Category: GBHackers
Christina Marie Chapman, a 50-year-old Arizona woman, has been sentenced to 102 months in prison for her role in an…
AhnLab’s Threat Intelligence Platform (TIP) has been instrumental in monitoring ransomware activities across dark web forums and marketplaces. Through its…
Wiz Research has uncovered an active cryptomining campaign, dubbed Soco404, that exploits misconfigurations in PostgreSQL databases and other cloud services…
CloudSEK’s TRIAD team uncovered an active development site deploying Clickfix-themed malware linked to the Epsilon Red ransomware. This variant deviates…
A malicious Android application has been uncovered, impersonating legitimate Indian banking apps to orchestrate credential theft, surveillance, and unauthorized financial…
Cybersecurity firm Sygnia has been tracking and mitigating a sophisticated espionage operation dubbed Fire Ant, which zeroes in on virtualization…
Cybercriminals are increasingly using Google Forms to plan cryptocurrency theft in a sophisticated evolution of phishing assaults, taking advantage of…
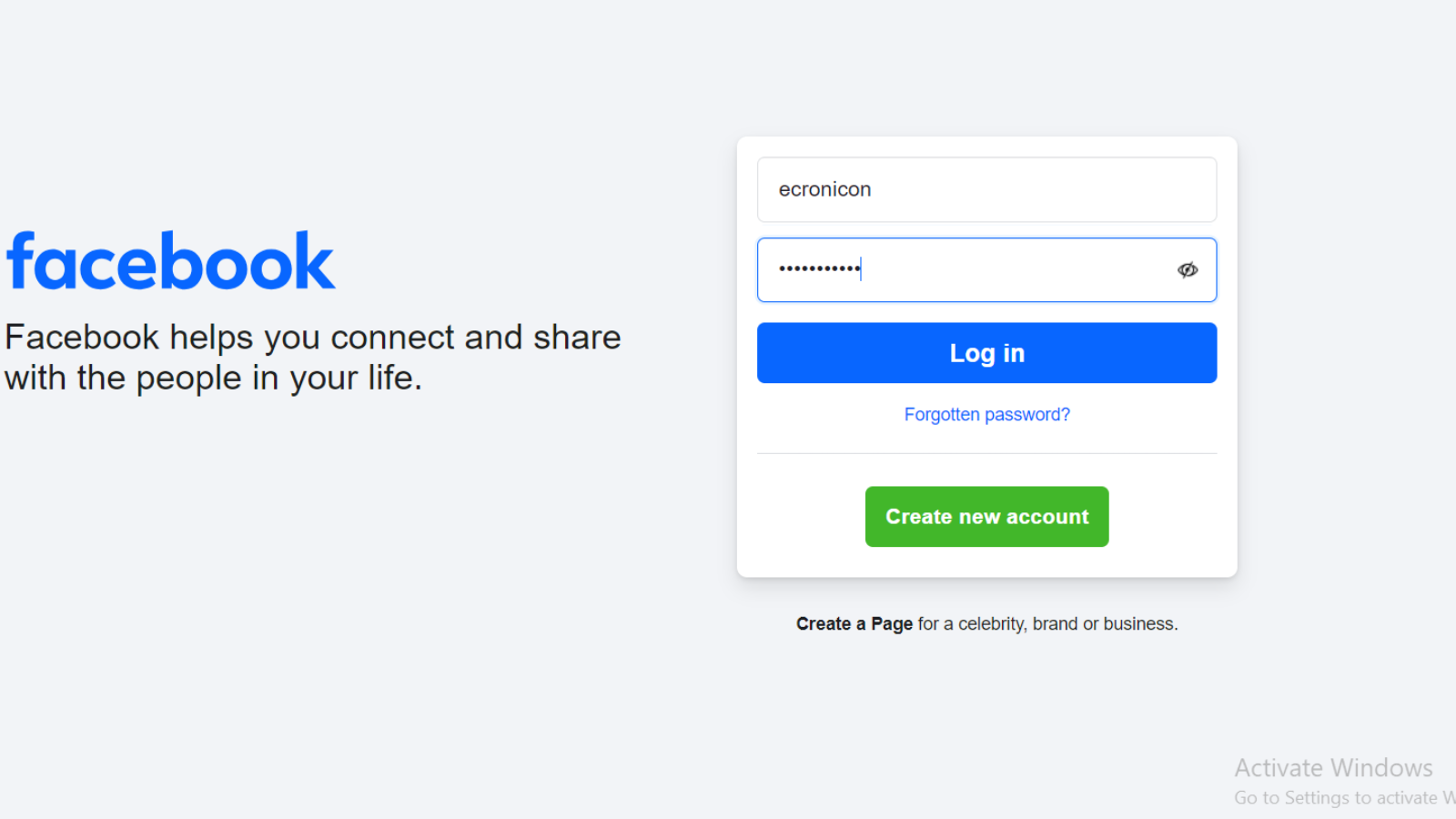
Cybercriminals are using a variety of dishonest tactics in a sophisticated phishing effort aimed at Facebook users in order to…
The United States government announced coordinated actions across multiple departments today, offering rewards totaling up to $15 million for information…
Security researchers have uncovered critical vulnerabilities in VMware Tools’ Guest Authentication Service (VGAuth) that allow attackers to escalate privileges from…
Cybersecurity researchers at Nozomi Networks Labs have discovered 13 critical vulnerabilities in Tridium’s widely-used Niagara Framework, potentially exposing sensitive network…
The Acronis Threat Research Unit (TRU) has uncovered a sophisticated malware campaign deploying infostealers like Leet Stealer, its modified variant…