Category: ExploitOne
The threat actors associated with North Korea aggressively drew the attention of security specialists, exposing useful campaign insights during the…
The National Security Agency (NSA), the Federal Bureau of Investigation (FBI), and the Five Eyes (Five Eyes) from a variety…
The National Security Agency (NSA) has published best practices for setting and hardening Cisco Firepower Threat Defense (FTD). These best…
Amazon Web Services (AWS) has a novel post-exploitation approach that has been identified by researchers. This technique enables hackers to…
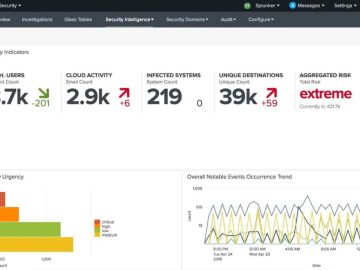
Splunk has found a vulnerability that enables unauthenticated log injection, which opens the door for hostile actors to execute dangerous…
According to a search warrant that was acquired by Forbes, the Pentagon is conducting an investigation into what it has…
In the month of May, both Google and Apple made the announcement that they were going to work together to…
The United States Securities and Exchange Commission (SEC) has approved new regulations that call for publicly-traded companies to report significant…
Cybercriminals have just released a new tool known as FraudGPT, which represents a significant risk to both private persons and…
According to the latest Cost of a Data Breach study from IBM, the worldwide average cost of a data breach…
The dangers posed by cybersecurity continue to advance, and processors are not exempt from this trend. CVE-2023-20593 is a severe…
The Cybersecurity and Infrastructure Security Agency (CISA) of the United States has issued a warning that threat actors attempted to…