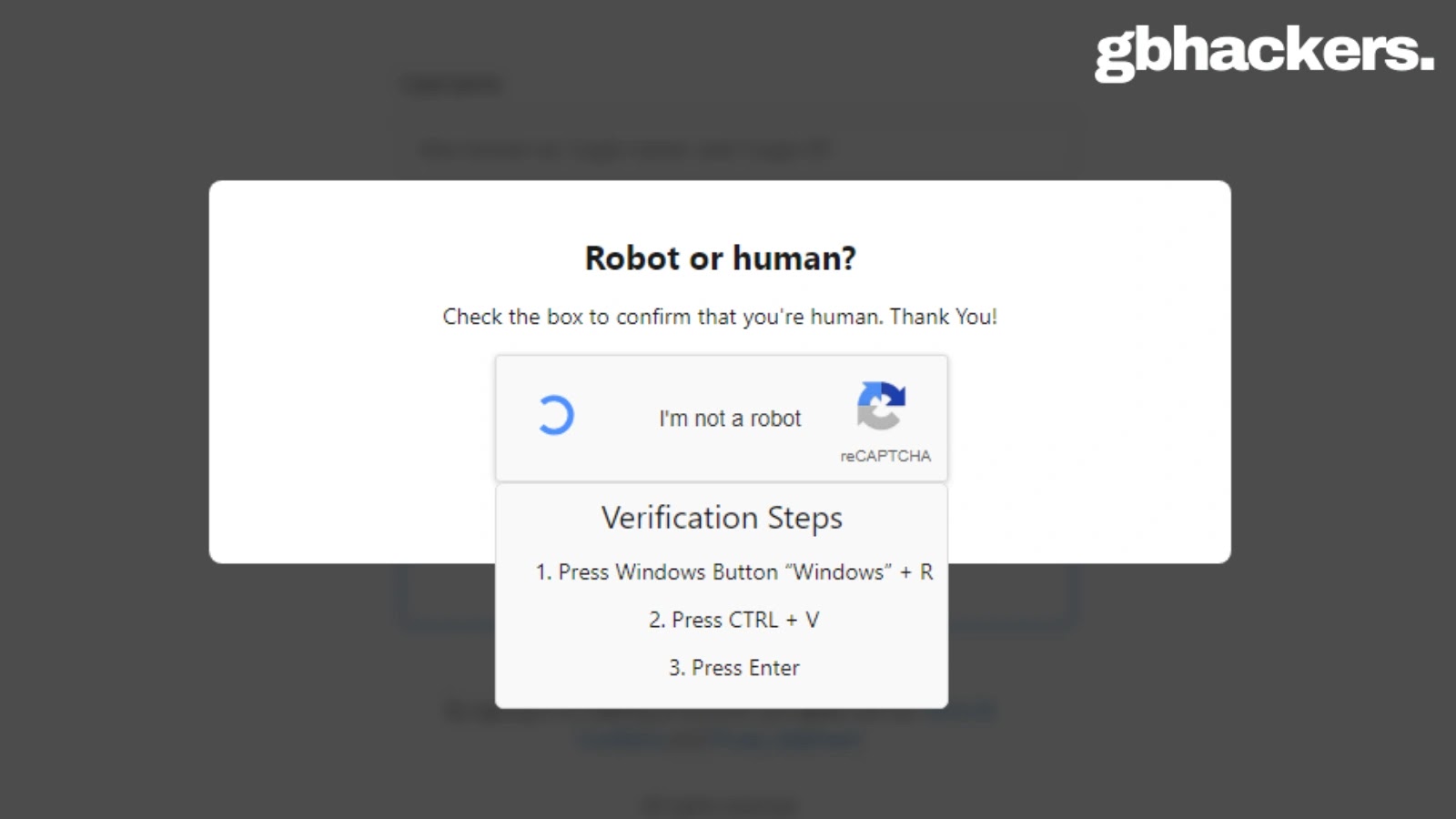
Category: GBHackers
HashiCorp has disclosed two critical vulnerabilities in Vault and Vault Enterprise that could enable attackers to bypass authentication mechanisms and…
A sophisticated cyber-sabotage group known as Predatory Sparrow has emerged as one of the most destructive threat actors targeting Iranian…
Famous Chollima, a DPRK-aligned threat group, has evolved its arsenal, with BeaverTail and OtterCookie increasingly merging functionalities to steal credentials…
In the latter half of 2025, the Qilin ransomware group has solidified its standing as a formidable threat, continuing to…
Security researchers at Datadog have uncovered a sophisticated phishing technique that weaponizes Microsoft Copilot Studio to conduct OAuth token theft…
Microsoft is preparing to introduce a groundbreaking feature in Teams that will revolutionise how hybrid workers manage their presence information….
Cybersecurity researchers from Team Z3 have withdrawn their planned demonstration of a zero-click remote code execution vulnerability in WhatsApp at…
A critical vulnerability affecting more than 706,000 BIND 9 DNS resolvers worldwide has been disclosed with proof-of-concept exploit code now…
Cybercriminals are increasingly using a technique known as “ClickFix” to deploy the NetSupport remote administration tool (RAT) for malicious purposes….
Cybersecurity firm Wordfence has uncovered a renewed wave of mass exploitation targeting critical vulnerabilities in two popular WordPress plugins, allowing…
Cybersecurity researchers are sounding the alarm after discovering that hackers are actively exploiting a critical remote code execution (RCE) vulnerability…
Gamers face a growing threat from cybercriminals exploiting popular gaming and communication platforms. A dangerous infostealer called RedTiger is now…