Category: GBHackers
More than 1,100 instances of Ollama—a popular framework for running large language models (LLMs) locally—were discovered directly accessible on the…
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert about a serious security hole in certain TP-Link…
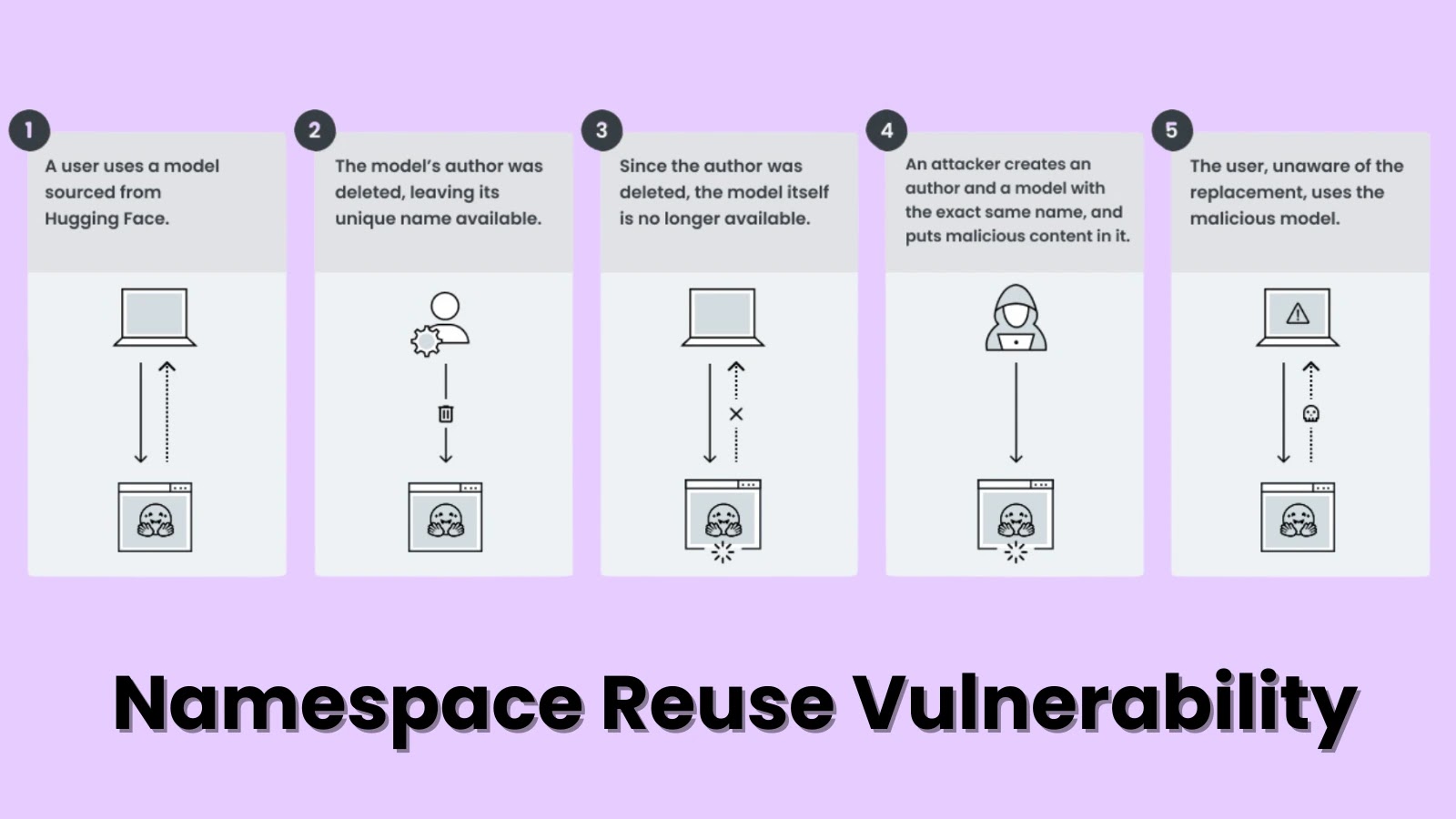
A newly discovered vulnerability in the AI supply chain—termed Model Namespace Reuse—permits attackers to achieve Remote Code Execution (RCE) across…
PagerDuty has confirmed that it experienced a data breach following a compromise of its Salesforce account. The company was first…
The recently emerged DireWolf ransomware group has launched a sophisticated new campaign targeting Windows systems worldwide, employing ruthless tactics to…
The U.S. District Court for the District of Columbia today imposed landmark remedies in the Justice Department’s monopolization case against…
The BC-SECURITY team has released a major update to its flagship offensive security framework, Empire, introducing enhanced agent capabilities and comprehensive…
The Cybersecurity and Infrastructure Security Agency (CISA) yesterday issued a high-severity alert (ICSA-25-245-03) regarding a critical vulnerability in SunPower’s PVS6…
An industrial-scale phishing campaign exploiting Google Cloud and Cloudflare infrastructure operated in plain sight for more than three years, targeting…
A cutting-edge penetration testing tool called BruteForceAI has arrived, bringing automation and artificial intelligence to the art of login page detection and…
A newly disclosed remote code execution (RCE) vulnerability in Microsoft’s IIS Web Deploy toolchain has captured industry attention after the…
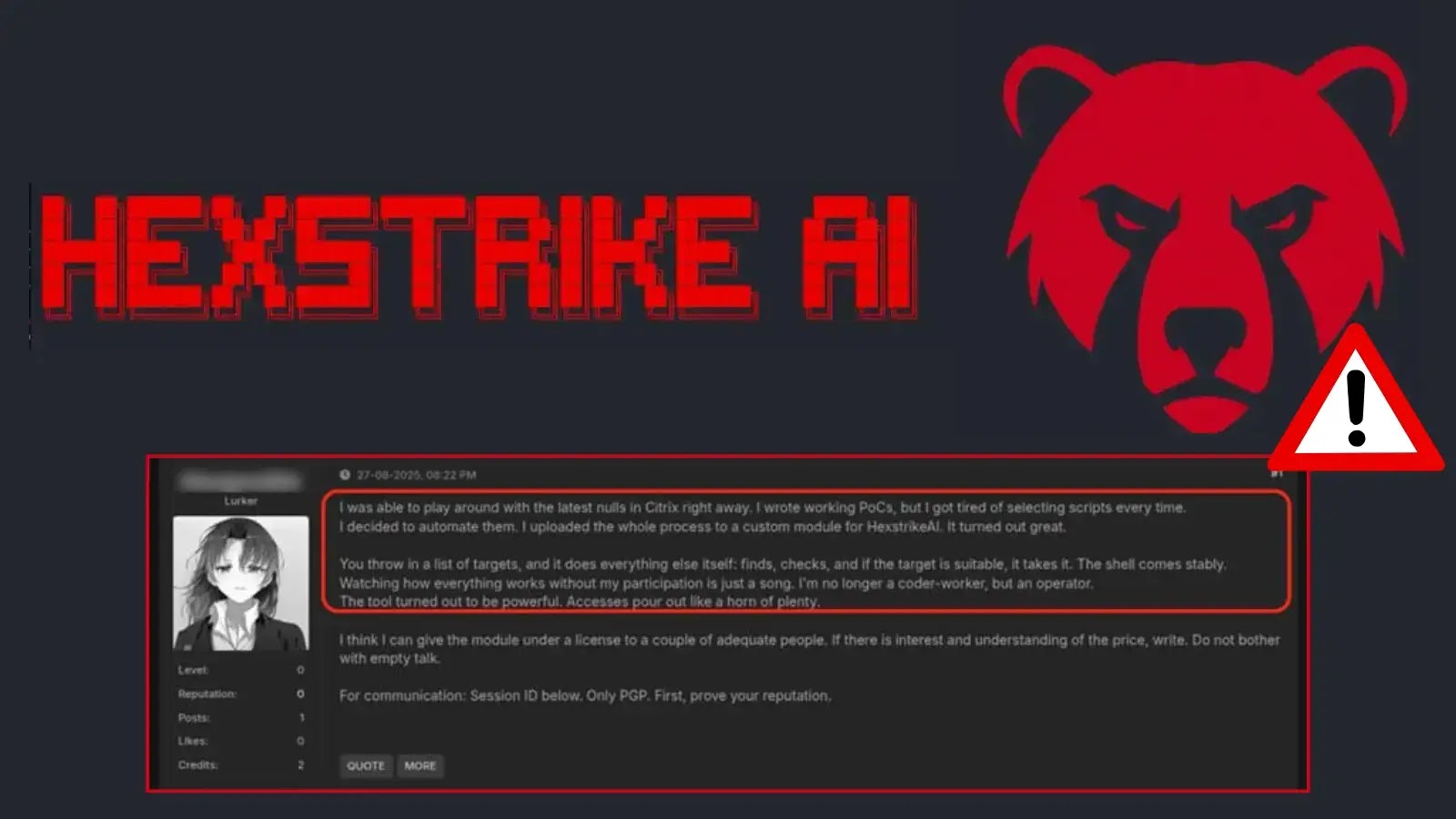
Within hours of its release, the newly unveiled framework Hexstrike-AI has emerged as a game-changer for cybercriminals, enabling them to scan, exploit…