Category: CyberSecurityNews
Baltimore, USA, November 4th, 2025, CyberNewsWire The new 2025 Insider Risk Report, produced by Cybersecurity Insiders in collaboration with Cogility,…
Hackers have successfully stolen more than $100 million by exploiting a critical vulnerability in the Balancer protocol. Balancer, a leading…
Delaware, United States, November 4th, 2025, CyberNewsWire Brinker, the narrative intelligence company dedicated to combating disinformation and influence campaigns, announced…
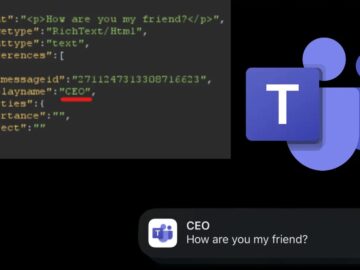
Critical vulnerabilities in Microsoft Teams, a platform central to workplace communication for over 320 million users worldwide, enable attackers to…
Microsoft is implementing a significant security enhancement to its Authenticator app, introducing automatic detection of jailbroken and rooted devices for…
Zscaler, a leading cloud security company, has announced the acquisition of SPLX, an innovative AI security firm, to enhance its…
Cybercriminals have shifted their focus to a highly profitable target: the trucking and logistics industry. Over the past several months,…
Google has issued a critical security alert for Android devices, highlighting a severe zero-click vulnerability in the system’s core components…
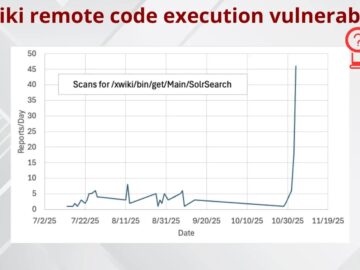
A critical remote code execution vulnerability affecting XWiki’s SolrSearch component has become the target of widespread exploitation attempts, prompting cybersecurity…
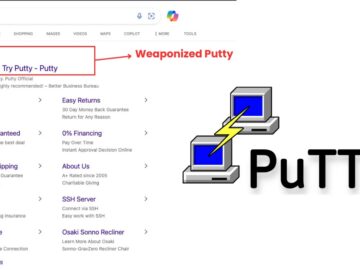
An ongoing malicious advertising campaign is weaponizing legitimate software downloads to deploy OysterLoader malware, previously identified as Broomstick and CleanUpLoader….
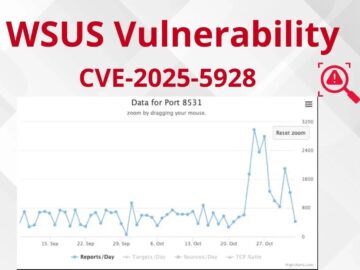
Cybersecurity researchers and firewall monitoring services have detected a dramatic surge in reconnaissance activity targeting Windows Server Update Services (WSUS)…
AMD has disclosed a critical vulnerability affecting its Zen 5 processor lineup that compromises the reliability of random number generation,…