Category: GBHackers
Threat actors are increasingly refining Android droppers to circumvent enhanced security measures, extending their utility beyond sophisticated banking trojans to…
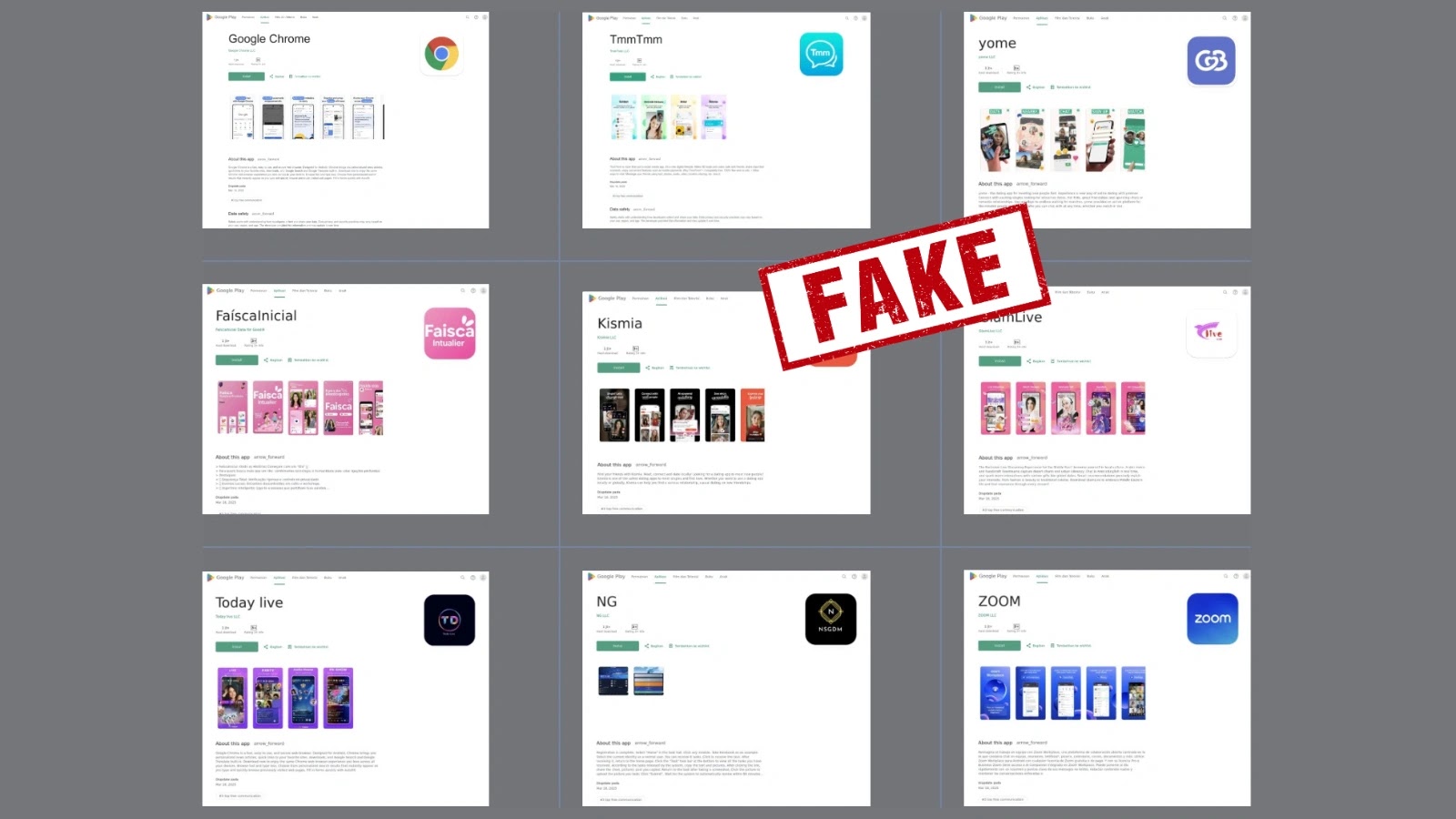
Cybersecurity researchers have identified a resurgence of SpyNote malware campaigns targeting Android users through sophisticated fake Google Play Store websites….
A critical security risk has emerged for Windows users of WhatsApp Desktop who also have Python installed. Attackers can exploit…
Google Threat Intelligence Group (GTIG) has uncovered a multifaceted cyber espionage operation attributed to the PRC-nexus threat actor UNC6384, believed…
Maryland’s transit network experienced widespread disruption this week after a sophisticated cyberattack targeted critical information systems, forcing the Maryland Transit…
A comprehensive study examining the location data practices of the top 10 social media platforms has uncovered concerning patterns of…
French retail giant Auchan announced on August 21 that it fell victim to a cyberattack that resulted in the theft of loyalty…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent security alert after adding three critical vulnerabilities to its…
A sophisticated scanning campaign has escalated dramatically, with threat intelligence firm GreyNoise detecting over 30,000 unique IP addresses simultaneously probing Microsoft Remote…
Scammers are using Google Ads to pose as Tesla in an elaborate cybercrime campaign that aims to obtain illicit preorders…
Google Classroom, a popular educational platform, has been exploited by threat actors to launch a major phishing campaign in a…
FortiGuard Labs has uncovered a sophisticated malware campaign targeting critical infrastructure devices from multiple vendors, with the “Gayfemboy” malware strain…