Category: GBHackers
Content creators and small businesses are facing a sophisticated new threat targeting their Facebook accounts through deceptive advertisements promising free…
Fileless malware has become a formidable adversary for security teams, operating entirely in memory and evading disk-based detection. A recent…
GitLab has released critical security updates across multiple versions to address six significant vulnerabilities that could enable denial-of-service attacks, server-side…
CyberVolk ransomware, which first emerged in May 2024, has escalated its operations against government agencies, critical infrastructure, and scientific institutions…
Content creators and small businesses are facing a sophisticated new threat targeting their Facebook accounts through deceptive advertisements promising free…
A newly disclosed vulnerability in Apple’s CarPlay ecosystem enables remote code execution with root privileges, posing a serious risk to connected…
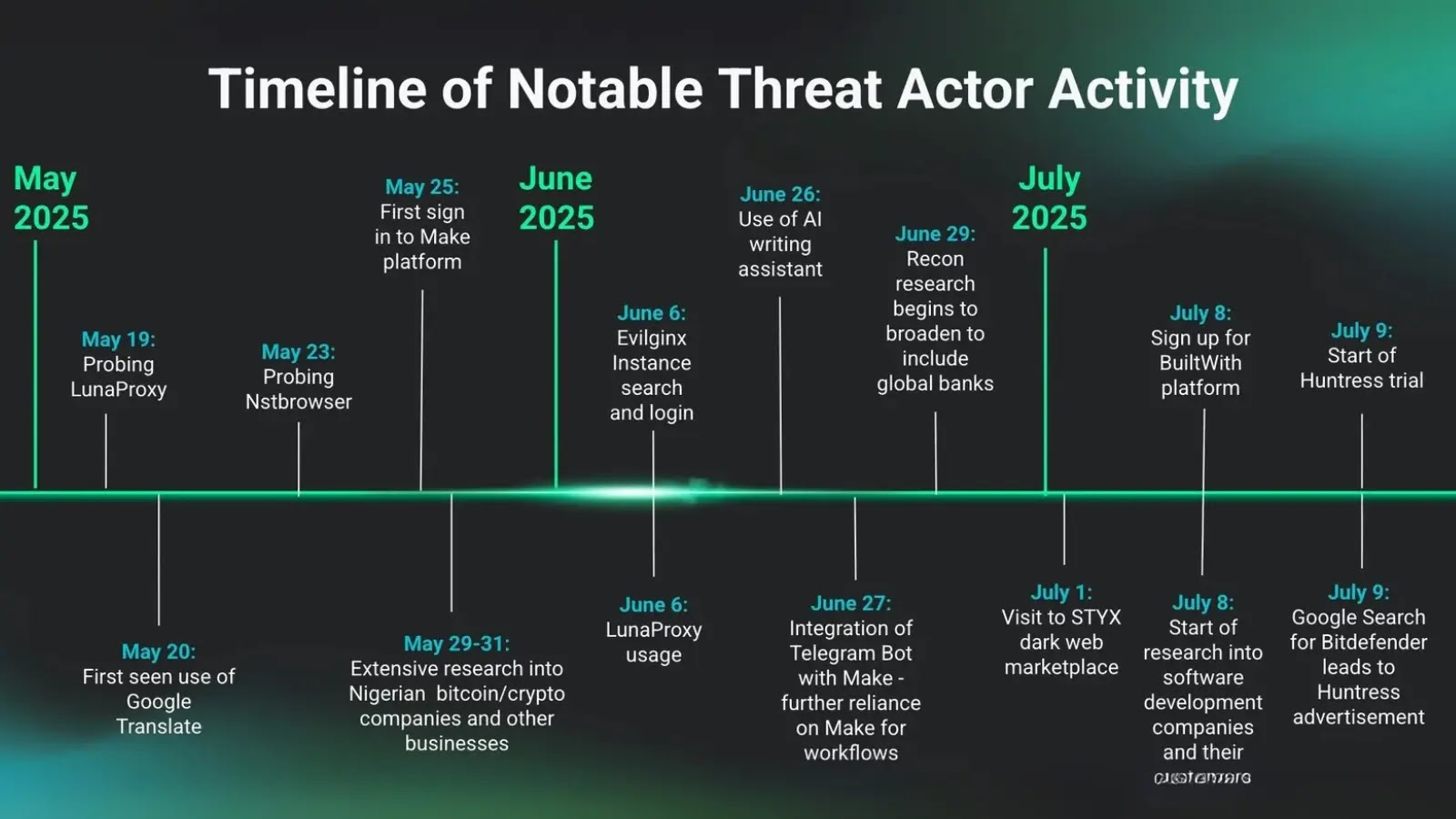
The cybersecurity landscape has witnessed a novel phishing campaign that weaponizes Google’s no-code platform, AppSheet, to harvest user credentials. By…
In a twist of fate that underscores both the power and inherent transparency of endpoint detection and response (EDR) solutions….
A sophisticated espionage campaign leveraging a previously unknown malware strain dubbed GONEPOSTAL, attributed to the notorious Russian state-sponsored group KTA007,…
Sophos has released an important security advisory addressing a critical authentication bypass vulnerability in its AP6 Series Wireless Points. Attackers who…
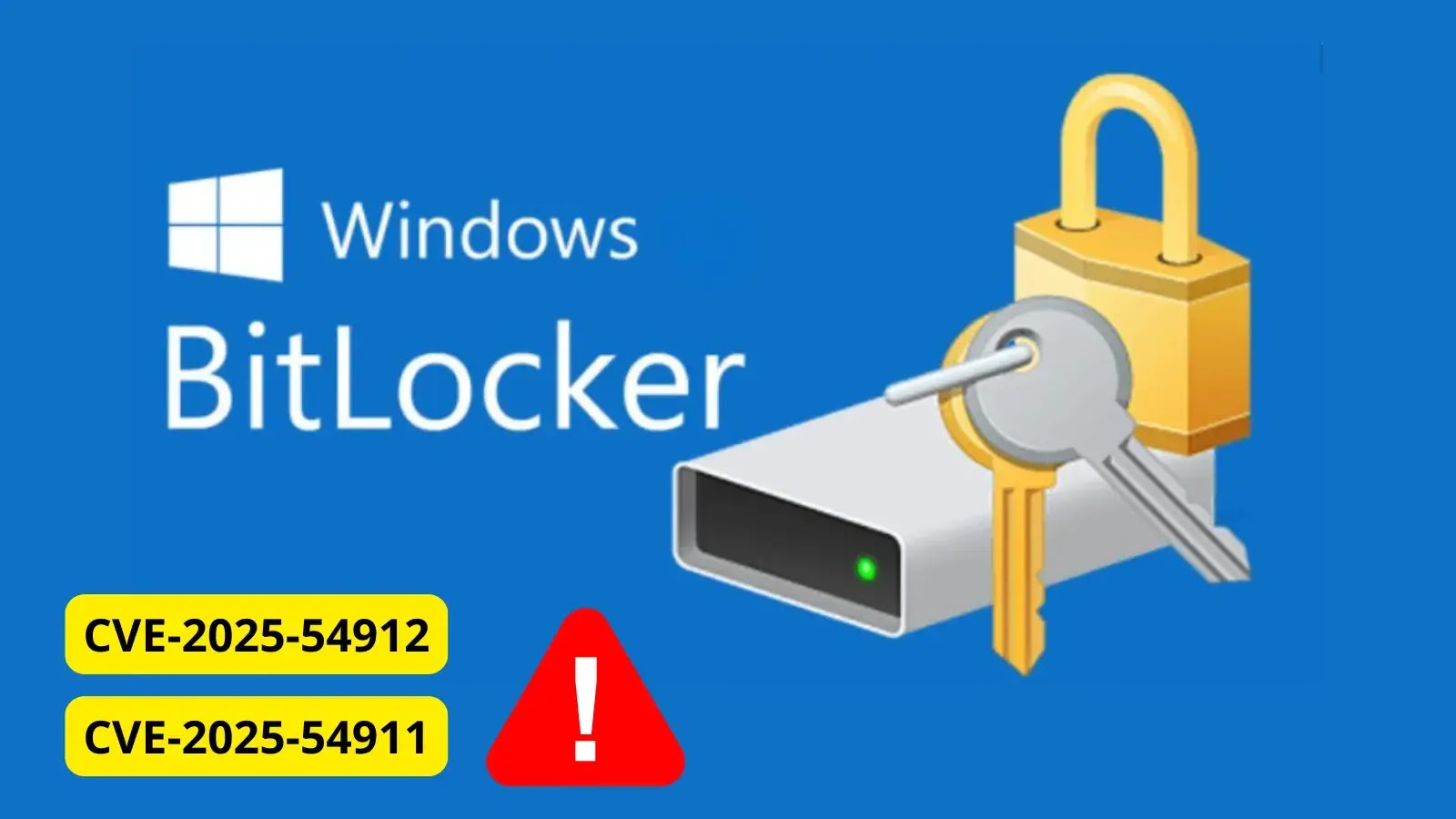
Microsoft has released a warning about two serious security flaws in Windows BitLocker that could allow attackers to gain elevated…
A critical security vulnerability has been discovered in SAP NetWeaver AS Java Deploy Service that enables authenticated attackers to execute arbitrary code…