Category: CyberSecurityNews
Recently, Cluster25, a threat intelligence firm, uncovered a spear-phishing campaign dubbed “The Bear and the Shell,” specifically targeting entities critical…
Attackers continue to use compromised routers as malicious infrastructure to target government organizations in Europe and the Caucasus region. APT28…
With the increasing complexity and sophistication of malware, traditional signature-based detection technologies are insufficient. Next-generation malware analysis is a significant…
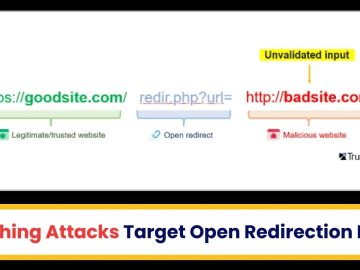
Attackers abuse trustworthy platforms for redirection, which involves the use of legitimate websites to redirect users to harmful URL destinations. In…
Aembit Becomes the First Workload IAM Platform to Integrate with the Industry-Leading CrowdStrike Falcon Platform to Drive Workload Conditional Access…
Funny videos, messages on social networks, hot topic news, and special offers are perfect baits for stealing your money and…
The recent discovery of a new DLL loader associated with the notorious Blackwood APT group has sent shivers down the…
A recent cyberattack on Orange España highlights the vulnerability of telecom network personnel and the critical need for improved digital…
With a CVSS score of 7.5, a high-severity IPv6 implementation issue in the Linux kernel identified as CVE-2023-6200 allowed attackers…
In an era where online threats no longer discriminate by business size, Control D, powered by Windscribe VPN‘s robust security…
On January 12, 2024, Microsoft identified a nation-state threat actor, “Midnight Blizzard,” attacking their corporate systems. Upon discovery, Microsoft deployed…
In an era where technology intertwines intricately with every facet of business operations, cybersecurity emerges as a buzzword and a…