Category: CyberSecurityNews
Threat actors hijack routers to gain unauthorized access to network traffic. This enables them to monitor, manipulate, or intercept sensitive…
A new threat activity has been discovered that relates to the Iran-Nexus espionage activity that targets Aerospace, Aviation, and defense…
A critical vulnerability has been discovered in the LiteSpeed Cache plugin, a popular WordPress plugin installed on over 4 million…
Threat actors use weaponized PDF files to exploit software vulnerabilities, enabling them to execute malicious code on a target system. …
The Ann & Robert H. Lurie Children’s Hospital of Chicago was recently hit by a highly advanced ransomware attack, underlining…
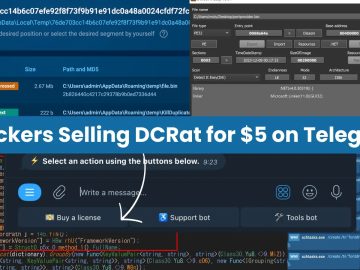
Recently, the cybersecurity researchers at ANY.RUN identified that hackers are selling DCRat subscriptions for $5 on the Telegram groups. Hackers…
Hackers poison the SEO results to manipulate search engine rankings by misdirecting users to malicious sites. They aim to take…
The notorious ransomware group LockBit has re-emerged on the dark web, signaling a swift comeback less than a week after…
The newly updated Cybersecurity Framework (CSF 2.0) offers simplified cybersecurity guidance designed for everyone, from small nonprofits to large corporations….
In a seemingly impossible act, nearly 8000 domains were discovered to be compromised by threat actors for malicious scam campaigns…
In a groundbreaking advisory, cybersecurity agencies from the Five Eyes intelligence alliance have detailed the sophisticated tactics, techniques, and procedures…
A cybersecurity company data breach could be extremely damaging as it not only compromises sensitive client information but also corrupts…