Category: GBHackers
A new dark web marketplace listing has sparked alarm in the cybersecurity community after a seller using the handle “SebastianPereiro”…
Broadcom released VMSA-2025-0016 to address three key vulnerabilities affecting VMware vCenter Server and NSX products. The vulnerabilities include an SMTP…
Luxury department store Harrods has become the latest victim of a significant cybersecurity incident after hackers successfully accessed personal data belonging to 430,000…
Cybersecurity researchers have identified a sophisticated campaign where threat actors are using malicious advertisements and search engine optimization poisoning to…
Forensic-Timeliner is a fast, open-source command-line tool designed to help digital forensics and incident response (DFIR) teams quickly build a…
Security teams face a rapidly evolving campaign that abuses compromised SonicWall SSL VPN credentials to deliver Akira ransomware in under…
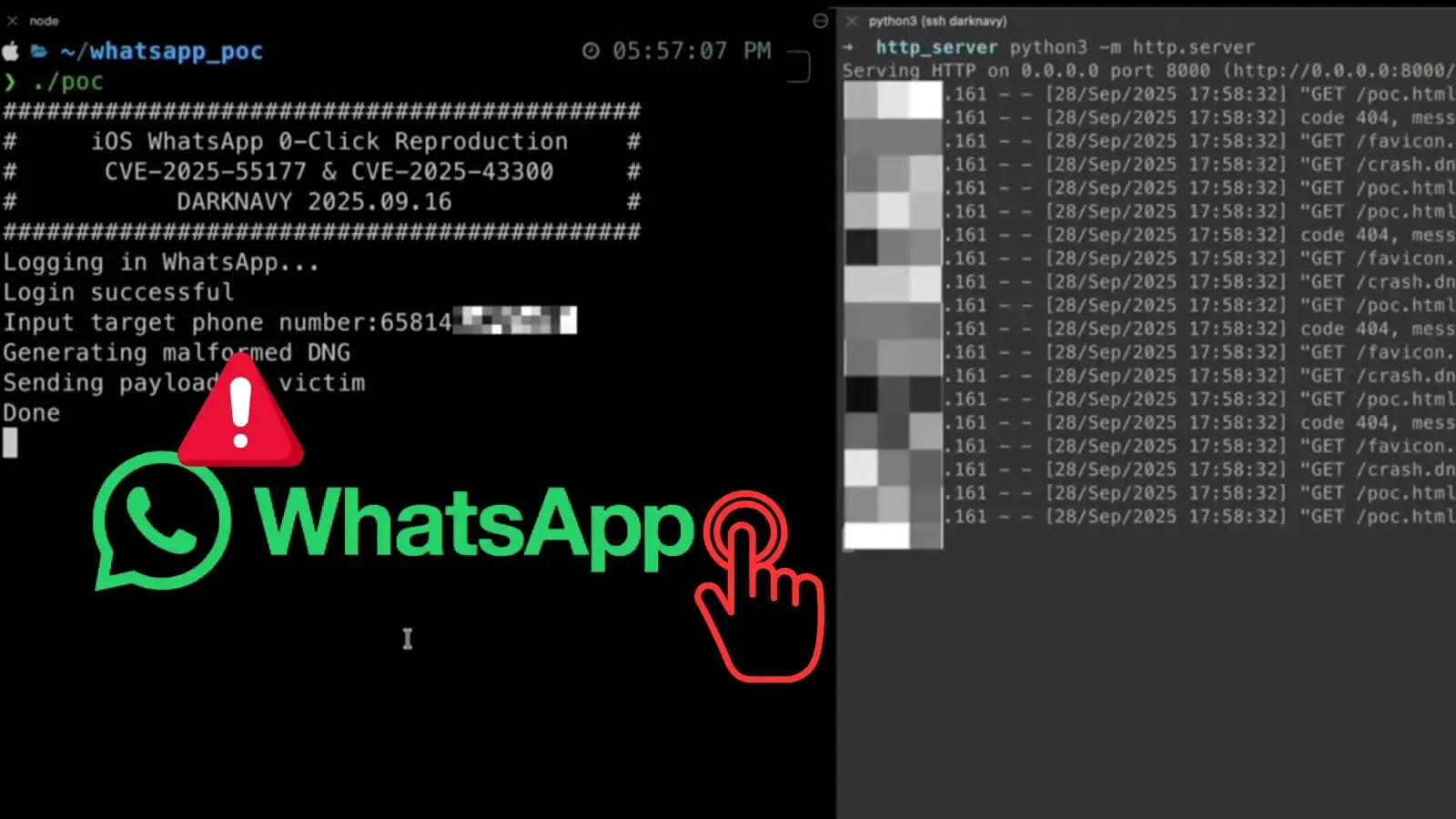
A newly discovered zero-click remote code execution (RCE) vulnerability in WhatsApp is putting millions of Apple users at risk. Researchers from DarkNavyOrg…
Adversaries don’t work 9–5 and neither do we. At eSentire, our 24/7 SOCs are staffed with elite threat hunters and…
A sophisticated malware campaign dubbed “TamperedChef” is exploiting trojanized productivity tools—disguised as seemingly benign applications—to bypass security controls, establish persistence,…
Jaguar Land Rover (JLR) has announced the controlled resumption of manufacturing operations following a significant cyberattack that disrupted its production…
Acreed, a novel infostealer first observed in February 2025, has rapidly gained traction among threat actors seeking discreet credential and…
A sophisticated malvertising campaign has been targeting organizations through a weaponized Microsoft Teams installer that delivers the dangerous Oyster malware,…