Category: CyberSecurityNews
Chinese-affiliated threat actor UNC6384 has been actively leveraging a critical Windows shortcut vulnerability to target European diplomatic entities across Hungary,…
Sophisticated threat actors have orchestrated a coordinated multilingual phishing campaign targeting financial and government organizations across East and Southeast Asia….
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning about a severe injection vulnerability in the…
In an unprecedented cybersecurity incident that occurred in September 2025, over 500 gigabytes of internal data from China’s Great Firewall…
WhatsApp has unveiled passkey-encrypted backups, simplifying the protection of cherished chat histories without the burden of memorizing complex passwords. This…
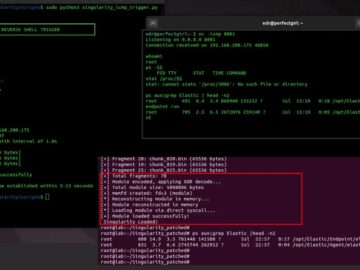
A sophisticated Linux kernel rootkit designed to slip past the defenses of Elastic Security, a leading endpoint detection and response…
The Cybersecurity and Infrastructure Security Agency (CISA) has added CVE-2025-41244 to its Known Exploited Vulnerabilities catalog. This local privilege escalation…
A newly discovered Windows malware family named Airstalk has emerged as a sophisticated threat capable of exfiltrating sensitive browser credentials…
A new agent-aware cloaking technique uses AI browsers like OpenAI’s ChatGPT Atlas to deliver misleading content. This method allows malicious…
Researchers have uncovered a sophisticated campaign leveraging the Lampion banking trojan, a malware strain that has operated since 2019 with…
A sophisticated malware campaign exploiting Near Field Communication technology on Android devices has expanded dramatically since its emergence in April…
The cybersecurity landscape faced a critical threat in early October 2025 with the public disclosure of RediShell, a severe use-after-free…