Category: ExploitOne
On Tuesday, the OpenSSL Project released a significant security update in order to address at least eight identified security weaknesses….
The Linux kernel has a framework known as netfilter that enables a variety of networking-related actions to be performed in…
Ubiquiti Networks, a technological company that had its headquarters in New York, that produced and marketed equipment related to wireless…
Certification in cybersecurity is often required for employment in the cybersecurity sector, and common examples of such certifications include those…
Imagine that you get an email from DocuSign, which is a reputable and well-known electronic signature platform. If you clicked…
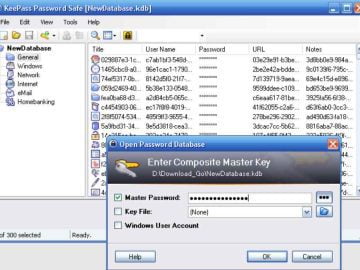
KeePass is a widely used open-source password manager that enables you to manage your passwords by using a database that…
My Cloud from Western Digital is one of the most popular network-attached storage (NAS) devices that are being used by…
A Yandex source code repository that was apparently taken by an ex-worker of the Russian IT giant has been published…
On Tuesday, January 24, many news organizations claimed that the SAT site had been hacked. In response to these reports,…
During the fourth quarter of 2022, Yahoo was the target of twenty percent of all brand phishing attempts. Investigators discovered…
The security of Zendesk, a company that provides customer care solutions, was breached on October 25, 2022 as a direct…
Internet Protocol (IP) is the protocol that the vast majority of networked devices use in order to communicate. IP version…