Category: GBHackers
Singapore, Singapore, September 29th, 2025, CyberNewsWire Analyzing over 14 billion cyber-attack records daily, ThreatBook ATI is a global solution enriched…
Cybercriminals expand malvertising campaigns from Facebook to Google Ads and YouTube, hijacking accounts to distribute crypto-stealing malware targeting financial platform…
Olymp Loader, a newly emerged Malware-as-a-Service (MaaS) offering, has rapidly gained traction across underground forums and Telegram since its debut…
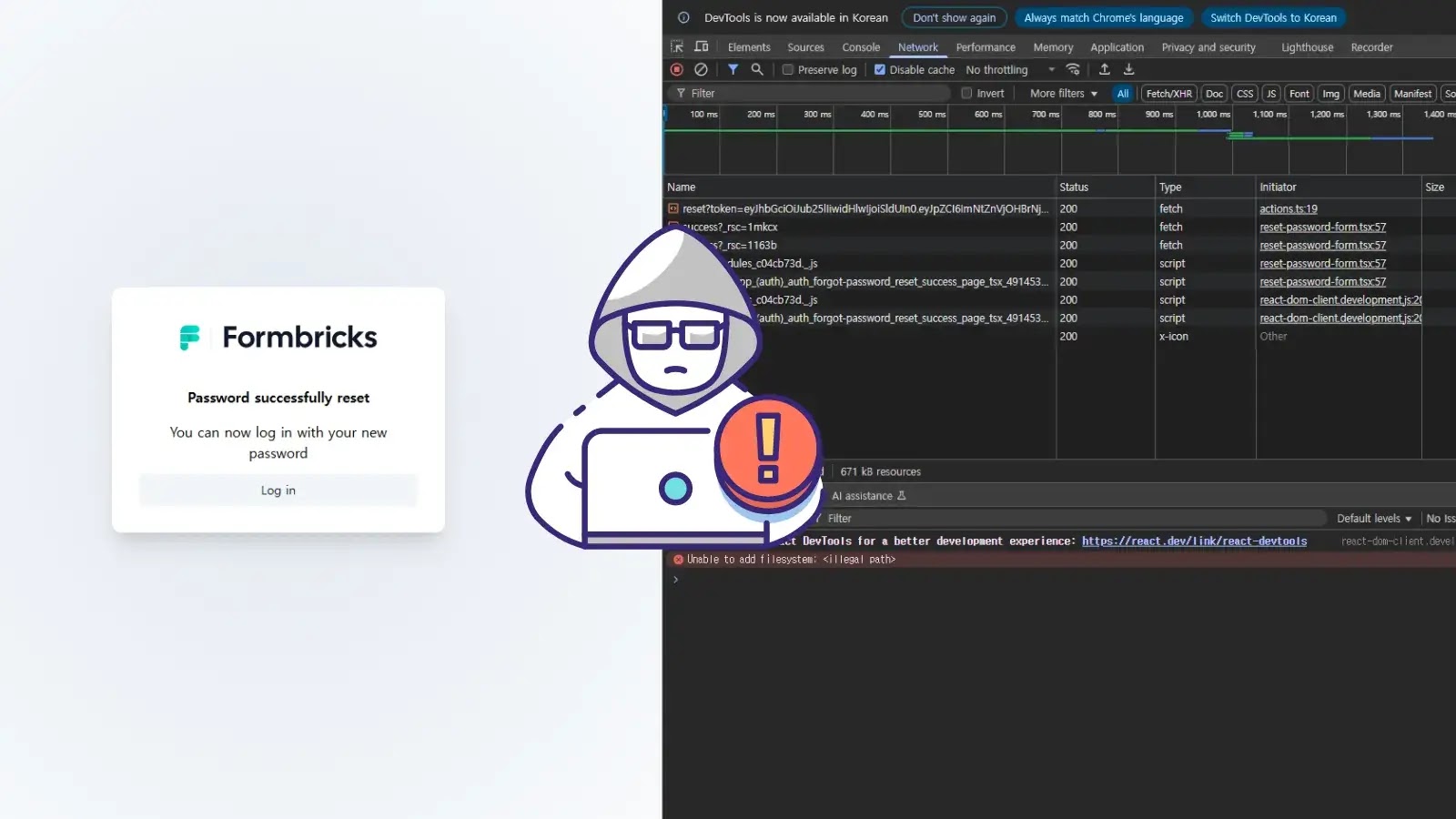
A critical vulnerability in the open source Formbricks experience management toolbox allows attackers to reset any user’s password without authorization. Published three…
A sophisticated new malware strain targeting macOS users has emerged, capable of bypassing traditional antivirus solutions while specifically targeting developers…
A critical security vulnerability in SUSE Rancher Manager has been discovered that enables attackers with elevated privileges to lock out administrative accounts,…
Dutch authorities have arrested two 17-year-old boys on suspicion of “state interference” in a cybersecurity case with alleged connections to…
Cybersecurity researchers have identified a growing trend where threat actors are increasingly exploiting Dynamic DNS providers to host malicious infrastructure,…
Security researchers have identified a critical DLL hijacking vulnerability in Notepad++ version 8.8.3, tracked as CVE-2025-56383. This flaw enables attackers to…
Security teams worldwide have been warned after attackers began exploiting a newly discovered zero-day vulnerability in Cisco Adaptive Security Appliance…
A critical zero-day vulnerability in Cisco Secure Firewall Adaptive Security Appliance (ASA) Software and Cisco Secure Firewall Threat Defense (FTD)…
Enterprises everywhere are embracing MCP servers—tools that grant AI assistants “god-mode” permissions to send emails, run database queries, and automate…