Category: CyberSecurityNews
A newly discovered ransomware-as-a-service platform called Gentlemen’s RaaS has recently emerged on underground hacking forums, offering threat actors a sophisticated…
Microsoft reported a DNS-related outage on October 29, 2025, affecting access to key services, including Microsoft Azure and Microsoft 365….
A groundbreaking security vulnerability has emerged that fundamentally challenges the integrity of modern trusted execution environments across Intel and AMD…
A new open-source tool called HikvisionExploiter has emerged, designed to automate attacks on vulnerable Hikvision IP cameras. Released on GitHub…
The npm ecosystem faces a sophisticated new threat as ten malicious packages have emerged, each designed to automatically execute during…
A public exploit code demonstrating how attackers could exploit CVE-2025-40778, a critical vulnerability in BIND 9 that enables DNS cache…
Microsoft Exchange servers in Germany are still running without security updates, just weeks after the official end of support for…
Google has announced a significant security initiative that will fundamentally change how Chrome handles unsecured web connections. Beginning with Chrome…
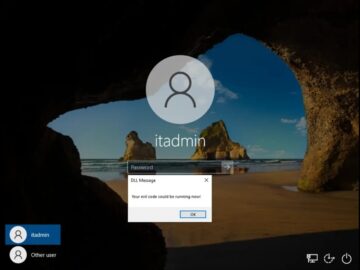
A persistent vulnerability related to DLL hijacking has been identified in the Narrator accessibility tool, which has been a significant…
A persistent vulnerability related to DLL hijacking has been identified in the Narrator accessibility tool, which has been a significant…
The Beast ransomware group has emerged as a significant threat in the cybersecurity landscape, evolving from the Monster ransomware strain…
CISA has added two critical vulnerabilities affecting Dassault Systèmes DELMIA Apriso to its Known Exploited Vulnerabilities catalog, warning that threat…