Category: GBHackers
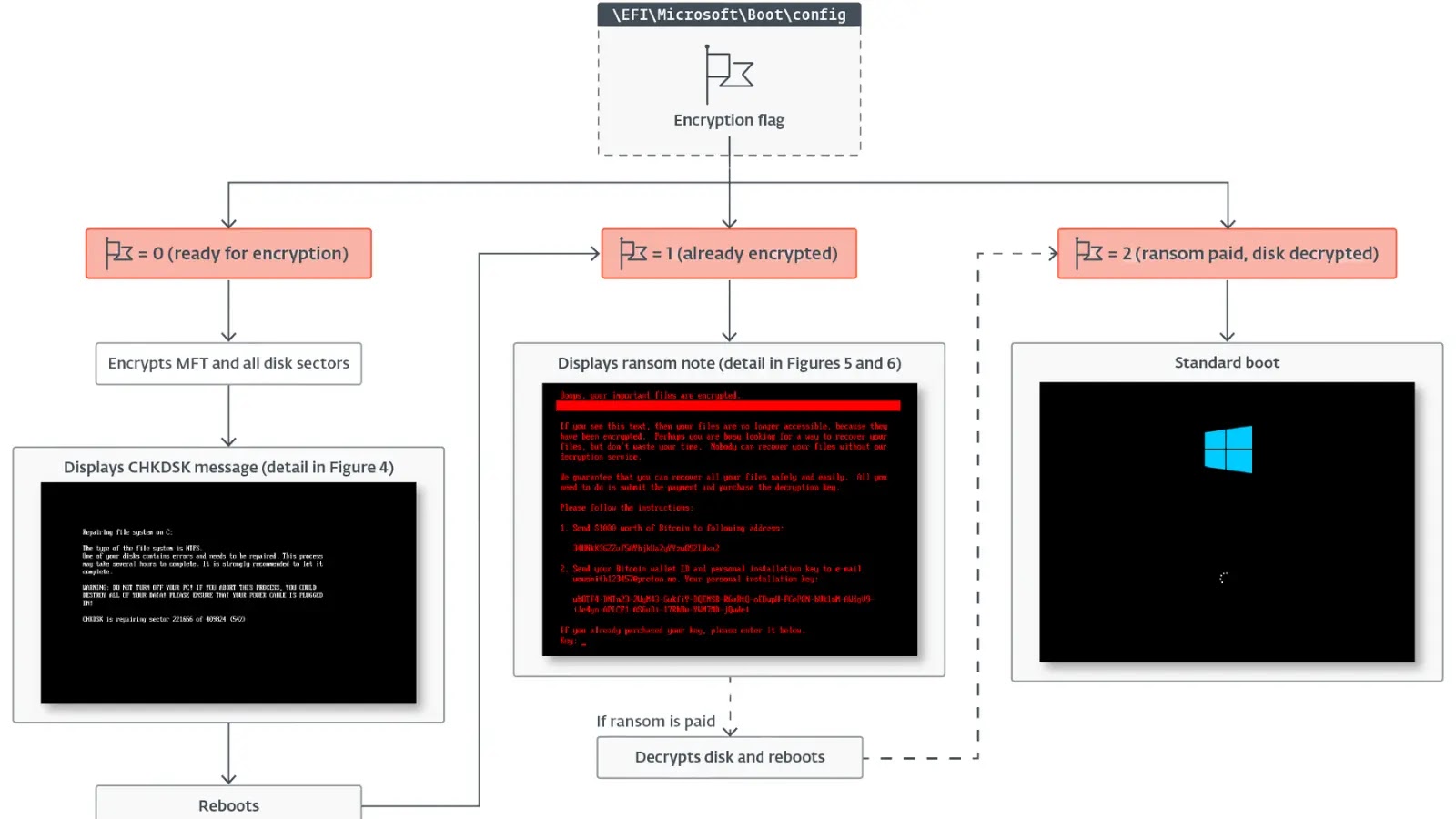
ESET Research has uncovered a sophisticated new ransomware variant called HybridPetya, discovered on the VirusTotal sample sharing platform. This malware…
Microsoft has released security advisories for four newly discovered vulnerabilities in its Windows Defender Firewall Service that could enable attackers…
A malicious ISO image named Servicenow-BNM-Verify.iso was uploaded to VirusTotal from Malaysia with almost no detections. The image contains four…
A sophisticated malvertising campaign has been uncovered targeting unsuspecting users through “dangling commits” in a legitimate GitHub repository. Attackers are…
A critical security vulnerability has been discovered in the popular Axios HTTP client library that allows attackers to crash Node.js…
Backdoor malware is a covert type of malicious software designed to bypass standard authentication mechanisms and provide persistent, unauthorized access…
Recent threat campaigns have revealed an evolving use of BAT-based loaders to deliver Remote Access Trojans (RATs), including XWorm and…
In a striking evolution of its tactics, the Sidewinder advanced persistent threat (APT) group—also known as APT-C-24 or “Rattlesnake”—has adopted…
Microsoft announced the phased deprecation of VBScript in Windows, significantly impacting VBA developers who rely on VBScript libraries for regular…
In a startling development on September 8, the Telegram channel “scattered LAPSUS$ hunters 4.0” declared its intention to “go dark”…
A groundbreaking vulnerability has emerged in the newly released K2 Think AI model from UAE’s Mohamed bin Zayed University of…
The latest ToneShell variant introduces a notable advancement in its persistence strategy by leveraging the Windows Task Scheduler COM service….