Category: GBHackers
UK law enforcement agencies have arrested two individuals linked to the notorious Scattered Spider cybercriminal group. The arrests, announced on…
Silhouetted hooded figures represent Russian hackers operating under the auspices of the FSB against targeted organizations. Two prominent Russian state-sponsored…
Cyber threat actors have weaponized two critical Ivanti Endpoint Manager Mobile (EPMM) vulnerabilities—CVE-2025-4427 and CVE-2025-4428—to deploy sophisticated malicious loaders and…
Russian regional carrier KrasAvia is grappling with a major IT outage after what appears to be a cyberattack. Passengers have…
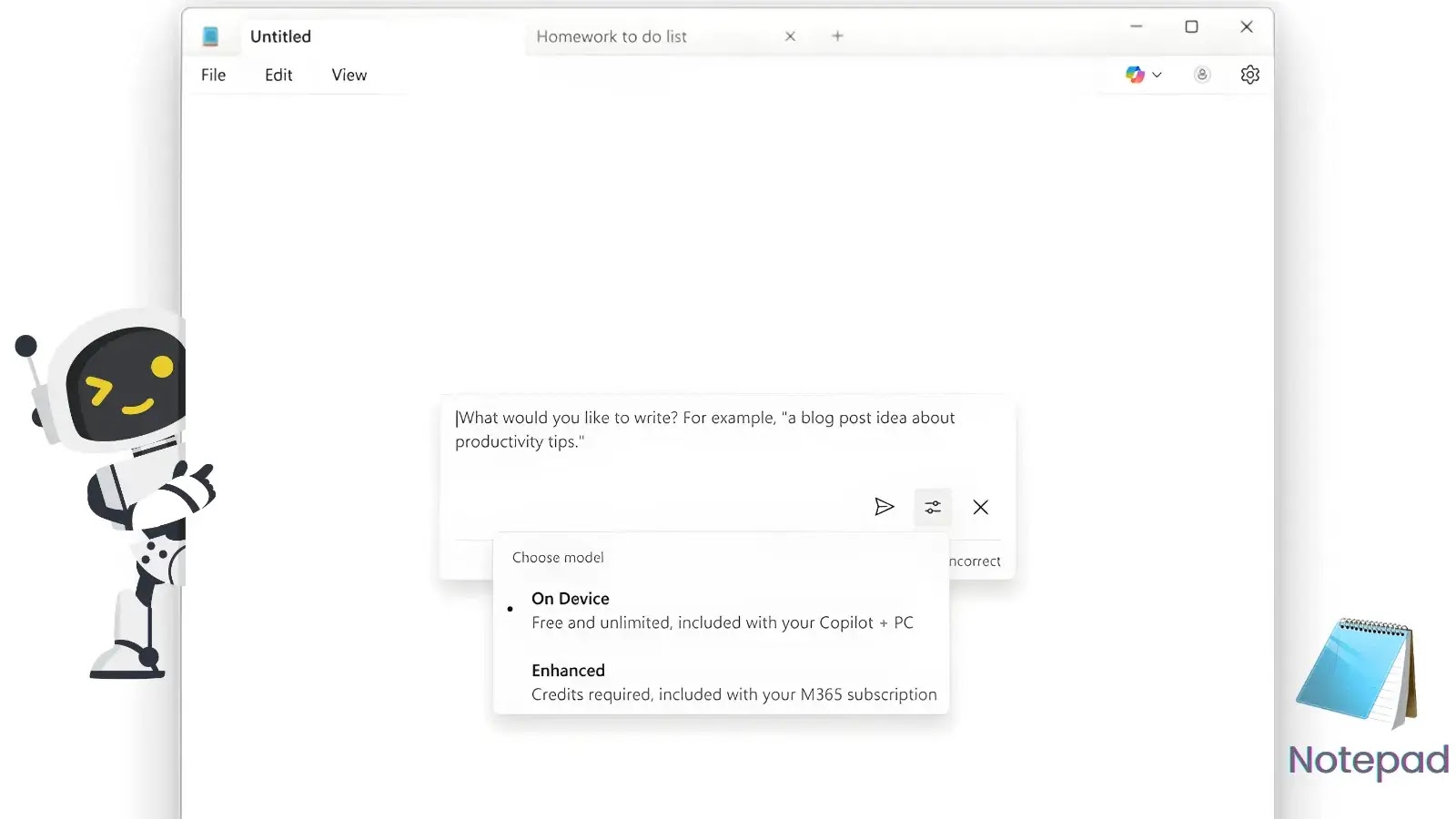
Microsoft has announced a significant upgrade to Windows 11 Notepad, introducing powerful artificial intelligence features that will revolutionize how users…
In a groundbreaking analysis, cybersecurity firm KELA reveals striking parallels in operational style, target selection, and online presence that suggest…
Cloudflare experienced a significant outage on September 12, 2025, affecting its Tenant Service API, multiple APIs, and the Cloudflare Dashboard….
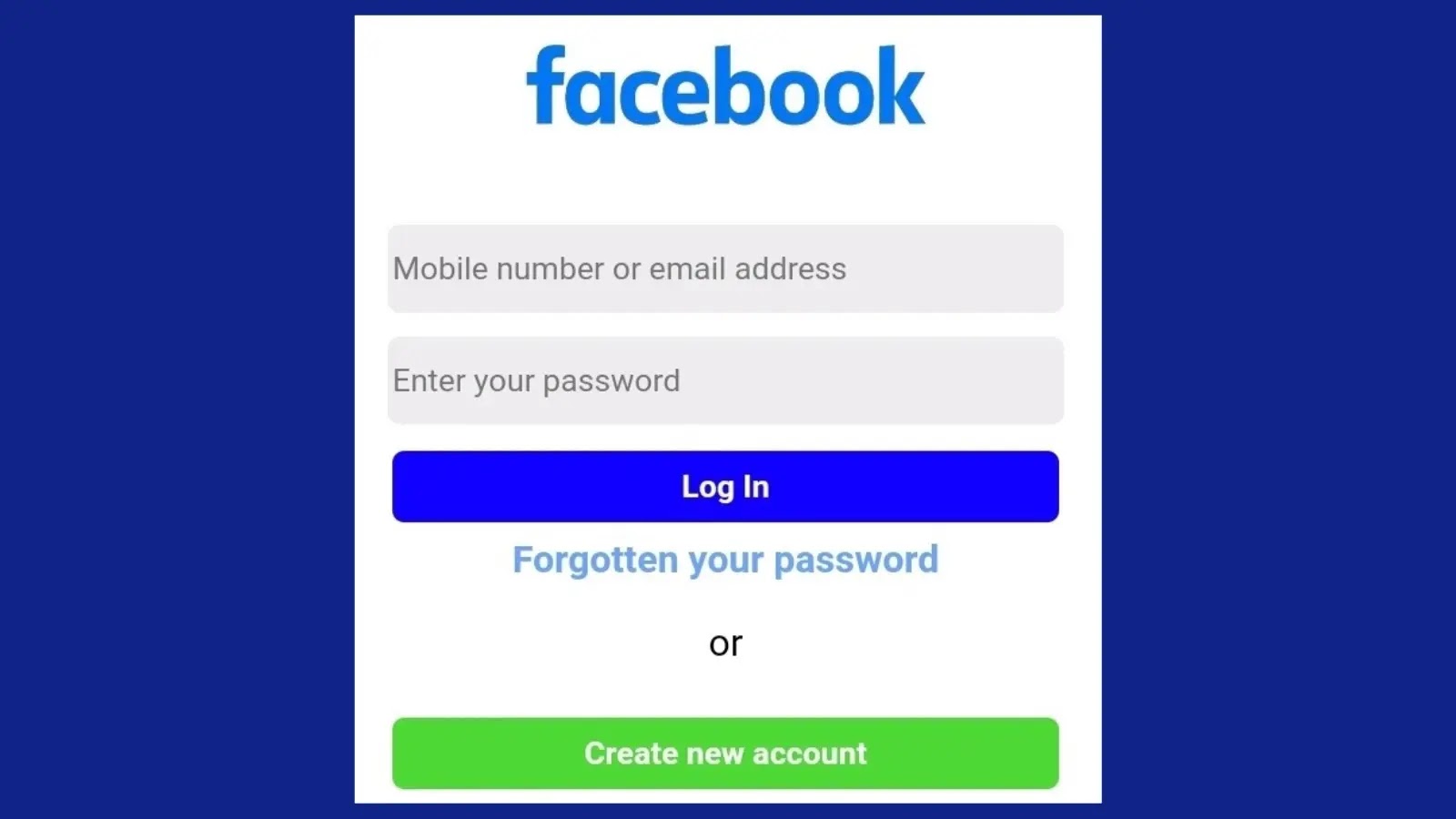
A newly discovered phishing campaign is exploiting Facebook’s external URL warning feature to dupe users into handing over their login…
SonicWall has alerted its customers to reset all login credentials after a recent leak exposed firewall configuration backups. The vendor…
Lurking in the murky depths of the global marketplace for offensive cyber capabilities sits a particularly dangerous instrument—spyware. Spyware’s danger…
EclecticIQ analysts assess with high confidence that ShinyHunters is expanding its operations by combining AI-enabled voice phishing, supply chain compromises,…
The Everest ransomware group has claimed a major breach at Bayerische Motoren Werke AG (BMW), alleging the theft of 600,000…