Category: GBHackers
A fresh wave of domain-confusion phishing emails is sweeping through the Python community, once again setting its sights on PyPI…
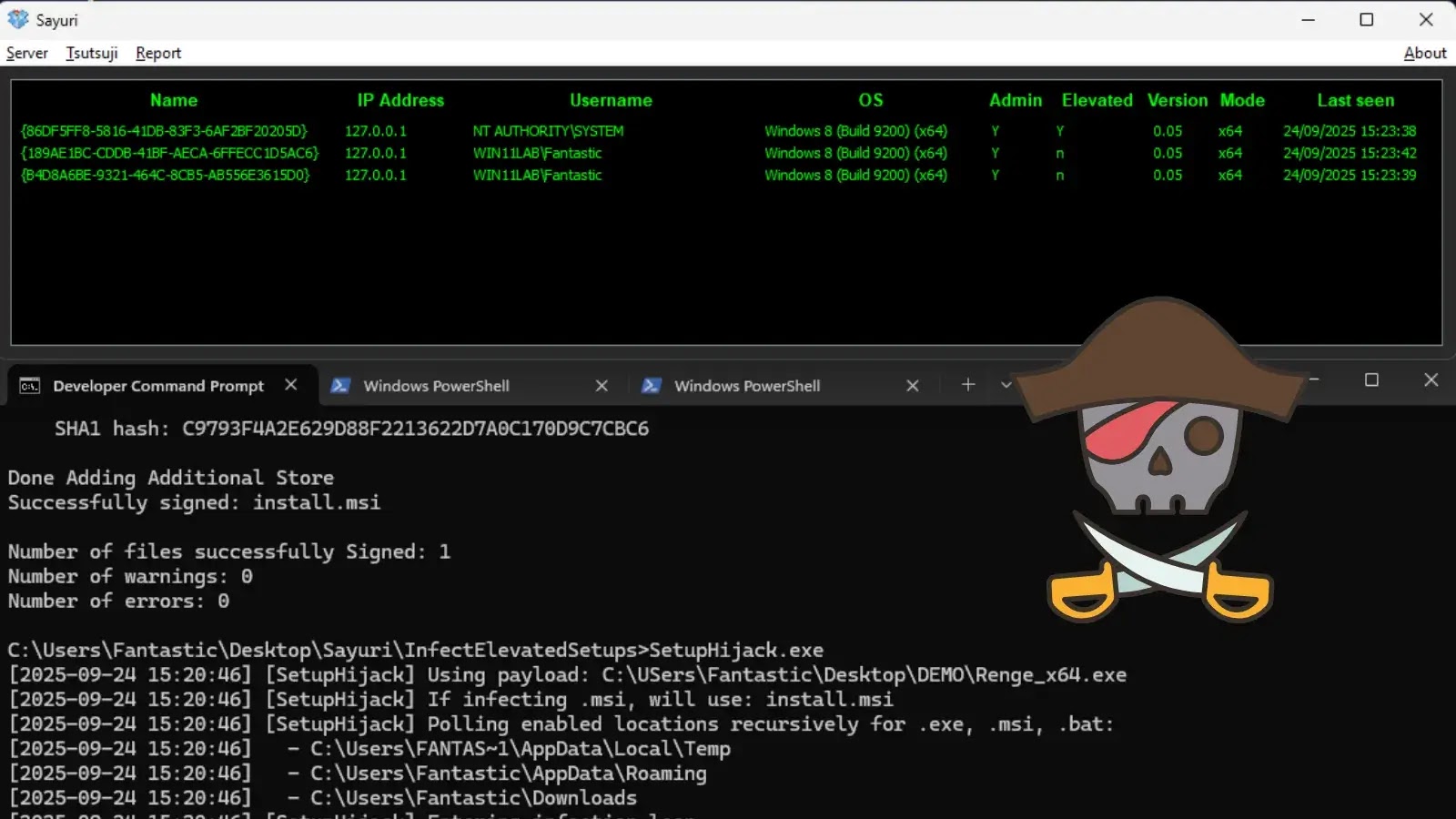
Security researchers at Hacker House have released SetupHijack, a proof-of-concept tool that exploits race conditions and insecure file handling in…
Threat actors from the Lone None group are exploiting copyright takedown notices to distribute sophisticated malware, including Pure Logs Stealer…
Attackers have stepped up their tactics by deploying stealthy backdoors disguised as legitimate WordPress components, ensuring persistent administrative access even…
Security researchers have observed renewed exploit campaigns targeting an eight-year-old backdoor in Hikvision cameras to harvest configuration files, user lists,…
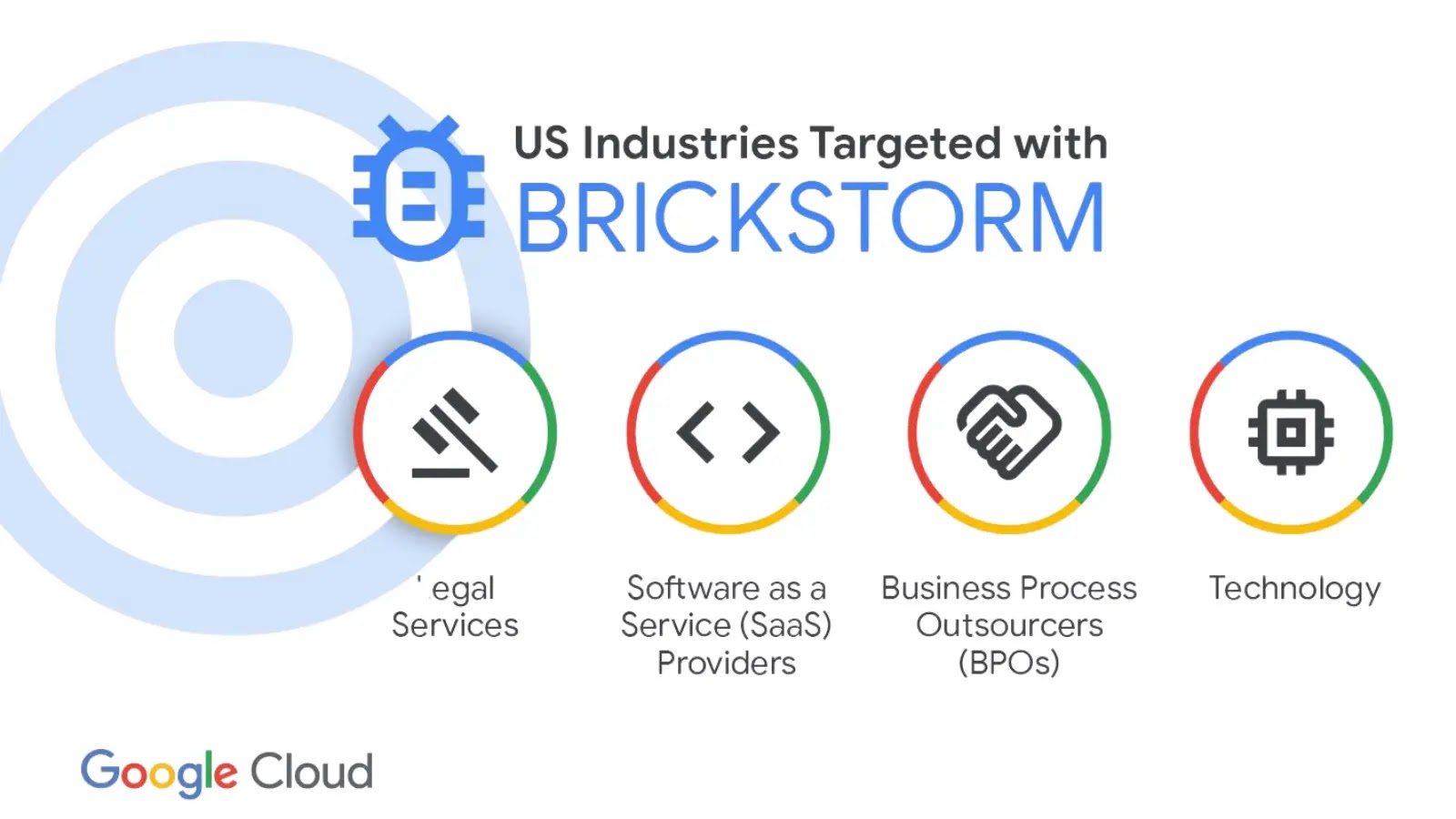
Persistent, stealthy, and cross-platform, the BRICKSTORM backdoor has emerged as a significant threat to U.S. technology and legal organizations. Tracked…
A critical vulnerability in the Linux Kernel’s ksmbd file sharing component allows remote attackers to execute code with kernel privileges….
A critical vulnerability in NVIDIA’s Merlin Transformers4Rec library allows attackers to achieve remote code execution with root privileges. Discovered by…
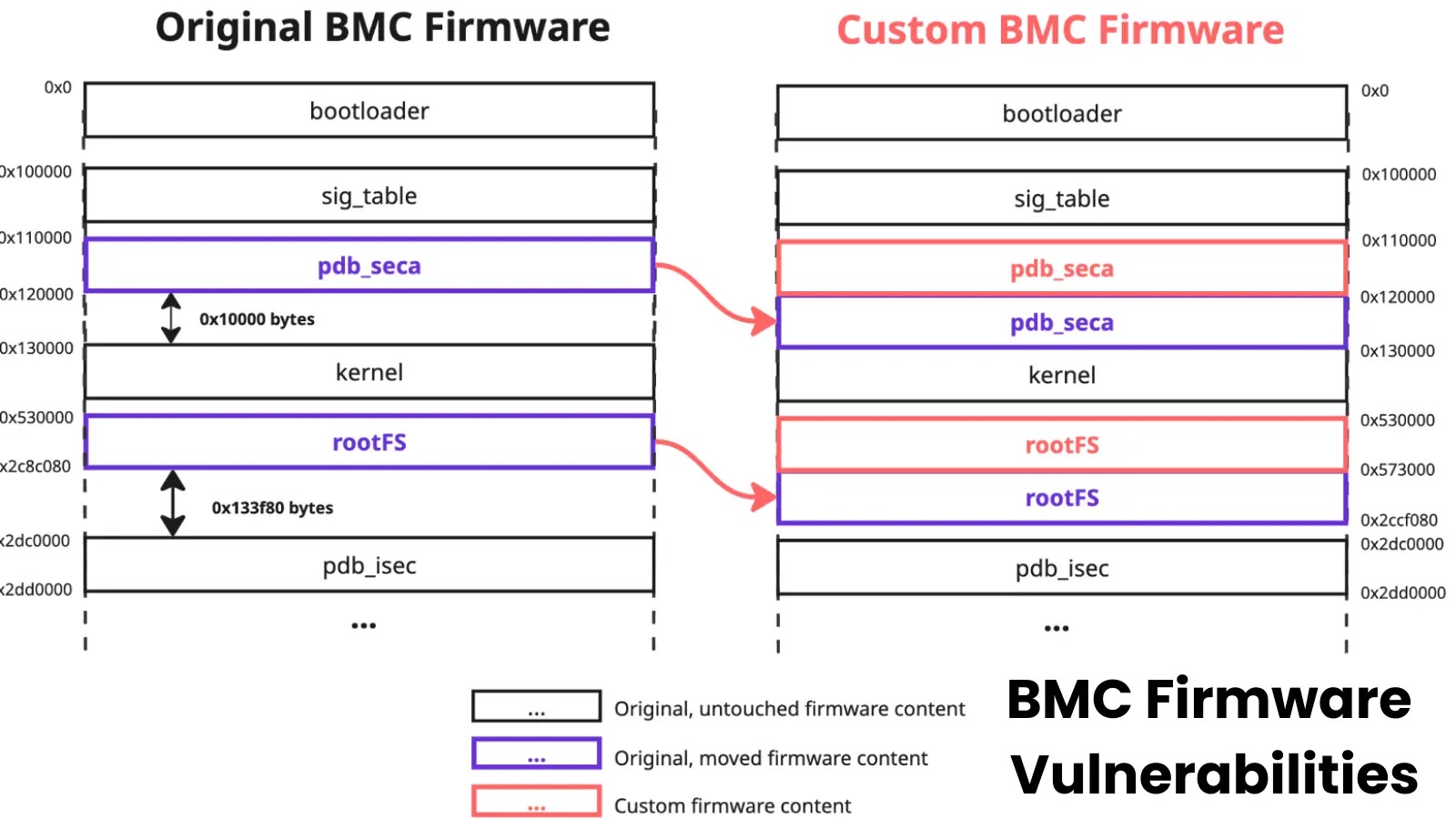
In January 2025, Supermicro released patches addressing critical vulnerabilities in its Baseboard Management Controller (BMC) firmware validation logic. Despite these…
A new study has uncovered a method for silently installing custom extensions on Chromium-based browsers running in Windows domain environments….
A large-scale campaign targeting Mac users is leveraging fake GitHub pages to distribute information-stealing malware disguised as popular legitimate applications….
A comprehensive security analysis has revealed a widespread vulnerability affecting Firebase-powered mobile applications, with over 150 popular apps inadvertently exposing…