Category: CyberSecurityNews
The Industrial control systems (ICS) security teams are actively fighting against a worm that is breaching and compromising the defense…
On June 21, 2023, hackers broke into LetMeSpy’s servers and stole private data. Following the hack, the attackers were able…
The Threat and Vulnerability Roundup for this week is out! With great pride, Cyber Writes presents a weekly overview of…
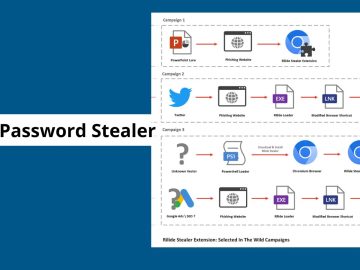
As per reports, a new version of the Rilide stealer is known to be stealing credentials from enterprise employees and…
Hackers actively leverage LOLBAS (Living-Off-the-Land Binaries-And-Scripts), it’s a popular methodology that is used by threat actors for exploiting legit tools…
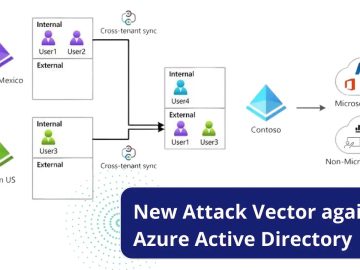
According to reports, the threat group known as “Nobelium” who were responsible for the SolarWinds attacks is now discovered to…
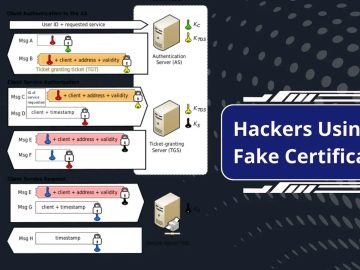
Using fake certificates, attackers gain unauthorized access to corporate network resources. Attackers use such certificates to trick the Key Distribution…
Threat actors are evolving their techniques and tools at a rapid pace that is completely changing the current threat scenario….
There is a critical vulnerability in Ivanti’s MobileIron Core 11.2 version that could allow a malicious actor to gain unauthorized…
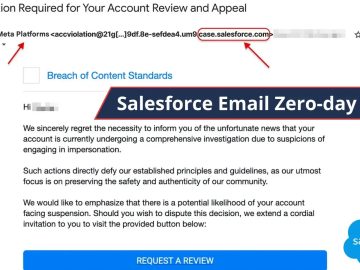
Hackers exploited a zero-day vulnerability in the email services and SMTP servers of Salesforce. Malicious email traffic is often concealed…
Google has published a security update for Chrome, updating the Stable channel for Mac and Linux to 115.0.5790.170 and 115.0.5790.170/.171 for…
Microsoft Threat intelligence identifies Midnight Blizzard (previously tracked as NOBELIUM) as a highly targeted social engineering attack. The attacker uses…