Category: GBHackers
The cryptocurrency ecosystem is experiencing heightened scrutiny from both regulatory authorities and criminal organizations, as Google Play implements stringent publishing…
The Qilin ransomware group has solidified its position as the most active threat actor in July 2025, marking its third…
Cybersecurity firms are reporting a disturbing new trend in 2025: artificial intelligence assistants designed to boost productivity are inadvertently becoming…
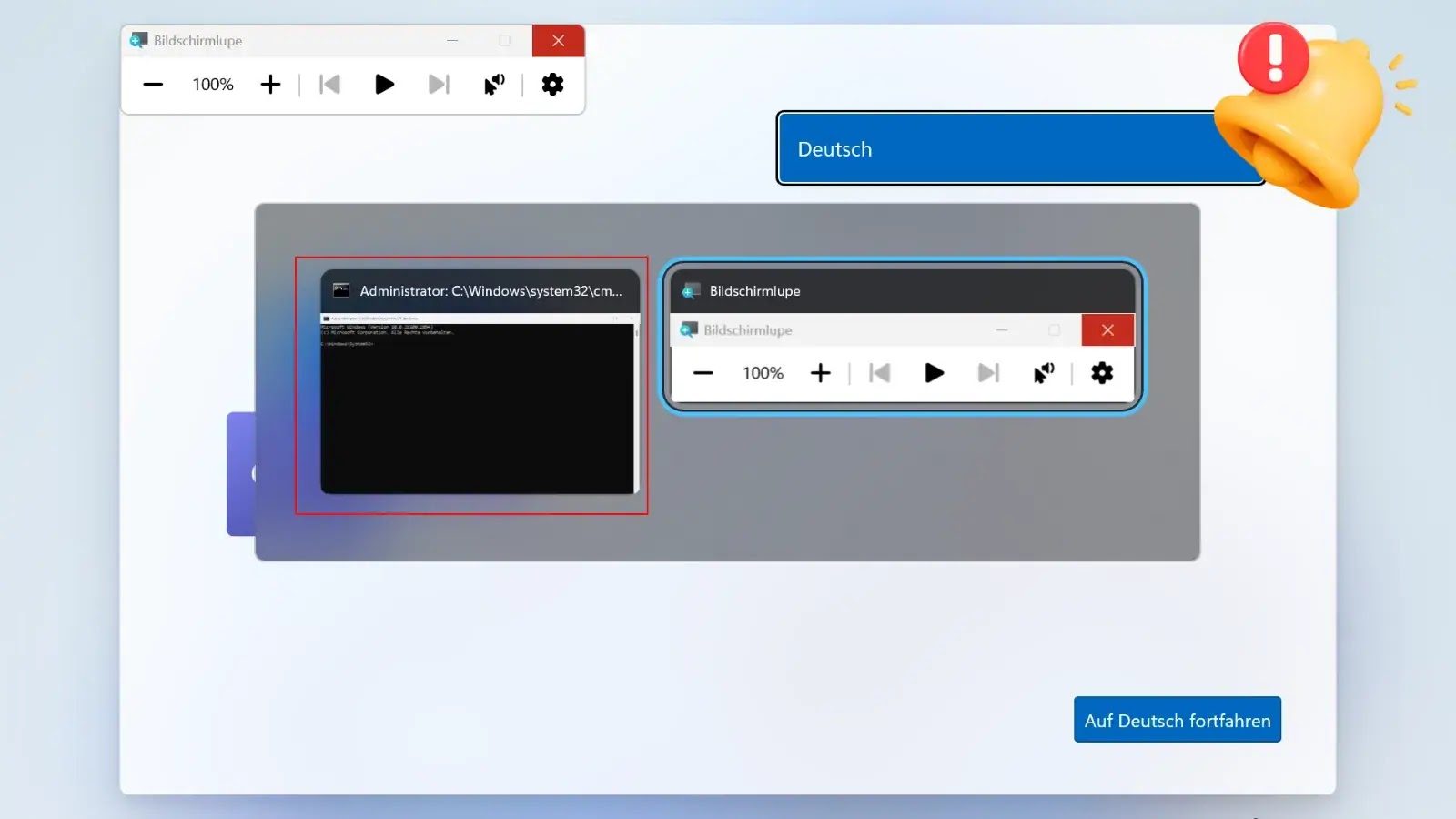
A newly documented vulnerability in Windows’ Out-of-Box-Experience (OOBE) allows users to bypass security restrictions and gain full administrative access to…
Intezer’s Research Team has uncovered a new, low-detection variant of the FireWood backdoor, a sophisticated Linux-based remote access trojan (RAT)…
The Cybersecurity and Infrastructure Security Agency (CISA), in partnership with eight other national cyber agencies, has released a comprehensive “Foundations…
Microsoft has disclosed a critical security vulnerability in its Internet Information Services (IIS) Web Deploy tool that could allow attackers…
Trustwave SpiderLabs researchers have uncovered a sophisticated EncryptHub campaign that ingeniously abuses the Brave Support platform to deliver malicious payloads,…
Splunk has released a comprehensive defender’s guide aimed at helping cybersecurity teams detect and prevent ransomware attacks targeting ESXi infrastructure…
Android privilege escalation has been transformed by rooting frameworks such as KernelSU, APatch, and SKRoot, which use advanced kernel patching…
The AhnLab Security Intelligence Center (ASEC) has uncovered fresh instances of proxyware distribution by threat actors leveraging deceptive advertising on…
A severe security vulnerability has been discovered in a popular WordPress plugin used by over 70,000 websites worldwide, potentially exposing…