Category: GBHackers
Industrial technology company Colt has confirmed that a recent ransomware attack on its business support systems resulted in the theft…
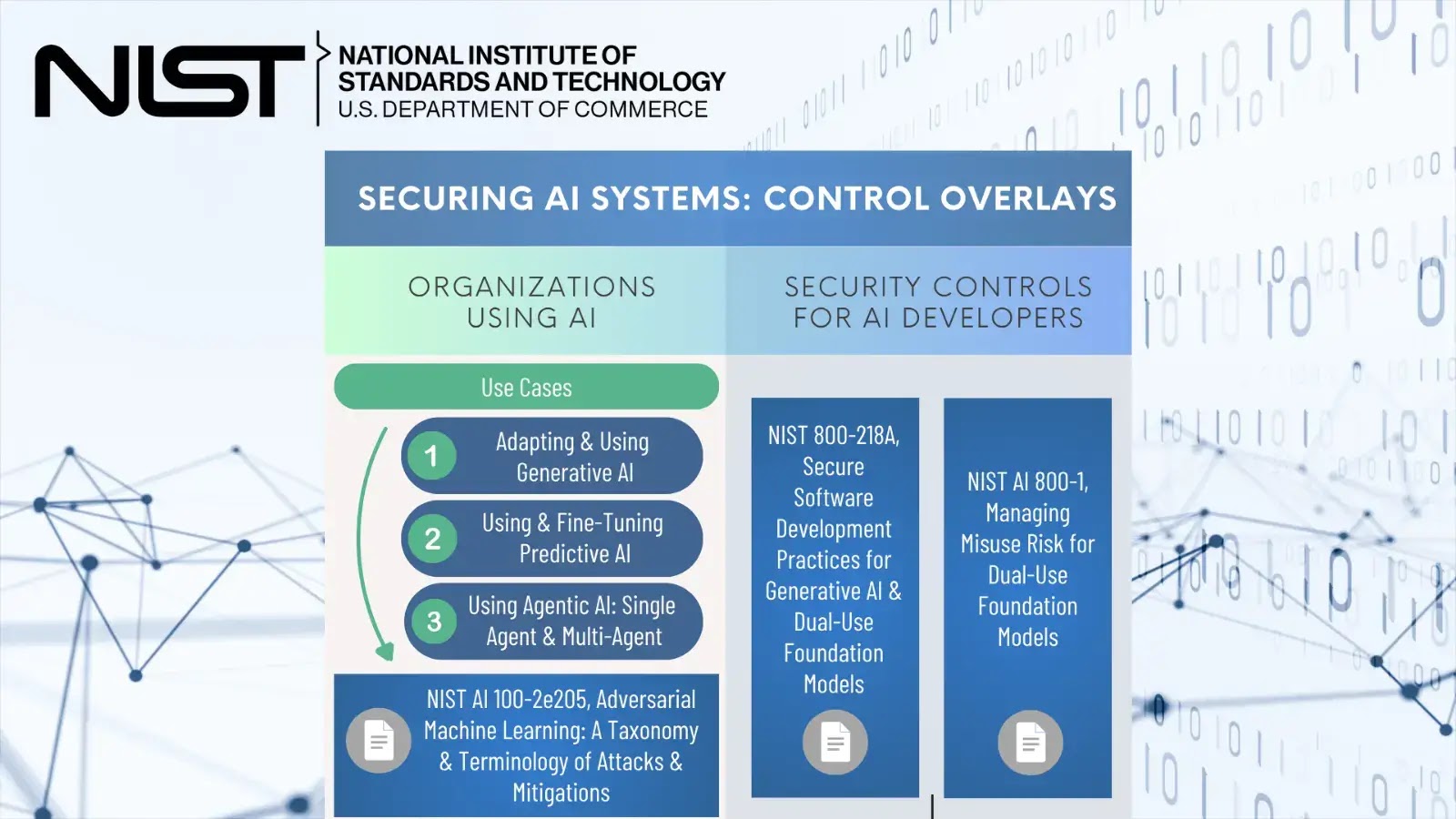
The National Institute of Standards and Technology (NIST) has unveiled a comprehensive initiative to address the growing cybersecurity challenges associated…
A critical security vulnerability has been discovered in the widely-used sha.js npm package, exposing millions of applications to sophisticated hash…
A critical vulnerability in Docker Desktop for Windows has been discovered that allows any container to achieve full host system…
Security researchers from Adversa AI have uncovered a critical vulnerability in ChatGPT-5 and other major AI systems that allows attackers…
Cybersecurity researchers have uncovered an ongoing campaign where threat actors exploit the critical CVE-2024-36401 vulnerability in GeoServer, a geospatial database,…
Quishing, a powerful form of phishing that uses malicious hyperlinks contained in QR codes to expose user credentials and sensitive…
Researchers have discovered a complex campaign using trojanized software that uses authentic code-signing certificates to avoid detection and turn compromised…
Adversaries are using AI-powered website builders to expedite the development of harmful infrastructure in a quickly changing threat landscape, hence…
The Warlock ransomware group has intensified its operations by targeting unpatched on-premises Microsoft SharePoint servers, leveraging critical vulnerabilities to achieve…
An Malicious actors are using reliable internet resources, such as the Internet Archive, more frequently to disseminate clandestine malware components…
Cyber spies associated with the threat actor group Paper Werewolf have demonstrated advanced capabilities in bypassing email security filters by…