Category: CyberSecurityNews
Cyble Research & Intelligence Labs (CRIL) discovered a brand-new malware variant called “Rhadamanthys Stealer.” This malware stealer variation is now…
It has been reported that a group or individual, whose identity is currently unknown, has released a new “backdoor.” This…
The consumer VPN market has seen explosive growth in the last few years due to the increasing popularity of VPN…
Digital certificates are electronic credential that binds the identity to the owner of the certificate which can also pair the…
In a recent incident, within just 24 hours of initial access, the IcedID (aka BokBot) malware was used to successfully…
Kerberos authentication is a cryptography-based protocol that is used to secure logins. The Kerberos is a mythological three-headed Greek creature….
Twitter Inc. undertook a thorough investigation in response to recent media claims that the data of 200M Twitter users were…
An incident involving a cyber attack has caused severe service disruptions at Royal Mail, the British postal service and courier…
Trend Micro researchers recently reported that Australian healthcare entities were infected with a Cobalt Strike beacon after a new SEO…
The official AnyDesk website is being impersonated using more than 1,300 domains, all of which are linking to a Dropbox…
During the course of investigating the popular open-source project JsonWebToken, Unit 42 researchers discovered a new vulnerability. The cybersecurity analysts…
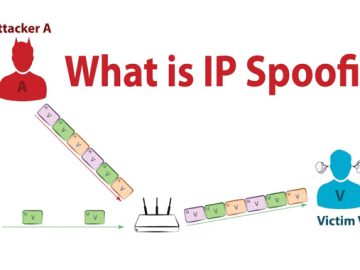
Spoofing is a malicious practice that disguising as a legitimate source to gain sensitive information, or to gain access to…