Category: GBHackers
Cybersecurity landscapes are undergoing a paradigm shift as threat actors increasingly deploy agentic AI systems to orchestrate sophisticated social engineering…
A significant milestone for cybersecurity experts is the disclosure of specific tactics, methods, and procedures (TTPs) used by Mustang Panda,…
Securden Unified PAM is a comprehensive privileged access management platform that is used to store, manage, and monitor credentials across…
Zimperium’s zLabs research team has identified a sophisticated new variant of the Hook Android banking trojan, marking a significant escalation…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent alert regarding a critical vulnerability in Git (CVE-2025-48384) that…
Google has announced that all Android apps installed on approved devices will soon need to be able to be traced…
CYFIRMA researchers have uncovered a campaign they have codenamed “OneFlip”, an operation that demonstrates how a single-bit modification inside a…
A proof-of-concept exploit for a high-severity Google Chrome zero-day vulnerability has been published publicly, less than three months after the…
Cybersecurity incidents increasingly exploit human vulnerabilities, including those of privileged users, as demonstrated in recent compromises involving trojanized versions of…
Microsoft today announced the public preview of a new VM Conversion extension for Windows Admin Center, enabling IT administrators to migrate virtual…
Threat actors are increasingly refining Android droppers to circumvent enhanced security measures, extending their utility beyond sophisticated banking trojans to…
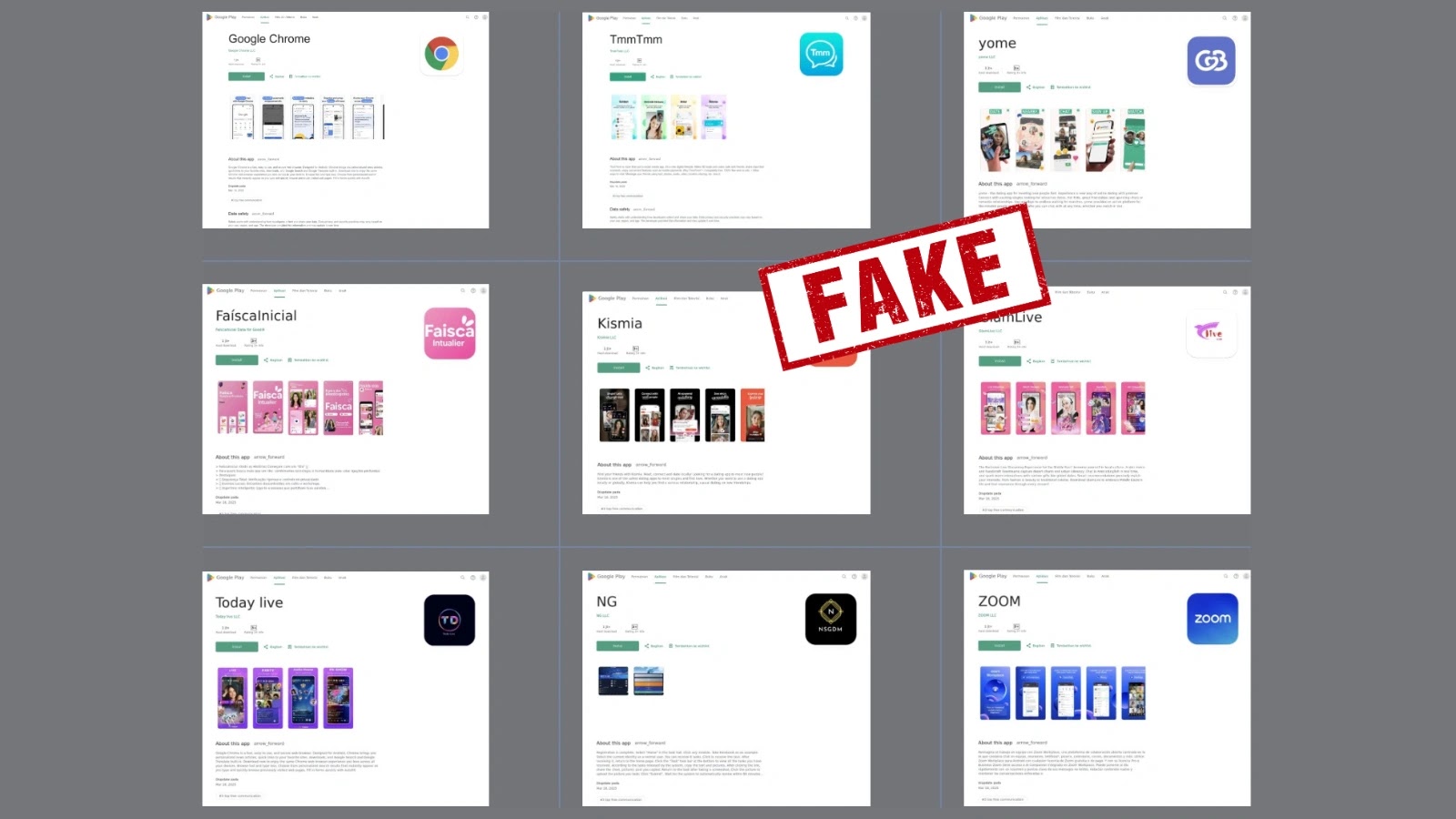
Cybersecurity researchers have identified a resurgence of SpyNote malware campaigns targeting Android users through sophisticated fake Google Play Store websites….