Category: CyberSecurityNews
Russian hackers have been inside Ukrainian telecoms company Kyivstar’s system since at least May of last year, causing the most…
sIf you drive a smart car, its high-tech, internet-connected systems are likely monitoring your every move. Vehicles with these features…
The digital landscape, once a serene meadow, has morphed into a battleground where attackers and security vendors engage in a…
In the age of social media, verification badges hold significant power. On Twitter, the coveted blue tick (now replaced with…
Threat actors using the DLL Hijacking technique for persistence have been the order of the day and have been utilized…
The exploitation of crypto scams by hackers can be attributed to the inherent characteristics of cryptocurrencies that provide two critical…
SonicWall has made a strategic move in the evolving cybersecurity landscape, acquiring Banyan Security, a leading provider of identity-centric Secure…
Persistence is one of the key things for threat actors to maintain their access to compromised systems and establish connections…
Recently, Xerox’s US subsidiary, Xerox Business Solutions (XBS), experienced a cyber incident, prompting immediate action from Xerox’s cybersecurity personnel. While…
SentinelOne, the leading AI-powered security company, has made a significant move in the cloud security landscape by acquiring PingSafe, a…
Previously, in December 2023, it was reported that SSH servers were vulnerable to the new Terrapin Attack in which threat…
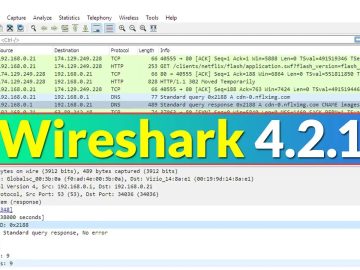
A free and open-source packet analyzer, Wireshark is used for network troubleshooting, education, software and communications protocol development, and analysis. …