Category: GBHackers
A serious security vulnerability in Netskope’s Windows client has been discovered that could allow attackers to escalate privileges from a…
Security researchers at watchTowr Labs have uncovered a devastating chain of vulnerabilities in Sitecore Experience Platform that could allow attackers…
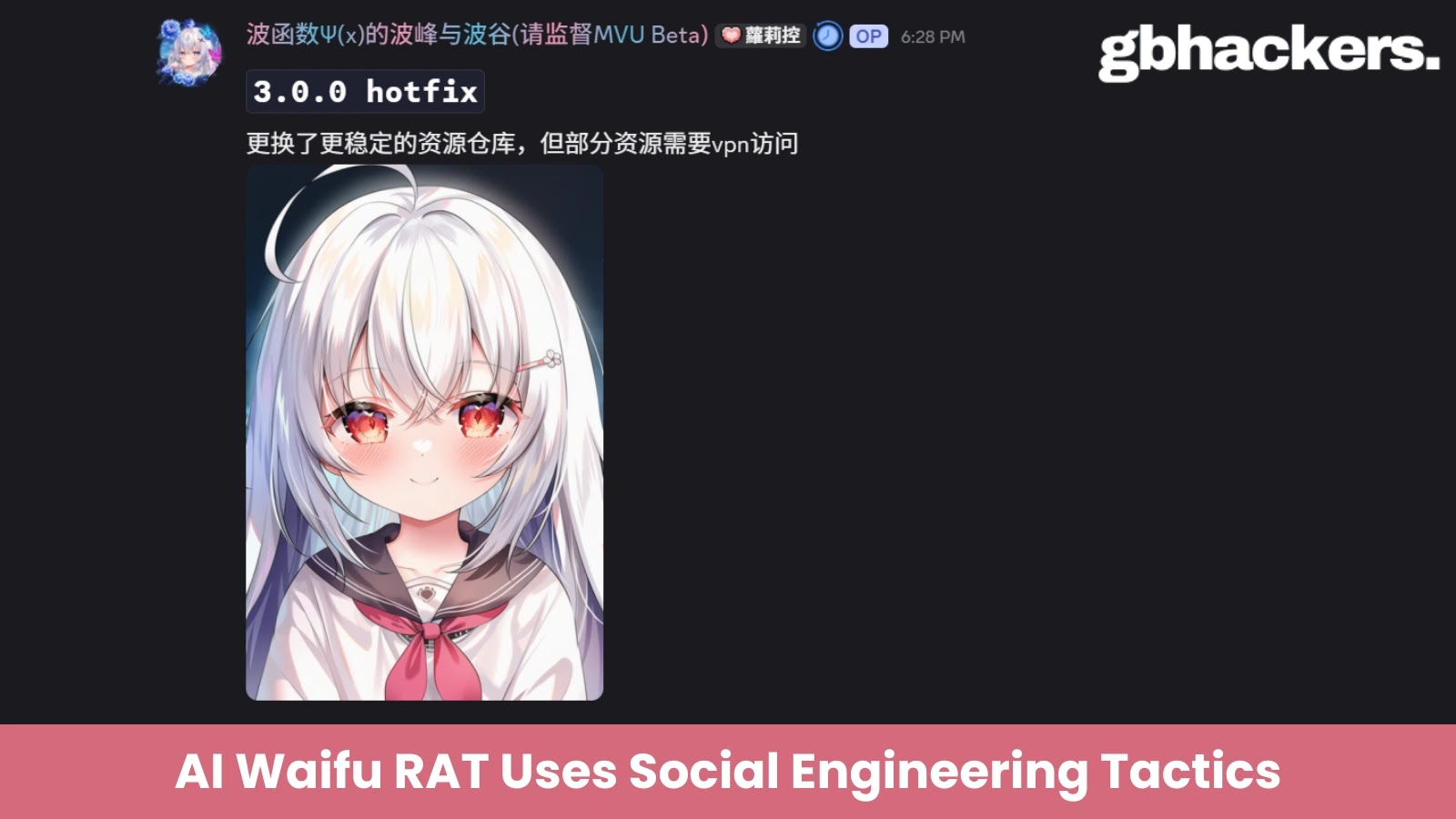
A sophisticated new malware campaign has emerged that weaponizes artificial intelligence and social engineering to target niche online communities. Security…
A sophisticated voice phishing operation has emerged as a significant threat to organizations worldwide, with cybercriminals successfully infiltrating Salesforce environments…
QNAP Systems has released security patches to address multiple vulnerabilities affecting QVR firmware in legacy VioStor Network Video Recorder (NVR)…
Security researcher Kevin Beaumont has revealed alarming details about CVE-2025-6543, a critical Citrix NetScaler vulnerability that was actively exploited as…
Amazon’s cybersecurity team has successfully disrupted a sophisticated watering hole campaign orchestrated by APT29, a notorious hacking group linked to…
WhatsApp has issued a critical security advisory addressing a newly discovered zero-day vulnerability, tracked as CVE-2025-55177, which has been exploited…
A widespread supply chain attack on the popular Nx build system has compromised dozens of high-traffic packages, exposing sensitive credentials…
A recently uncovered vulnerability in the Visual Studio Code (VS Code) Marketplace has allowed malicious actors to hijack discontinued extension…
A clandestine campaign in which threat actors are weaponizing a legitimate-looking PDF document, titled “국가정보연구회 소식지 (52호)” (National Intelligence Research…
A sophisticated backdoor in AppSuite PDF Editor that enables threat actors to execute arbitrary commands on compromised Windows systems. Initially…