Category: GBHackers
A sophisticated malware campaign is actively targeting WordPress e-commerce websites using the WooCommerce plugin, according to recent findings from the…
The VSCode extension marketplace has become a critical vulnerability in the software supply chain. Security researchers at HelixGuard Team recently…
A critical security flaw has been discovered in the Anti-Malware Security and Brute-Force Firewall WordPress plugin, putting more than 100,000…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent warning about active exploitation of a critical vulnerability affecting…
The global developer community has been rocked by the emergence of PhantomRaven, a far-reaching campaign involving 126 malicious npm packages…
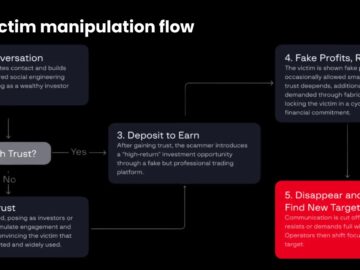
Fraudulent investment platforms impersonating legitimate cryptocurrency and forex exchanges have emerged as the primary financial threat across Asia, with organized…
Microsoft experienced a widespread service outage on Wednesday, October 29, 2025, affecting its Azure cloud platform and Microsoft 365 suite,…
A critical vulnerability discovered in Google Messages for Wear OS has exposed millions of smartwatch users to a significant security…
Tel Aviv, Israel, October 29th, 2025, CyberNewsWire Sweet Security Brings Runtime-CNAPP Power to Windows Sweet Security, a leader in Runtime…
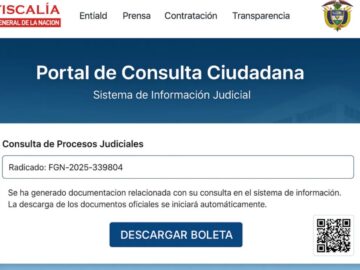
The campaign leverages judicial document themes to distribute Hijackloader malware, which subsequently deploys PureHVNC remote access trojan (RAT)—marking the first…
Google has released comprehensive guidance on protecting privileged accounts, recognizing that stolen credentials have become one of the most dangerous…
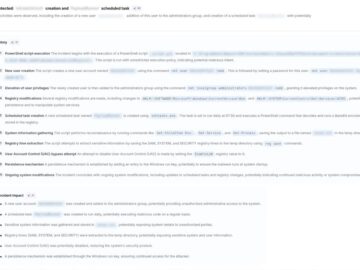
Russian-linked attackers have intensified their targeting of Ukrainian organizations through sophisticated intrusions that rely heavily on legitimate Windows tools rather…