Category: CyberSecurityNews
In a case that ignites the age-old debate between security concerns and ethical hacking, a German court has convicted a…
Bluetooth vulnerabilities in Android, Linux, macOS, iOS, and Windows are critical as hackers could exploit them to gain unauthorized access…
Threat actors target Apache Struts 2 due to vulnerabilities in its code that can be exploited for unauthorized access to…
Hackers exploit TeamViewer because it gives remote access to systems and allows threat actors to control them. This can be…
Since Apple iCloud saves sensitive and personal data like images, emails, and documents, hackers often target Apple iCloud. Breaching iCloud…
The incredible capabilities of LLM (Large Language Models) enable organizations to engage in various useful activities such as generating branding…
Recently, security analysts at ANY.RUN discovered that the Pure malware tools are masquerading as legitimate software to evade detection. ANY.RUN…
Hackers exploit Zero-Day flaws in VPNs as these vulnerabilities are unknown to the software vendor, making them difficult to patch…
An attacker may be able to steal a significant amount of data from a GPU’s memory due to a flaw…
Malware hunting on iOS devices has been extremely difficult due to the nature of the iOS ecosystem. There were only…
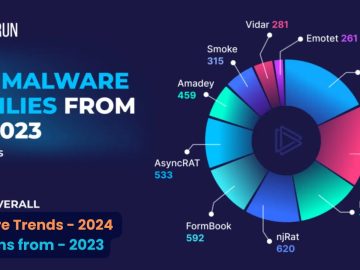
As the new year kicks off, it’s time to take a retrospective look at the past year’s malware landscape. Let’s…
Hackers frequently target researchers to get illegal access to important research data, intellectual property, and highly sensitive information. The threat…