Category: GBHackers
A novel serverless command-and-control (C2) technique that abuses Google Calendar APIs to obscure malicious traffic inside trusted cloud services. Dubbed…
A critical security vulnerability has been discovered in Microsoft Windows systems that allows attackers to escalate their privileges and potentially…
Attackers can bypass Endpoint Detection and Response (EDR) tools and file locks by reading raw disk sectors directly, highlighting the…
A sophisticated new botnet called NightshadeC2 that employs an innovative “UAC Prompt Bombing” technique to evade Windows Defender and compromise…
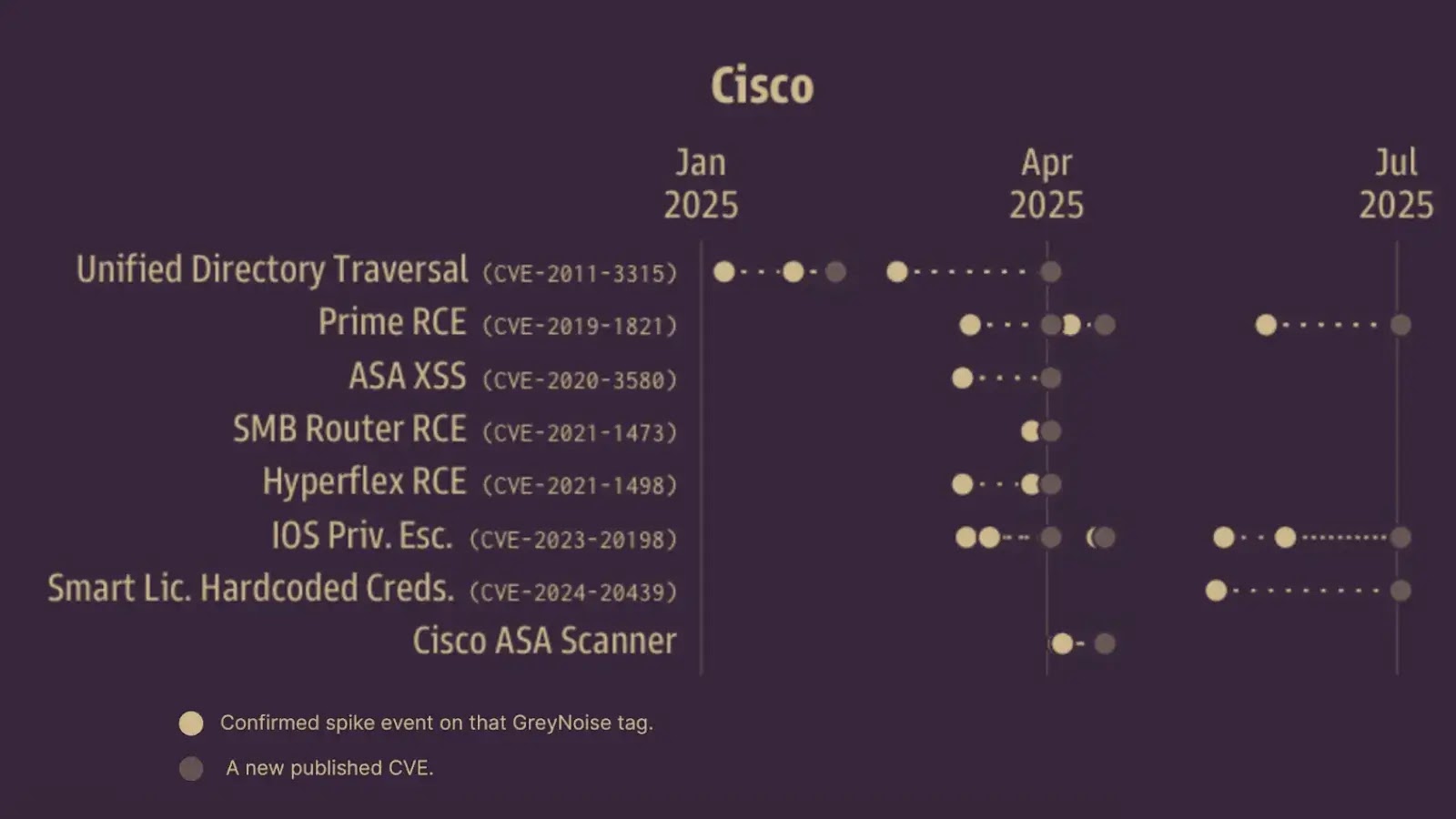
Security researchers have detected massive scanning campaigns targeting Cisco Adaptive Security Appliance (ASA) devices, with attackers probing over 25,000 unique…
Cybersecurity researchers uncovered a sophisticated, Iran-linked spear-phishing operation that exploited a compromised Ministry of Foreign Affairs (MFA) mailbox in Oman…
Wilmington, United States, September4th, 2025, CyberNewsWire: Veteran email security leader to expand MSP and VAR partnerships and accelerate DMARC adoption. …
Tire manufacturer launches a comprehensive investigation after a limited cyber incident affects operations at multiple plants. Bridgestone Americas has confirmed…
ESET security researchers have uncovered a sophisticated cyber threat campaign targeting Windows servers across multiple countries, with attackers deploying custom…
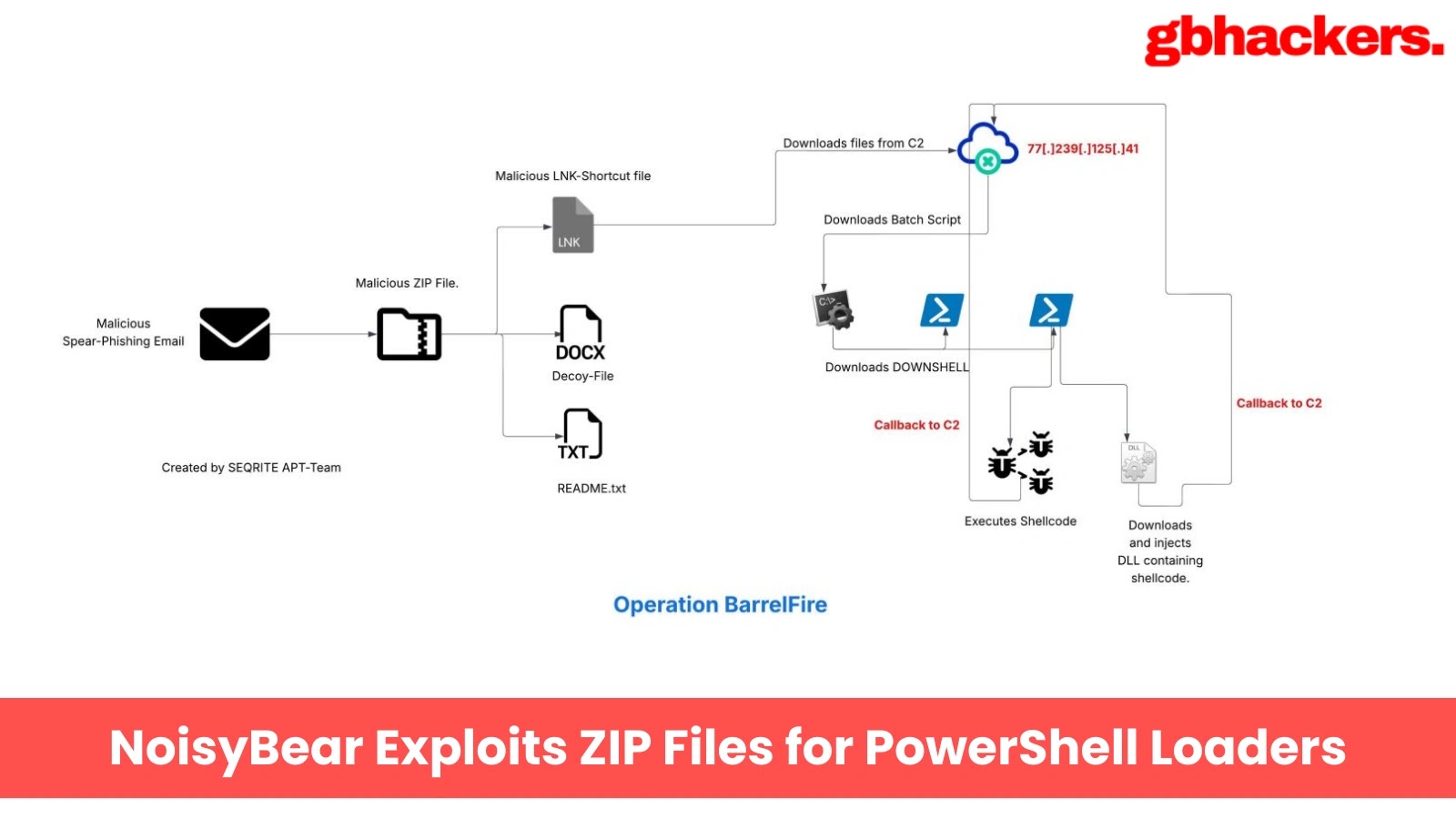
The threat actor known as NoisyBear has launched a sophisticated cyber-espionage effort called Operation BarrelFire, using specially designed phishing lures…
Security researchers revealed that three unauthorized TLS certificates were issued in May 2025 for 1.1.1.1, the widely used public DNS…
Microsoft has officially acknowledged a significant User Account Control (UAC) bug that is causing widespread installation issues across Windows 10…