Category: GBHackers
The threat actor group dubbed GreedyBear has orchestrated an industrial-scale operation blending malicious browser extensions, executable malware, and phishing infrastructure…
OpenAI has officially launched ChatGPT-5, marking a significant leap forward in artificial intelligence technology with a revolutionary unified system that…
The Cybersecurity and Infrastructure Security Agency (CISA) has released ten industrial control systems (ICS) advisories on August 7, 2025, highlighting…
Security researchers have disclosed a critical vulnerability in Amazon Elastic Container Service (ECS) that allows malicious containers to steal AWS…
Federal law enforcement agencies have successfully dismantled the critical infrastructure of BlackSuit ransomware, a sophisticated cybercriminal operation that has compromised…
Socket’s Threat Research Team has identified eleven malicious Go packages distributed via GitHub, with ten remaining active on the Go…
Socket’s Threat Research Team has exposed a persistent campaign involving over 60 malicious RubyGems packages that masquerade as automation tools…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued Emergency Directive 25-02 on August 7, 2025, requiring federal agencies to…
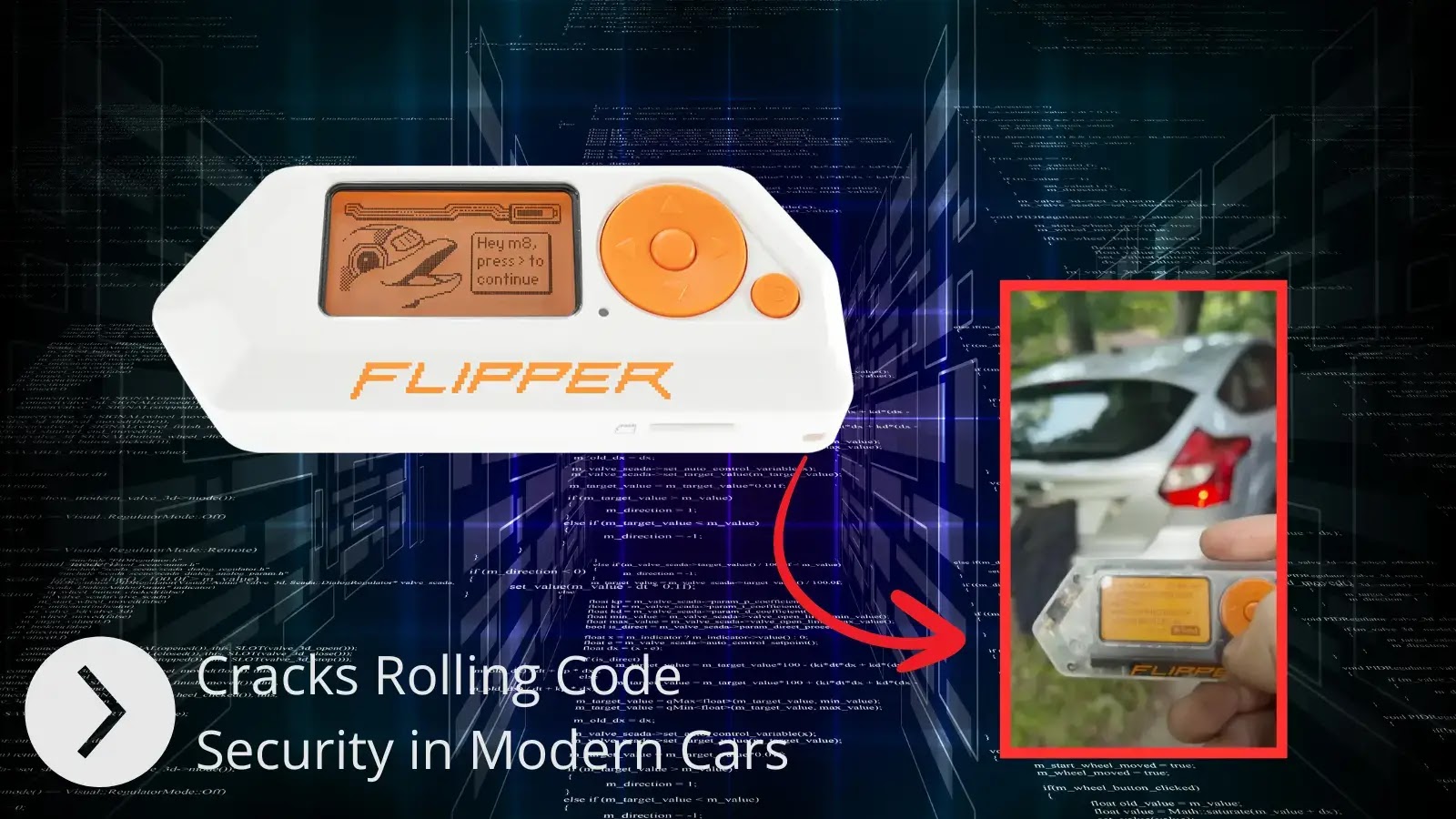
Security researchers have discovered alarming new firmware for the popular Flipper Zero device that can completely bypass the rolling code…
Security researchers have successfully demonstrated a sophisticated exploit of the Retbleed vulnerability, a critical CPU security flaw that allows attackers to…
Researchers at Cyata have disclosed nine previously unknown zero-day vulnerabilities in HashiCorp Vault, a widely adopted open-source secrets management platform,…
Elite cybercriminals prefer LotL attacks because they’re incredibly hard to spot. Instead of deploying obvious malware, attackers use the same…