Category: GBHackers
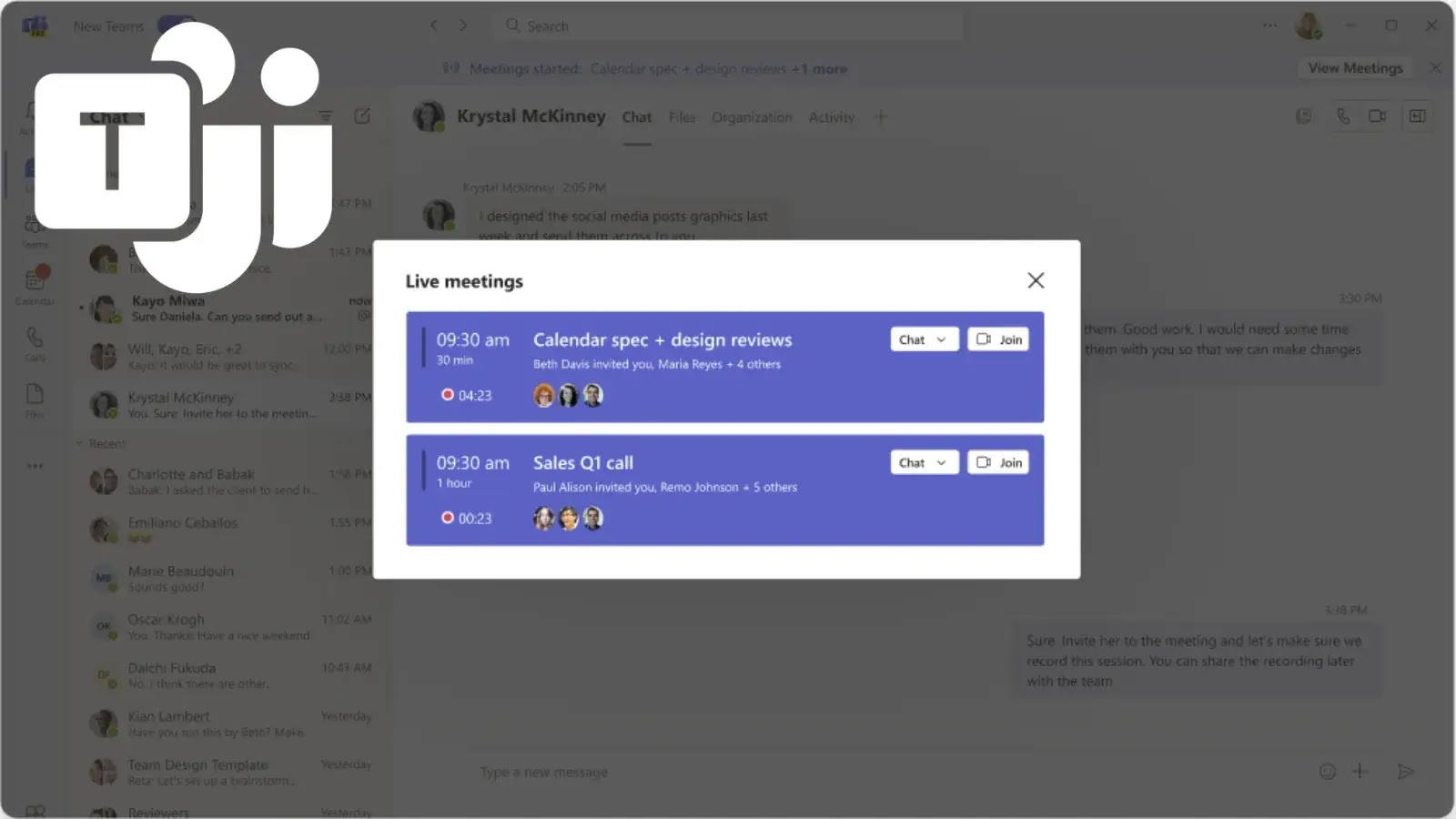
Microsoft Teams is rolling out a new meeting join banner designed to streamline the meeting experience for users who have…
Python developers are being warned about a sophisticated phishing campaign targeting users of the Python Package Index (PyPI) through fraudulent…
Linux creator Linus Torvalds announced the release of Linux kernel version 6.16 on July 27, 2025, marking the end of…
Outpost24’s threat intelligence researchers have uncovered the operations of Lionishackers, a financially motivated cyber threat actor specializing in the exfiltration…
Microsoft Threat Intelligence has uncovered a critical macOS vulnerability that enables attackers to bypass Apple’s Transparency, Consent, and Control (TCC)…
Cybersecurity experts have pointed to an increase in sophisticated threat actor activity following the July 27 2025 Belgian Grand Prix…
The Cybersecurity and Infrastructure Security Agency (CISA) has added a critical PaperCut vulnerability to its Known Exploited Vulnerabilities (KEV) catalog,…
GitHub experienced a significant global outage on July 28-29, 2025, disrupting core services used by millions of developers worldwide. The…
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical security alert regarding severe vulnerabilities in Cisco’s Identity Services…
Russia’s flagship carrier Aeroflot is reeling from a devastating cyberattack that pro-Ukraine hacking groups claim wiped approximately 7,000 servers and…
Threat actors have been using trojanized versions of well-known IT tools like PuTTY and WinSCP to spread the Oyster backdoor,…
ArmouryLoader and other malicious code loaders have become essential tools for introducing Trojan-type payloads into hacked systems in the ever-changing…