Category: ExploitOne
Multiple vulnerabilities have been found in the fingerprint sensors of Dell Inspiron 15, Lenovo ThinkPad T14, and Microsoft Surface Pro…
The U.S. Securities and Exchange Commission (SEC) has guidelines and rules that relate to how publicly traded companies must handle…
In a startling revelation, ChatGPT, the advanced AI chatbot developed by OpenAI, has been found to have a significant security…
CVE-2023-22515 and CVE-2023-22518 are critical vulnerabilities found in Atlassian Confluence, a widely used team collaboration software. CVE-2023-22515 Description: This vulnerability…
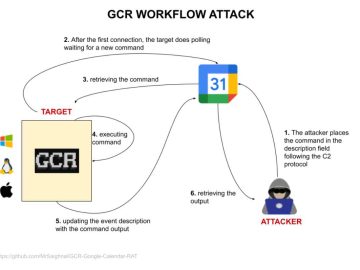
Google has warned about a method by which hackers could exploit its Calendar service to create a covert Command-and-Control (C2)…
RSA-2048 is a widely used encryption scheme based on the RSA (Rivest–Shamir–Adleman) cryptosystem. The “2048” in RSA-2048 denotes the key…
It would seem that the global leader in aerospace, Boeing, is the most recent victim of the ransomware gang known…
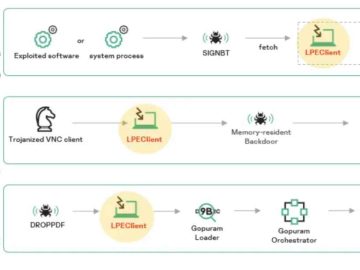
In recent weeks, the renowned Lazarus gang, which acts as a cyber threat actor, has been more active than usual,…
The Seiko Group, known for its timekeeping business, suffered a ransomware attack in July 2023 that led to the theft…
The Spanish National Police have successfully dismantled a sophisticated cybercriminal organization, resulting in the arrest of 34 individuals. This organization…
The recent Casio hack has left a significant impact on the data security of individuals and organizations across 149 countries….
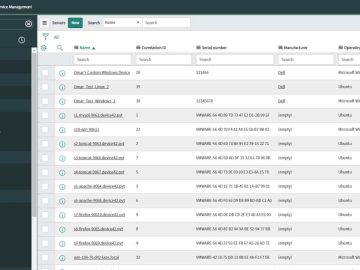
A vulnerability has been identified in the digital business platform known as ServiceNow, and this poses a significant risk to…