Category: GBHackers
A Chinese APT group compromised a Philippine military company using a new, fileless malware framework called EggStreme. This multi-stage toolset…
The threat actor delivers three Remote Access Trojans (RATs)—ValleyRAT, FatalRAT, and a newly discovered RAT dubbed kkRAT—via phishing sites hosted…
During a recent threat hunting exercise, the Sysdig Threat Research Team (TRT) identified a new sample dubbed ZynorRAT. This Go-based…
Spoof the email delivery platform SendGrid and employ fake Cloudflare CAPTCHA interstitials to lend legitimacy before redirecting unsuspecting users to…
A critical vulnerability in NVIDIA’s NVDebug tool could allow attackers to gain elevated system access, execute code, or tamper with…
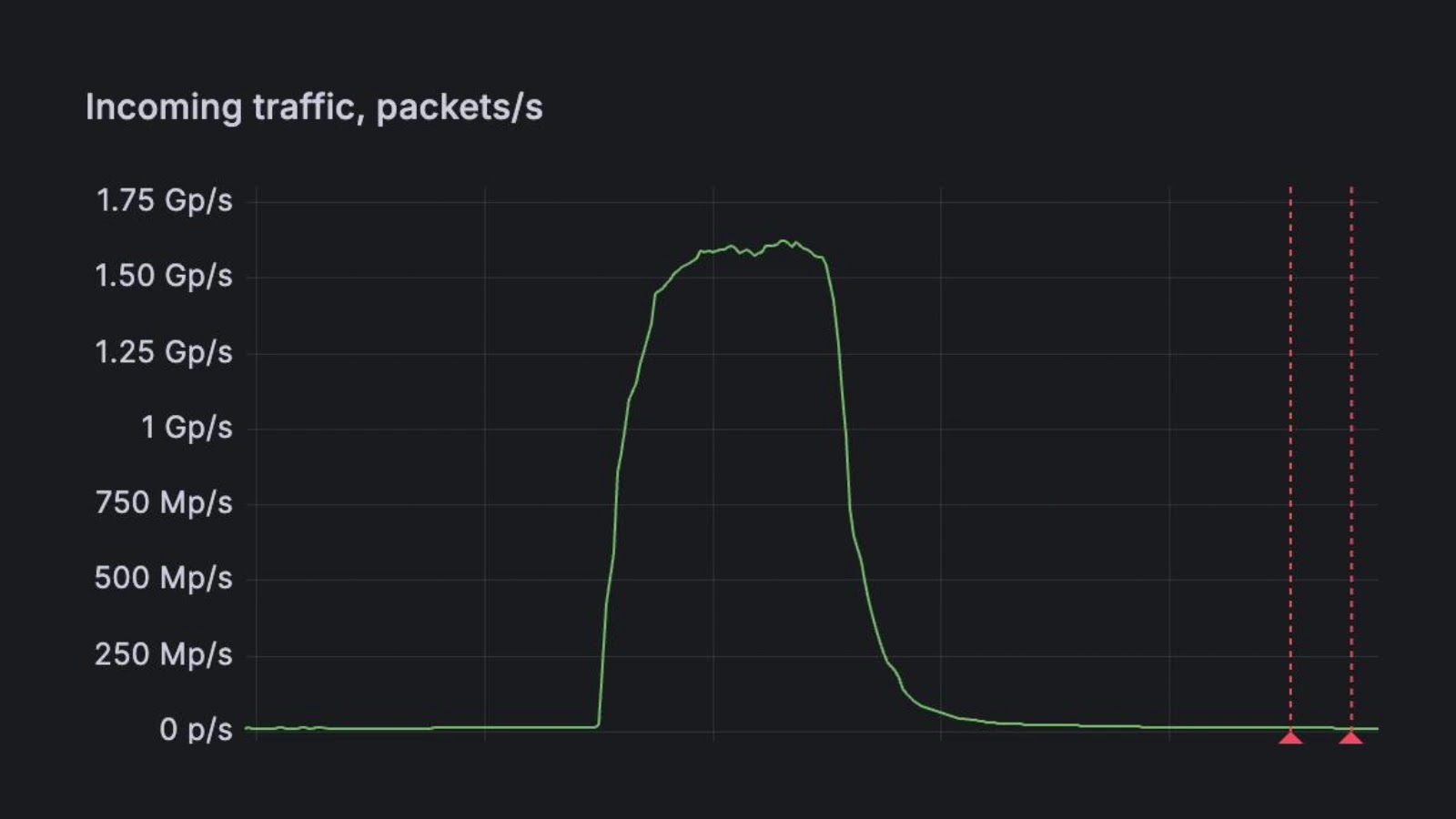
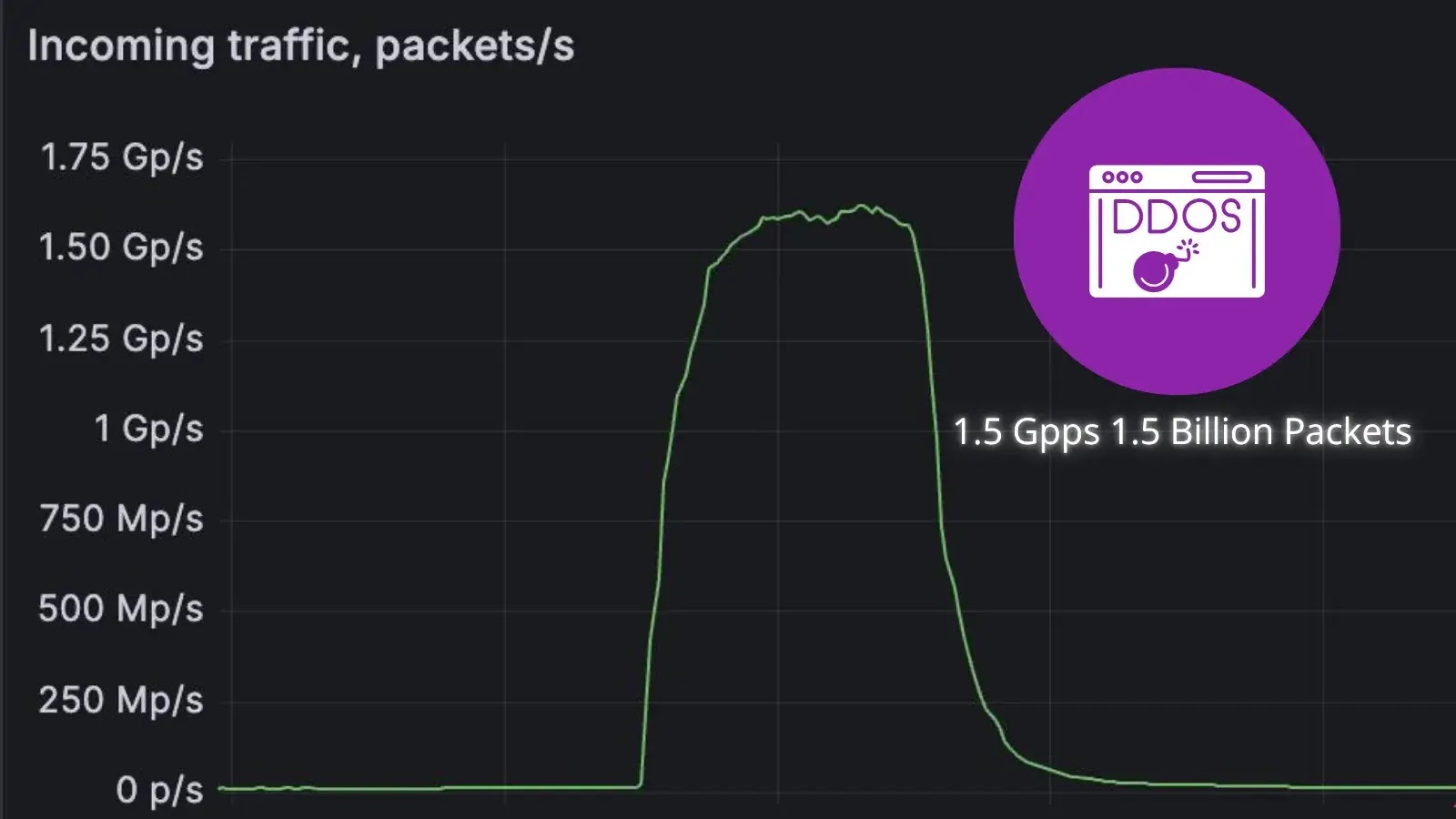
FastNetMon today announced that it detected a record-scale distributed denial-of-service (DDoS) attack targeting the website of a leading DDoS scrubbing vendor in…
FastNetMon today announced it detected a record-scale distributed denial-of-service (DDoS) attack targeting the website of a leading DDoS scrubbing vendor…
A new wave of macOS-targeted malware has emerged under the radar—despite employing advanced process reconnaissance and maintaining successful notarization status…
The Australian Cyber Security Centre (ACSC) has issued an urgent warning about a critical vulnerability in SonicWall firewall devices that…
On September 8th, 2025, at approximately 9AM EST, the npm ecosystem faced an acute supply chain attack. A threat actor…
HackerOne, a leading vulnerability coordination platform, has confirmed that its Salesforce environment was compromised in a recent third-party data breach….
KuCoin’s security team has uncovered a new phishing campaign orchestrated by the Lazarus Group (APT38), the notorious state-sponsored collective renowned…