Category: ExploitOne
Over the last two decades, the digital revolution has done nothing less than significantly improve the accessibility of information and…
CVE-2023-1281 and CVE-2023-1829 are two serious vulnerabilities that have been discovered in the Linux kernel. Both vulnerabilities have the potential…
Patch Tuesday for the month of April 2023 has here, and with it comes a torrent of new security updates…
A few days ago, we told you about the development of a YouTube scam that had everything: cryptocurrency fraud, the…
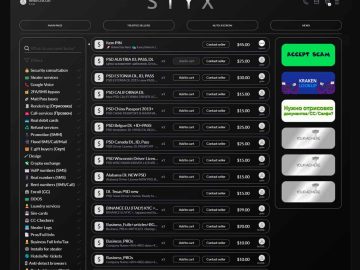
It was only recently revealed that the well-known Dark Web marketplace Genesis’s Clearnet site was taken over by authorities. Now,…
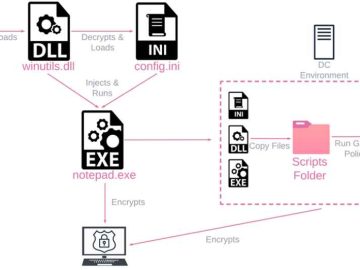
Researchers at the Israeli cybersecurity firm Check Point have given the new ransomware the name “Rorschach.” They said that their…
Due to a number of security flaws that a certain type of smart garage door opener controllers, named Nexx, has,…
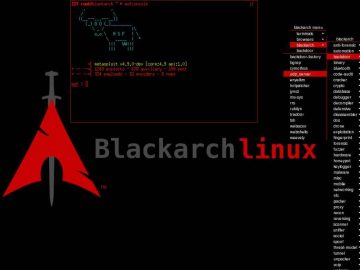
When it comes to Linux distributions, we have access to a large number of different alternatives to choose from. BlackArch…
Large-scale preparations by Russian military and intelligence services to use their cyberwar capabilities in misinformation campaigns, hacking operations, critical infrastructure…
A vulnerability that might compromise the security of millions of Microsoft 365 accounts was found earlier this year. Researchers at…
The malware was given the name Mélofée by the French cybersecurity company ExaTrack after they discovered three instances of the…
In just a few short months, ChatGPT has established itself as an indispensable resource for millions of users. This artificial…