Category: ExploitOne
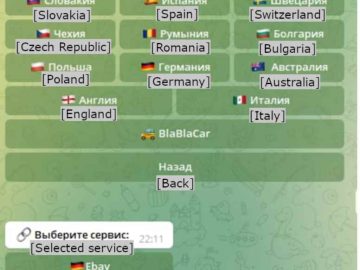
A recently launched enterprise driven by financial gain is using a malicious Telegram bot to assist threat actors in defrauding…
Both CloudNordic and AzeroCloud, two hosting services based in Denmark, have been hit by ransomware attacks, which have resulted in…
The Ecuadorian national election, which took place on Sunday, was hampered by problems with internet voting for residents residing outside…
Notification of a data breach was only recently made public by the well-known watch manufacturing business Seiko on August 20,…
An arbitrary code execution vulnerability was found in WinRAR, and it is possible to exploit this issue by opening a…
SMS Bomber attacks are becoming more prominent as a contemporary risk that has the potential to have substantial and unsettling…
This week, cleaning product manufacturer Clorox disclosed a cybersecurity issue that resulted in the company having to take a number…
A buffer overflow vulnerability was discovered not too long ago in the Wi-Fi driver that Ford employs in the SYNC…
Hackers in Belarus are focusing their attention on foreign embassies in the hopes of stealing papers, recording audio, and tracking…
The United Kingdom Electoral Commission, which is responsible for protecting voter information, recently had a complicated data breach, which resulted…
A recent investigation of acoustic side-channel attacks was carried out by a group of researchers drawn from a number of…
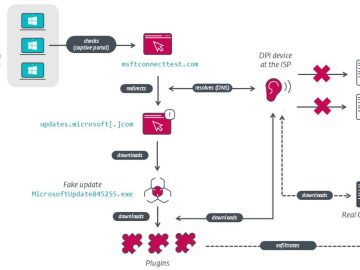
In comparison to the approaches that are now used, the detection capabilities of a typical internet attack have been much…