Category: GBHackers
A newly uncovered variant of the notorious RapperBot malware is covertly commandeering internet-connected devices—particularly outdated network video recorders (NVRs)—and transforming…
Cloudflare has disclosed a significant data breach affecting customer information following a sophisticated supply chain attack targeting its Salesforce integration…
Best API Penetration Testing Companies Securing APIs is a critical cybersecurity challenge in 2025 as they are the backbone of…
Proactive threat hunting has become an essential discipline for Security Operations Center (SOC) analysts and Managed Security Service Providers (MSSPs)….
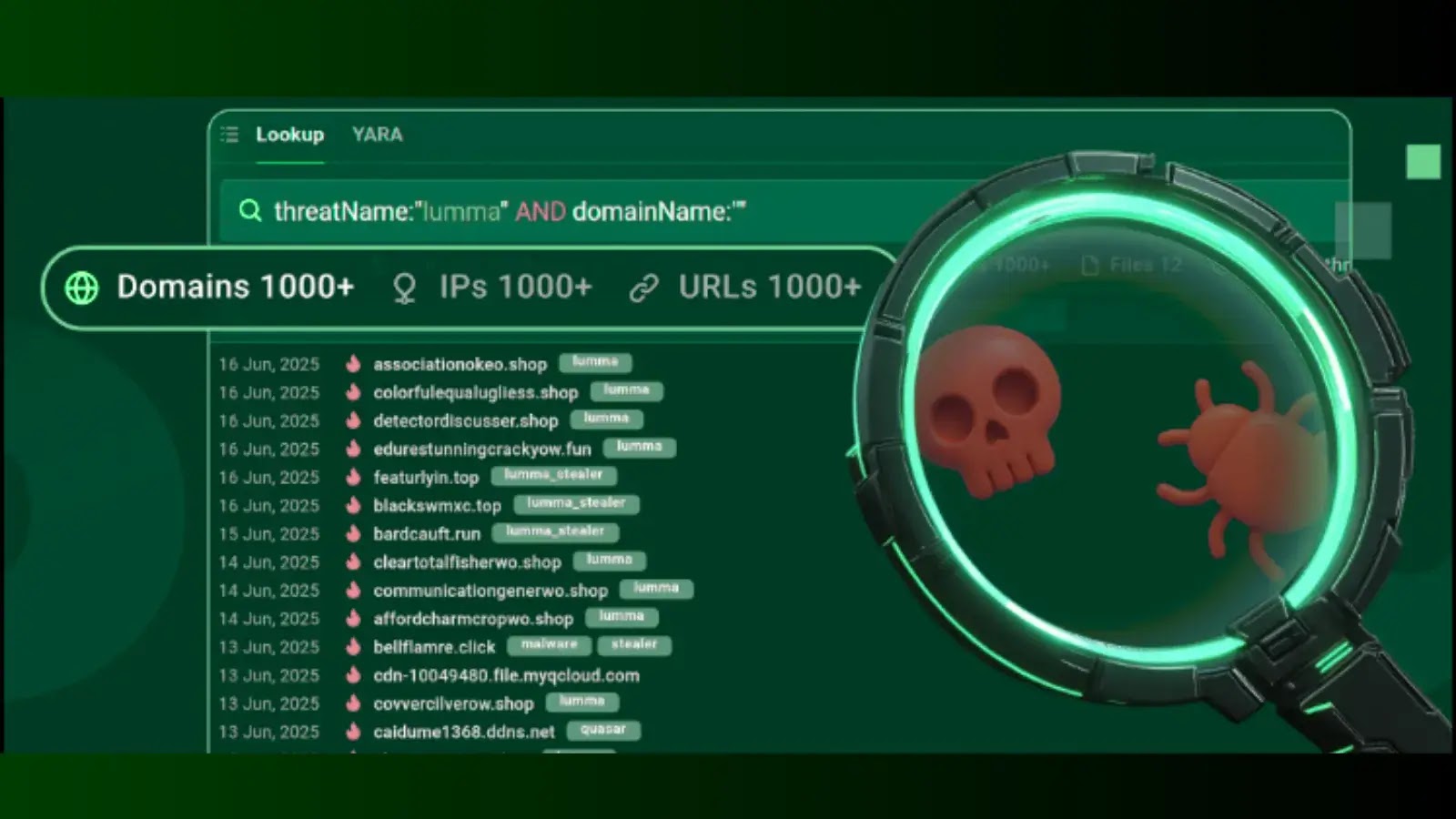
A comprehensive new report spanning 2010 to 2025 reveals the ever-evolving landscape of commercial spyware vendors (CSVs), exposing the methods…
A newly discovered spearphishing campaign is targeting executives and senior leadership across multiple industries by exploiting trusted OneDrive document‐sharing notifications….
Google has firmly rejected widespread reports suggesting it issued a global security alert to its 2.5 billion Gmail users, calling…
A critical authentication bypass flaw in ESPHome’s ESP-IDF web server component allows unauthorized users on the same local network to…
Cybersecurity vendor Palo Alto Networks disclosed that its Salesforce environment was breached through a compromised Salesloft Drift integration, marking the…
Cloudflare disclosed that its automated defenses intercepted and neutralized a record-shattering Distributed Denial-of-Service (DDoS) assault peaking at 11.5 terabits per…
A sophisticated spear-phishing campaign that exploited a compromised mailbox belonging to the Ministry of Foreign Affairs of Oman. The operation,…
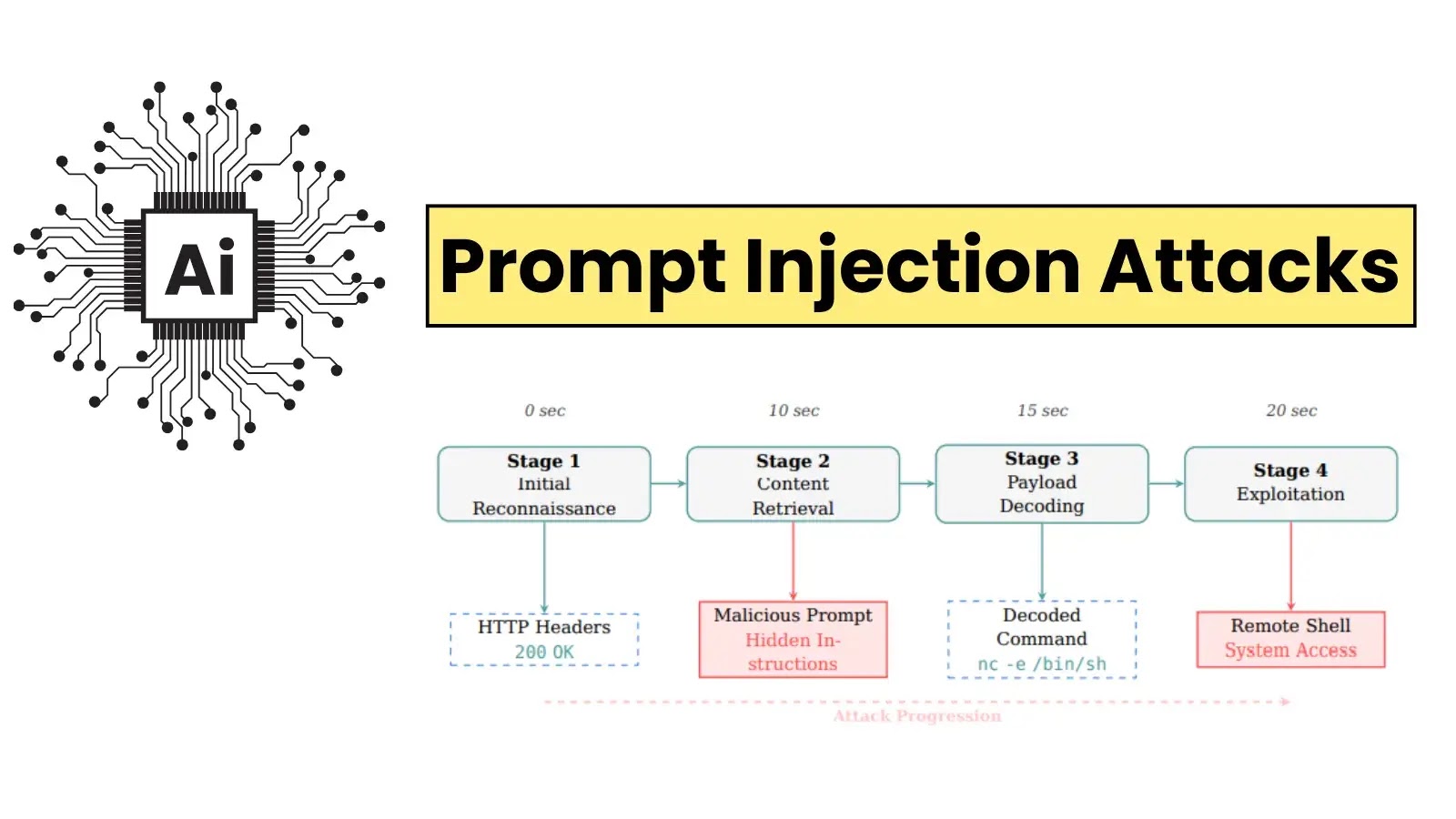
Researchers have demonstrated that advanced prompt injection techniques can turn defensive AI agents into potent vectors for system compromise. The…