Category: CyberSecurityNews
Cybersecurity is of critical concern for every company, no matter their headcount or yearly revenue; in fact, many hackers target…
The rise of malicious versions of LLMs, like dark variants of ChatGPT, is escalating cyber warfare by enabling more sophisticated…
A new malware has been reported to be distributed by threat actors, which is likely known to be a stealthy…
Fortinet has issued a warning regarding a critical out-of-bounds write vulnerability in FortiOS. Remote attackers can exploit this vulnerability to…
Customers of LastPass have been alerted of a fraudulent app on the Apple App Store that poses as the legitimate LastPass…
Volt Typhoon, the PRC state-sponsored threat actor, has been discovered to be compromising U.S. critical infrastructure for future crises in…
Chainalysis, a leading blockchain analysis firm, has recently released a report on ransomware payments revealing that they have skyrocketed to…
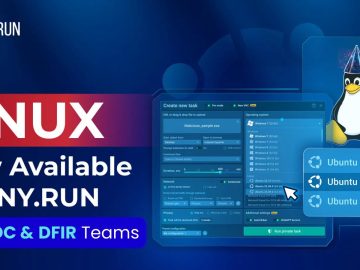
The ANY.RUN sandbox has recently undergone an update to include support for Linux, strengthening its capacity to offer a safe…
Spyware is a crucial tool for the surveillance and data collection of high-risk individuals. The functionalities of spyware have undergone…
Shim is a small application used by open-source projects and other third parties for verifying and running the bootloader (typically…
Chinese state-sponsored hackers exploited a zero-day vulnerability (CVE-2022-42475) in Fortinet’s virtual private network to gain unauthorized access to the Dutch…
FortiSIEM has been discovered with multiple OS command injection vulnerabilities, which could allow an unauthenticated remote threat actor to execute…