Category: GBHackers
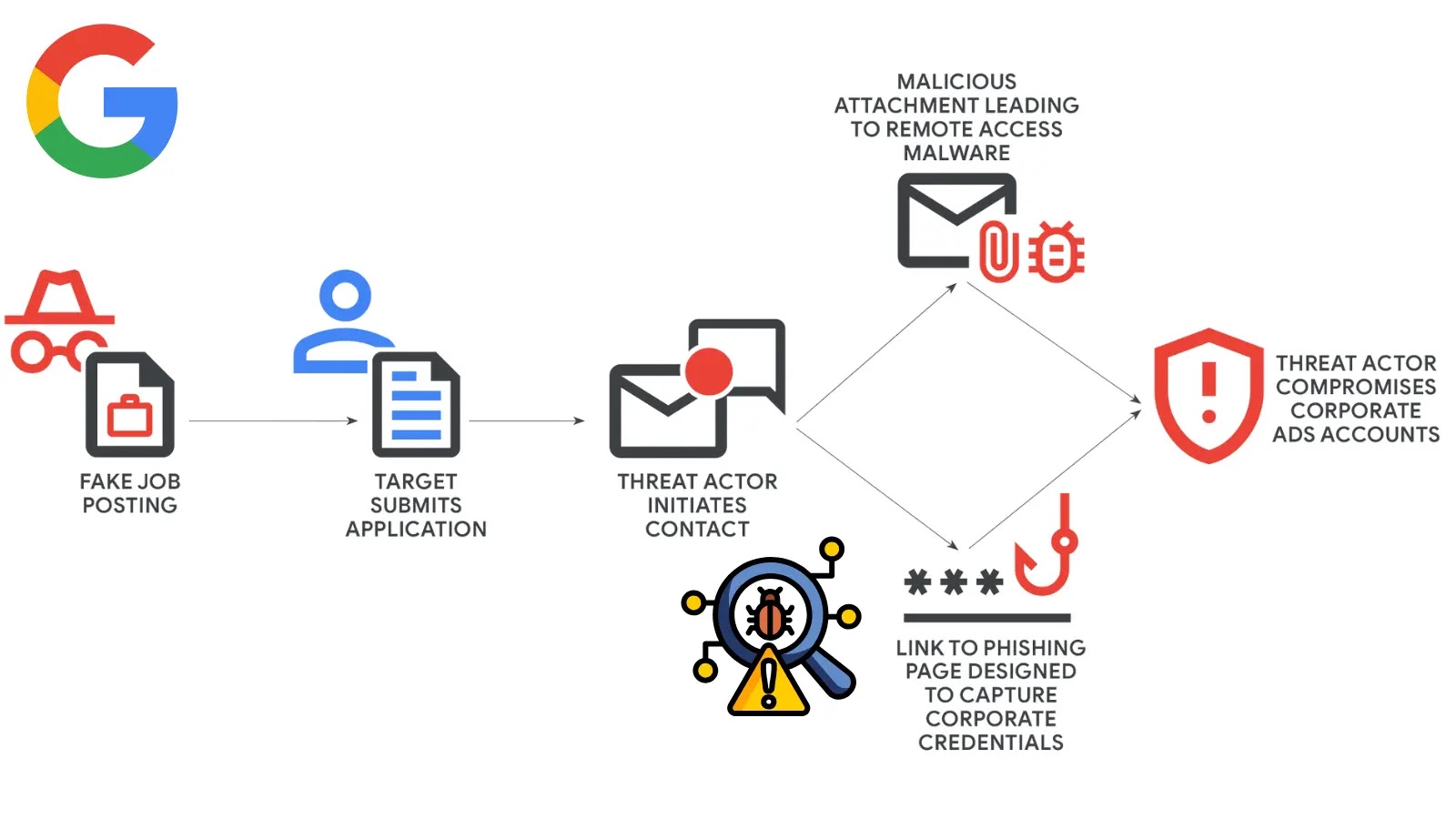
Google’s Threat Intelligence Group (GTIG) has uncovered a sophisticated social engineering campaign orchestrated by financially motivated threat actors based in…
After months of disruption following Operation Cronos in early 2024, the notorious LockBit ransomware group has resurfaced with renewed vigor…
Amazon Web Services experienced a major outage that affected millions of customers and Amazon’s own operations on October 19 and…
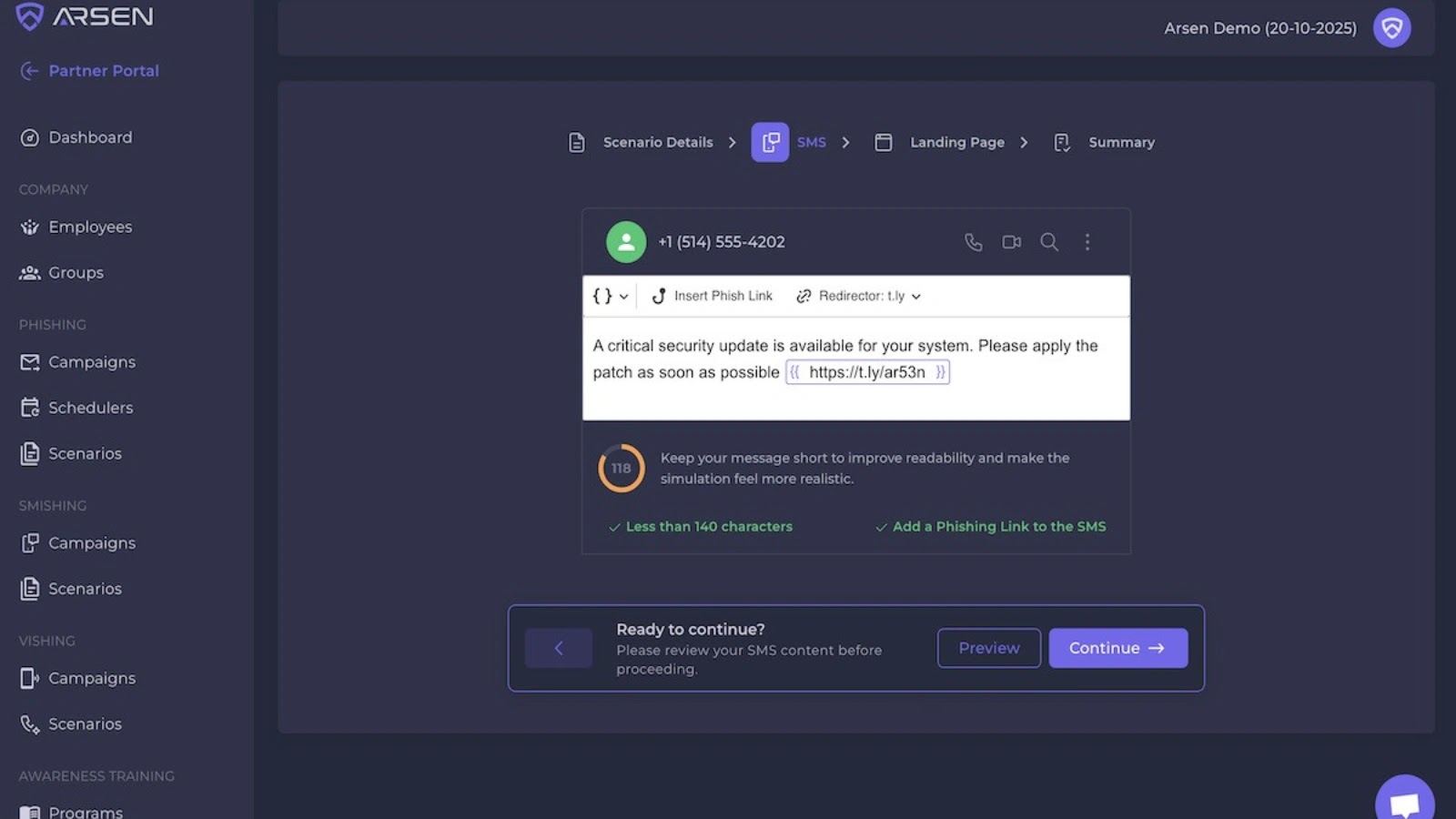
Paris, France, October 24th, 2025, CyberNewsWire Arsen, the cybersecurity company dedicated to helping organizations defend against social engineering, today introduced…
Security researchers at Doctor Web have uncovered a sophisticated Android backdoor disguised as Telegram X that grants cybercriminals complete control…
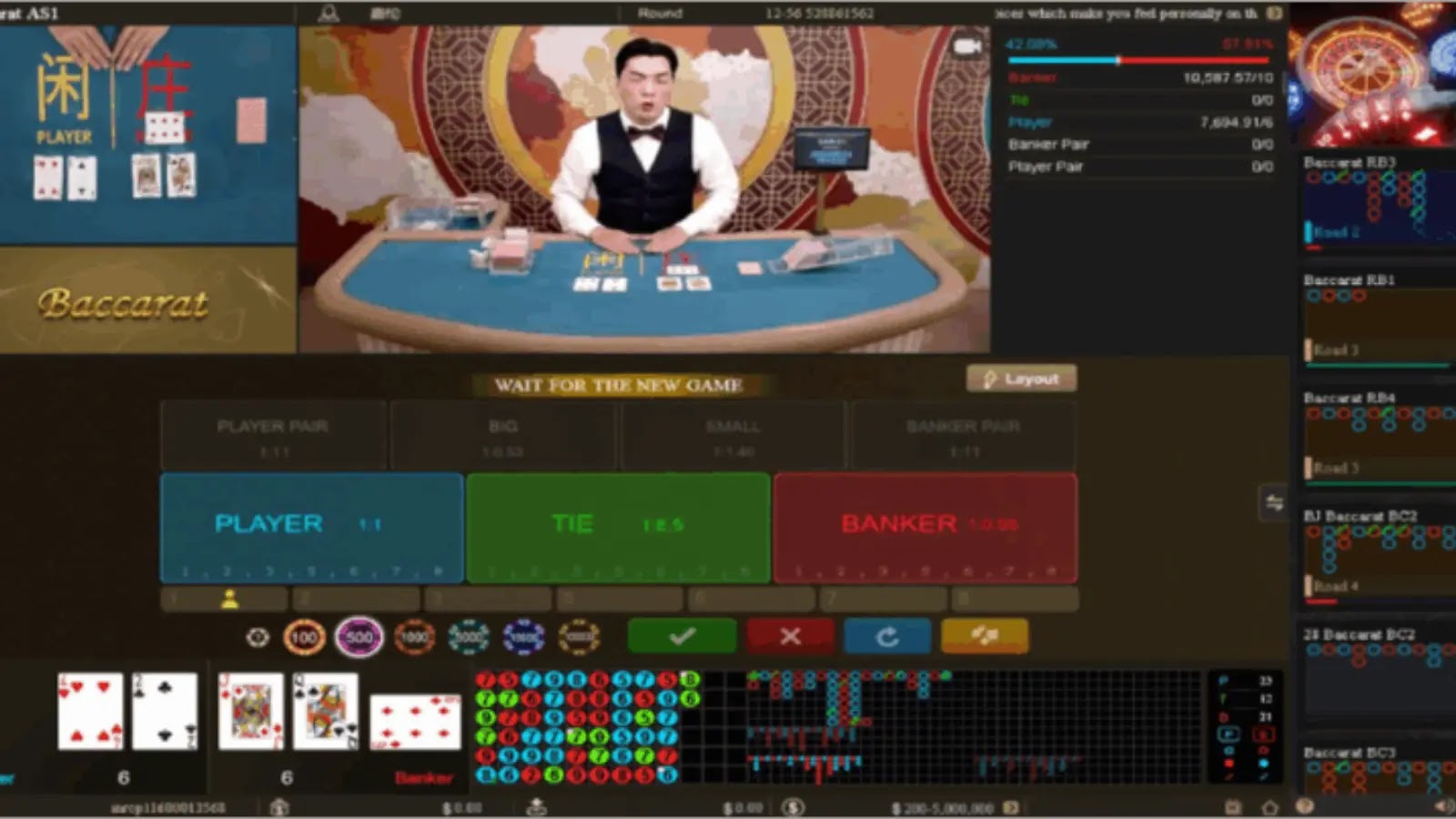
A major cybersecurity investigation has uncovered a sophisticated criminal operation called Vault Viper that exploits online gambling platforms to distribute…
Proofpoint has released a new open-source tool called PDF Object Hashing that helps security teams detect and track malicious files…
Security researchers have uncovered a sophisticated cyberattack campaign that exploited publicly exposed ASP.NET machine keys to compromise hundreds of Internet…
The public sector faces an unprecedented cybersecurity crisis as ransomware actors intensify their assault on government entities worldwide. According to…
ESET researchers have uncovered a sophisticated cyberespionage campaign targeting European defense companies specializing in unmanned aerial vehicle (UAV) technology. The…
A sophisticated new phishing attack discovered in early February 2025 is successfully bypassing Secure Email Gateways (SEGs) and evading perimeter…
Microsoft has released a critical security patch to address a severe remote code execution vulnerability affecting Windows Server Update Services…