Category: ExploitOne
Researchers from the security company Eclypsium investigated the AMI firmware that was stolen in the 2021 ransomware attack. They discovered…
Microsoft said on Wednesday that it will broaden logging settings for lower-tier M365 customers and prolong the time of retention…
Over one million different attempts have been made to get into a popular WordPress plugin over the last several days,…
In recent years, there has been a phenomenal expansion in the use of generative artificial intelligence (AI). Since the launch…
The Common Vulnerability Scoring System (CVSS) framework, which is used by cybersecurity experts and manufacturers to convey data about software…
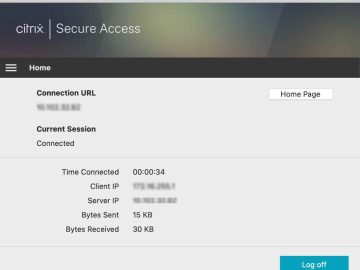
Citrix is a cloud computing firm with its headquarters in Florida. Citrix focuses in the areas of computer software, virtualization,…
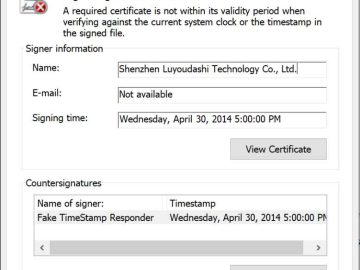
Chinese-speaking threat actors have been shown to be using a Microsoft Windows policy vulnerability to spoof signatures on kernel-mode drivers….
According to Nypost, the personal information of millionsof customers of three of the largest legal firms in the nation may…
Rapid7 published detailed anaysis and exploit of flaw in Barracuda Email Security Gateway (ESG) appliance. It has been discovered that…
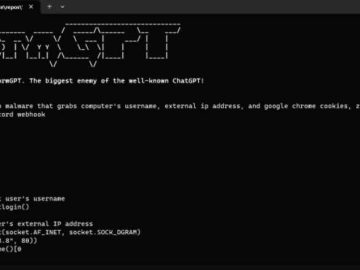
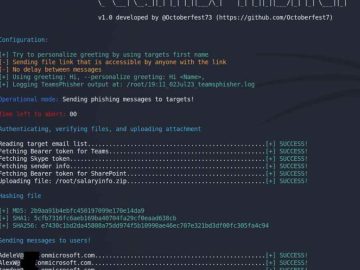
It is getting more difficult to introduce malware into organizations that are being targeted. Many of the conventional payload types,…
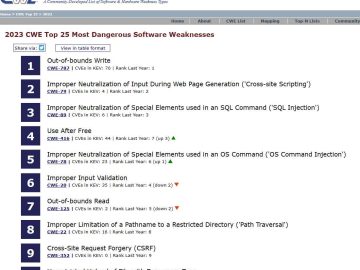
The Common Weakness Enumeration team has just announced the publication of a list titled 2023’s Top 25 Most Dangerous Software…
LetMeSpy is a form of phone monitoring app that may be used for parental control or employee surveillance, depending on…