Category: GBHackers
IBM X-Force has uncovered CastleBot, a nascent malware framework operating as a Malware-as-a-Service (MaaS) platform, enabling cybercriminals to deploy a…
GitLab’s Vulnerability Research team has uncovered a highly sophisticated cryptocurrency theft campaign exploiting typosquatted Python packages on the Python Package…
Kaspersky researchers have uncovered a widespread campaign involving the Efimer malicious script, a sophisticated Trojan-dropper primarily aimed at stealing cryptocurrency….
Researchers at Gen have uncovered a vast network of over 5,000 fraudulent online pharmacy domains operated by a single cybercriminal…
Unit 42 researchers have identified a significant evolution in the distribution tactics of DarkCloud Stealer, an infostealer malware first observed…
A new variant of the DarkCloud information-stealer malware has been observed targeting Microsoft Windows systems, primarily affecting Windows users by…
Claroty’s Team82 research unit has unveiled four vulnerabilities affecting Axis Communications’ widely deployed video surveillance ecosystem, potentially endangering thousands of…
The Python Package Index (PyPI) has announced new restrictions aimed at mitigating ZIP parser confusion attacks that could exploit discrepancies…
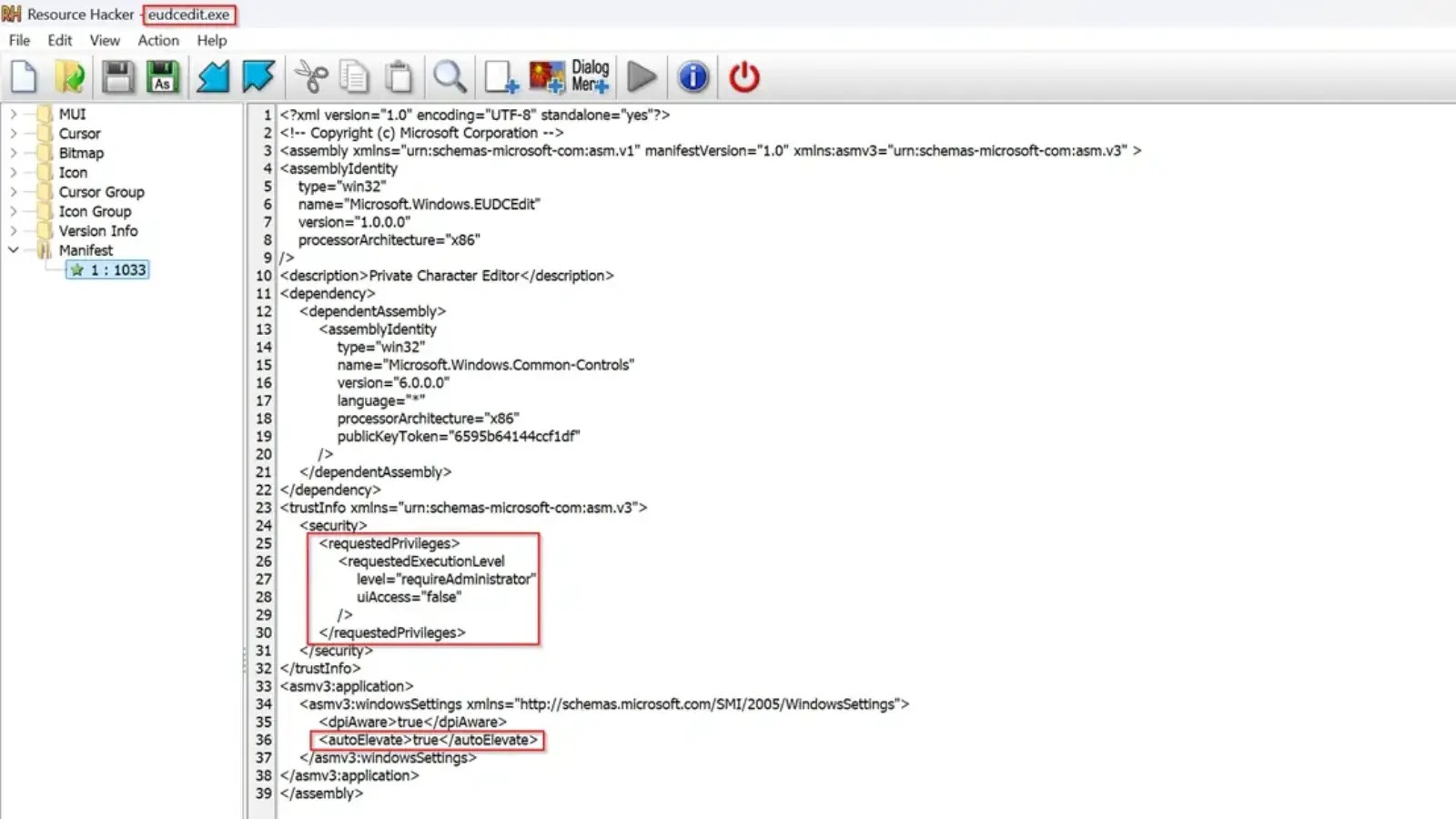
Cybersecurity researchers have uncovered a new technique that allows attackers to bypass Windows User Account Control (UAC) protections by exploiting…
Cisco Talos’ Vulnerability Discovery & Research team has disclosed a total of 12 critical security vulnerabilities across three popular software…
VexTrio, a sophisticated threat actor known for operating a massive traffic distribution system (TDS), has expanded its malicious activities by…
Columbia University disclosed a significant cybersecurity incident that compromised personal and financial information of nearly 870,000 individuals, making it one…