Category: GBHackers
The monitoring and analysis of vulnerability exploitations are among the primary responsibilities of Sekoia.io’s Threat Detection & Research (TDR) team….
Patchwork, the advanced persistent threat (APT) actor also known as Dropping Elephant, Monsoon, and Hangover Group, has been observed deploying…
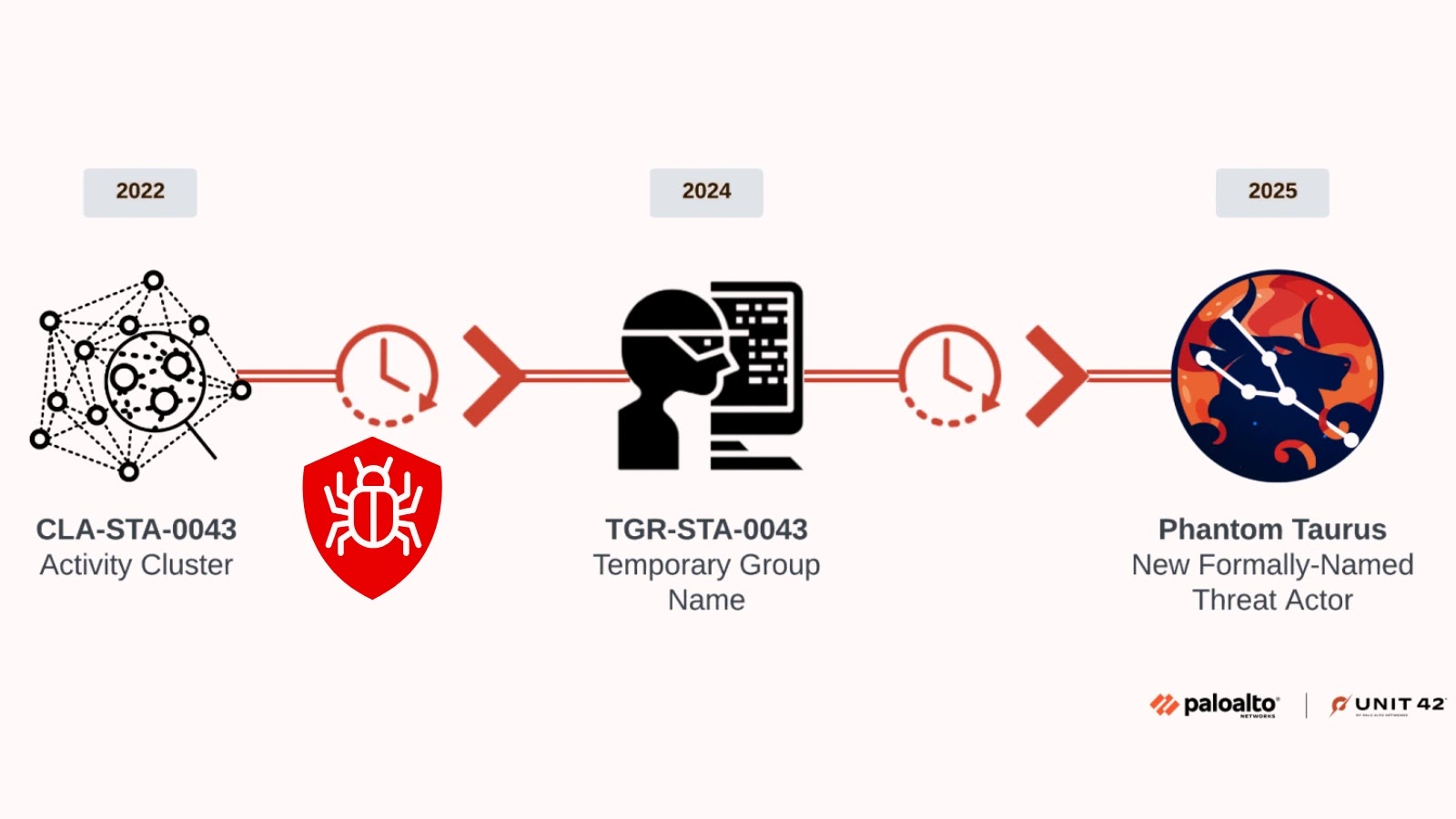
China-linked advanced persistent threat (APT) group Phantom Taurus has intensified espionage operations against government and telecommunications targets across Africa, the…
An emerging phishing campaign is targeting job seekers by masquerading as Google Careers recruiters, delivering seemingly legitimate emails that lead…
Japanese beer and beverage giant Asahi Group Holdings has been forced to halt production at its domestic factories as a…
Cybercriminals are exploiting the growing popularity of artificial intelligence tools by distributing malicious Chrome browser extensions that masquerade as legitimate…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical security alert highlighting the active exploitation of a serious…
The Cybersecurity and Infrastructure Security Agency (CISA) has released an urgent alert for system administrators and IT teams worldwide. Researchers…
A newly discovered attack on the npm ecosystem has exposed a deceptive backdoor embedded in a malicious package impersonating Postmark….
A surge in attacks targeting improperly managed MS-SQL servers, culminating in the deployment of the open-source XiebroC2 command-and-control (C2) framework….
Stormshield CTI researchers have identified two active phishing servers linked to APT35, revealing ongoing credential-stealing operations targeting government and military…
Organizations using VMware hypervisors face an urgent threat as a local privilege escalation zero-day, tracked as CVE-2025-41244, is under active exploitation…