Category: GBHackers
A member of North Korea’s notorious Kimsuky espionage group has experienced a significant data breach after insiders leaked hundreds of…
Reddit has announced it will restrict the Internet Archive’s Wayback Machine from accessing most of its content, citing concerns about…
Security researcher Eaton Zveare unveiled a critical flaw in a major automaker’s dealer portal that could allow attackers to unlock…
A sophisticated ransomware attack by a previously unknown cybercriminal group called “DarkBit” has targeted a major organization’s VMware ESXi infrastructure,…
A critical security vulnerability has been discovered in Apache bRPC that allows attackers to remotely crash services through network-based denial…
Threat actors have begun a geographically focused campaign against Israeli infrastructure and corporate entities in a sophisticated cyber incursion discovered…
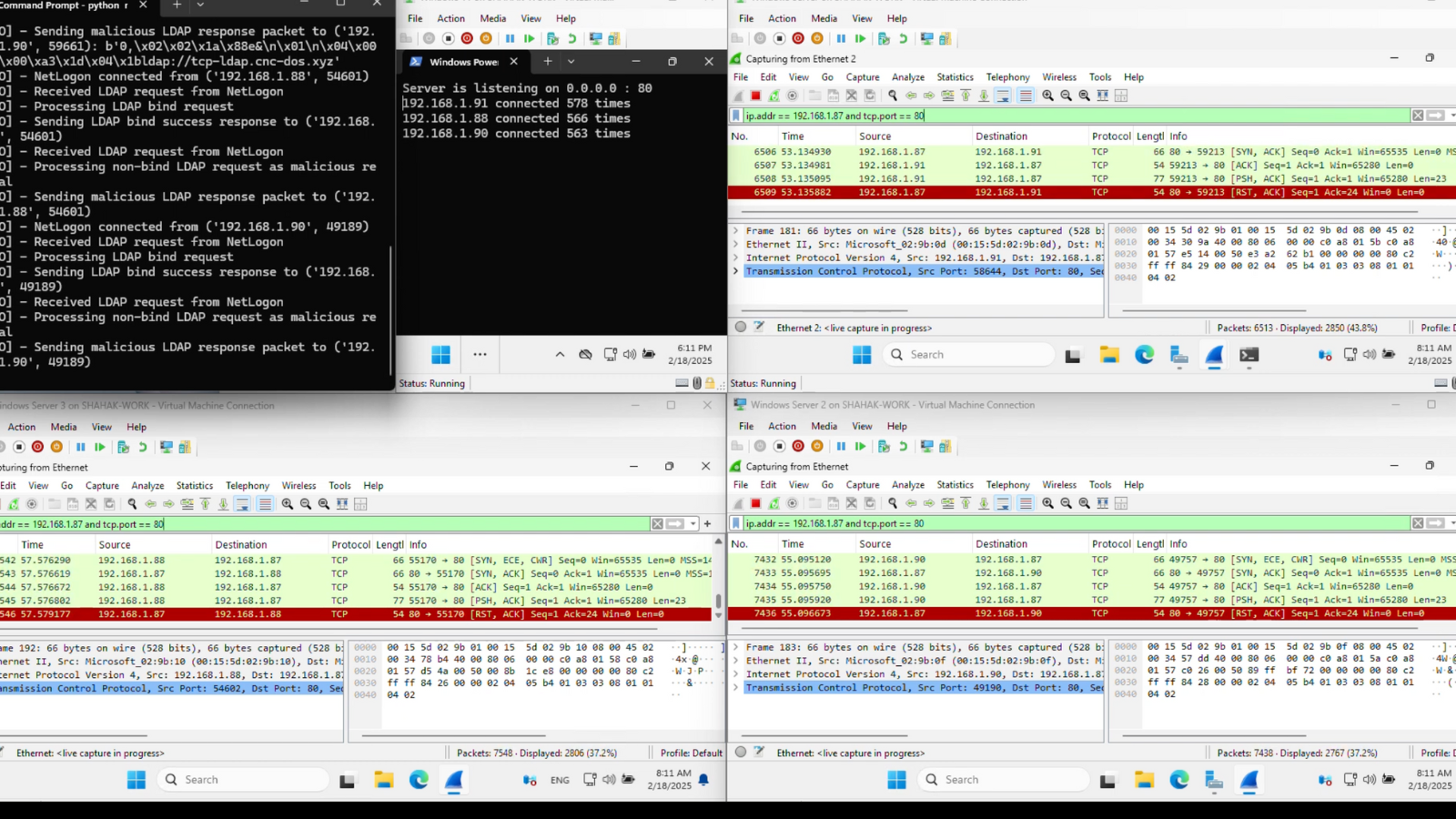
Security researchers have uncovered a “zero-click” denial-of-service chain that can silently turn thousands of Microsoft Windows Domain Controllers (DCs) into…
United States Attorney for the Southern District of New York, Jay Clayton, alongside FBI Assistant Director in Charge Christopher G….
New Heimdal study reveals how tool sprawl creates blind spots, with over half of providers experiencing daily or weekly burnout….
A severe vulnerability, designated CVE-2025-32433 with a CVSS score of 10.0, has been identified in the Secure Shell (SSH) daemon…
UAC-0099, a persistent threat actor active since at least 2022, has conducted sophisticated cyber-espionage operations against Ukrainian government, military, and…
Meta has introduced a transformative update to Instagram, evolving the platform from a simple photo-sharing service into an always-on real-time…