Category: ExploitOne
T-Mobile USA has started alerting customers whose personal information and account data may have been exposed as a consequence of…
In the mostly uncontrolled realm of cryptocurrencies, hacking must not be a relatively rare occurrence, right? Hackers have been successful in…
Both protecting your privacy and keeping your safety are now of the utmost importance. It is not simply the responsibility…
Minecraft is a well-known video game that may be enjoyed either on a personal computer or on a mobile device….
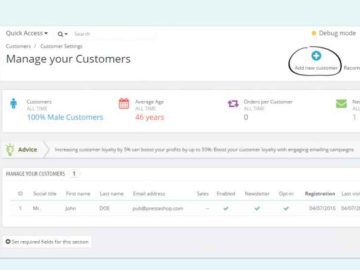
The fast-paced modern world has made online shopping and selling an essential component of our everyday life. PrestaShop has distinguished…
Service Location Protocol (SLP) is an older Internet protocol that has been found to contain a critical security flaw, which…
According to an article published by the Daily Mail, Google monitors the surfing activity of users on their devices by…
The Security Research Group at Astrix discovered a zero-day vulnerability in Google’s Cloud Platform (GCP), which means that all Google…
Cisco Industrial Network Director (IND) is an important tool for managing industrial networks, particularly in settings that need high-security standards….
The Mobile Research Team at McAfee came upon a software library that they have dubbed Goldoson. Goldoson compiles lists of…
Within the Linux kernel, a security flaw that has been given the identifier CVE-2023-2002 has been discovered; this flaw poses…
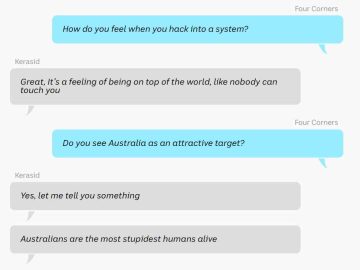
As he reveals how cyber gangs attack people and organizations with no guilt, a hacker believes that Australians are the…