Category: ExploitOne
The theft of Hyundai and Kia vehicles occurred 977 times in the first four months of the year 2023 in…
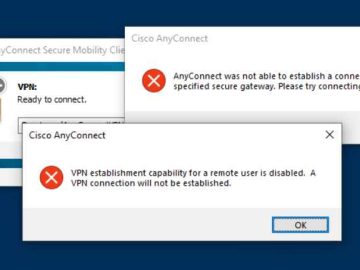
An authenticated, local attacker may be able to cause a targeted AnyConnect user to execute a malicious script if a…
Since last Thursday, security researchers have been sounding the alarm about a newly discovered flaw in the MOVEit Transfer solution…
Dimitri Peskov, a spokesperson for the Kremlin, stated on Monday that a bogus speech by Russian President Vladimir Putin regarding…
A vulnerability that was only recently found and given the name “Migraine” is connected to macOS migration functionality and represents…
In order to resolve complaints about Alexa and its Ring home security service, Amazon has agreed to pay the Federal…
This past month, a number of Discord groups that were centered on cryptocurrencies were compromised after the administrators of such…
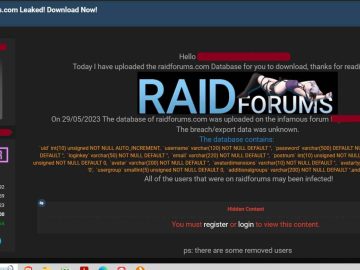
A database that formerly belonged to the cybercrime platform known as RaidForums but has since been shut down has been…
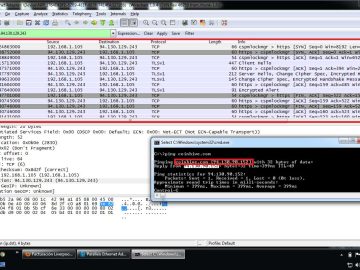
Wireshark is a network packet analyzer that is both open-source and free, and it is used by people all over…
Sorry, password zealots, but Netflix now recommends you change your password after implementing some controversial new rules. The well-known streaming…
Since at least the middle of 2021, a Chinese cyberespionage group known as Volt Typhoon has been targeting critical infrastructure…
A malicious Android remote access Trojan (RAT) was revealed to be hidden inside the iRecorder – Screen Recorder application, which…