Category: GBHackers
Spanish law enforcement recently dismantled an advanced AI-driven phishing network and arrested the mastermind developer known as “GoogleXcoder.” This operation…
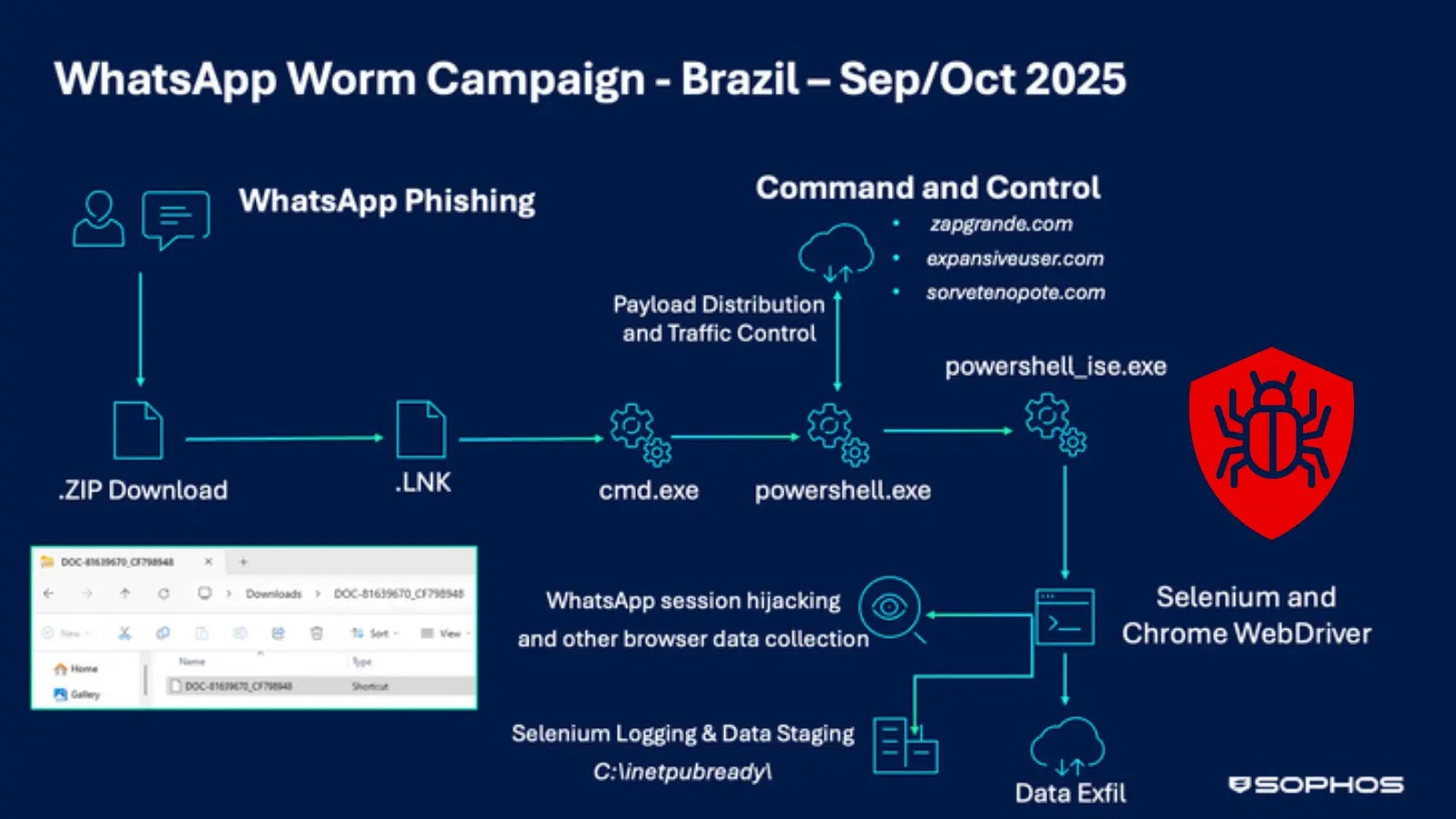
Cybersecurity researchers have uncovered a sophisticated new campaign targeting WhatsApp users in Brazil with self-propagating malware designed to steal banking…
A new cybercriminal conglomerate known as Scattered Lapsus$ Hunters has emerged as a significant threat to global organizations, claiming responsibility…
Oracle has issued a critical security alert for a severe vulnerability in its E-Business Suite platform that could allow attackers…
Microsoft Defender for Endpoint’s cloud communication can be abused to bypass authentication, intercept commands, and spoof results, allowing attackers to…
Threat actors are increasingly abusing Discord webhooks as covert command-and-control (C2) channels inside open-source packages, enabling stealthy exfiltration of secrets,…
Security researchers have identified a new, active campaign of the Stealit malware that uses an experimental Node.js feature to infect…
Menlo Park, USA, October 10th, 2025, CyberNewsWire AccuKnox, a leader in Zero Trust Cloud Native Application Protection Platforms (CNAPP), is…
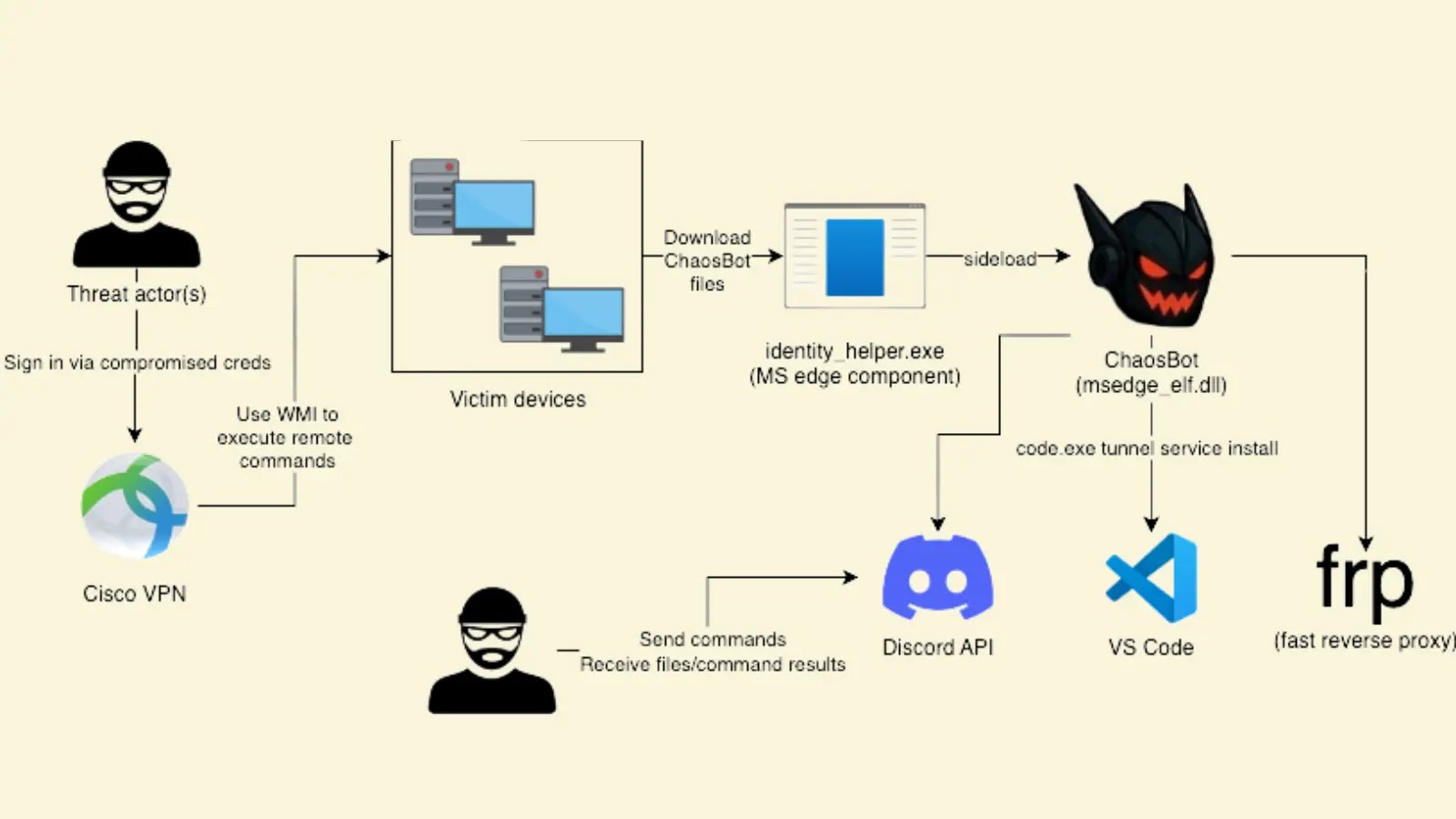
Adversaries have once again demonstrated that operational hours are irrelevant when mounting sophisticated cyberattacks. eSentire’s TRU team first observed suspicious…
A significant uptick in Akira ransomware attacks has been observed exploiting unpatched SonicWall SSL VPN devices between July and August…
Socket’s Threat Research Team has uncovered a sprawling phishing campaign—dubbed “Beamglea”—leveraging 175 malicious npm packages that have amassed over 26,000…
A critical weakness in GitHub Copilot Chat discovered in June 2025 exposed private source code and secrets to attackers. Rated…