Category: GBHackers
Microsoft has released a critical security update addressing a severe vulnerability in ASP.NET Core that could enable attackers to execute…
Active Directory domain join accounts are systematically exposing enterprise environments to compromise, even when administrators follow Microsoft’s official guidance. A…
A newly advertised information-stealing malware called Anivia Stealer has surfaced on the dark web, with threat actor ZeroTrace aggressively promoting…
Security researchers have discovered a sophisticated phishing technique that weaponizes invisible Unicode characters embedded within email subject lines using MIME…
The Brida security testing toolkit has released version 0.6, marking a significant update that brings full compatibility with the latest…
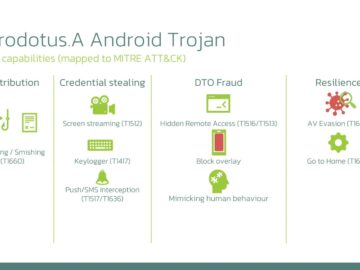
A sophisticated new Android banking Trojan named Herodotus has emerged as a significant threat to mobile users, introducing a novel…
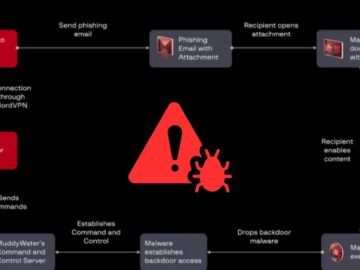
Advanced Persistent Threat (APT) MuddyWater has orchestrated a sophisticated phishing campaign targeting over 100 government entities across the Middle East,…
The IPFire project has announced the release of version 2.29, Core Update 198, marking a significant milestone in the open-source…
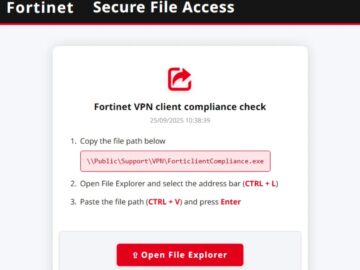
Cybersecurity researchers have uncovered a sophisticated evolution in phishing attacks that combines FileFix social engineering with cache smuggling techniques to…
Operant AI’s security research team has uncovered Shadow Escape, a dangerous zero-click attack that exploits the Model Context Protocol to…
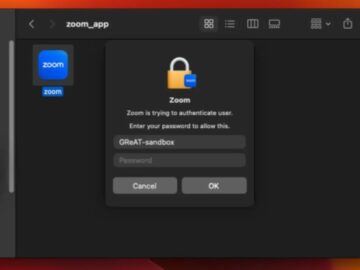
The North Korean-linked threat group BlueNoroff, also known by aliases including Sapphire Sleet, APT38, and Alluring Pisces, continues to evolve…
A sophisticated new Android malware family called GhostGrab is actively targeting mobile users with a dual-monetization strategy that combines covert…