Category: GBHackers
Attackers are increasingly leveraging the ClickFix social engineering technique to distribute potent malware families, including NetSupport RAT, Latrodectus, and Lumma…
Threat actors have been actively exploiting vulnerabilities in Ivanti Connect Secure, specifically CVE-2025-0282 and CVE-2025-22457, to deploy advanced malware, including…
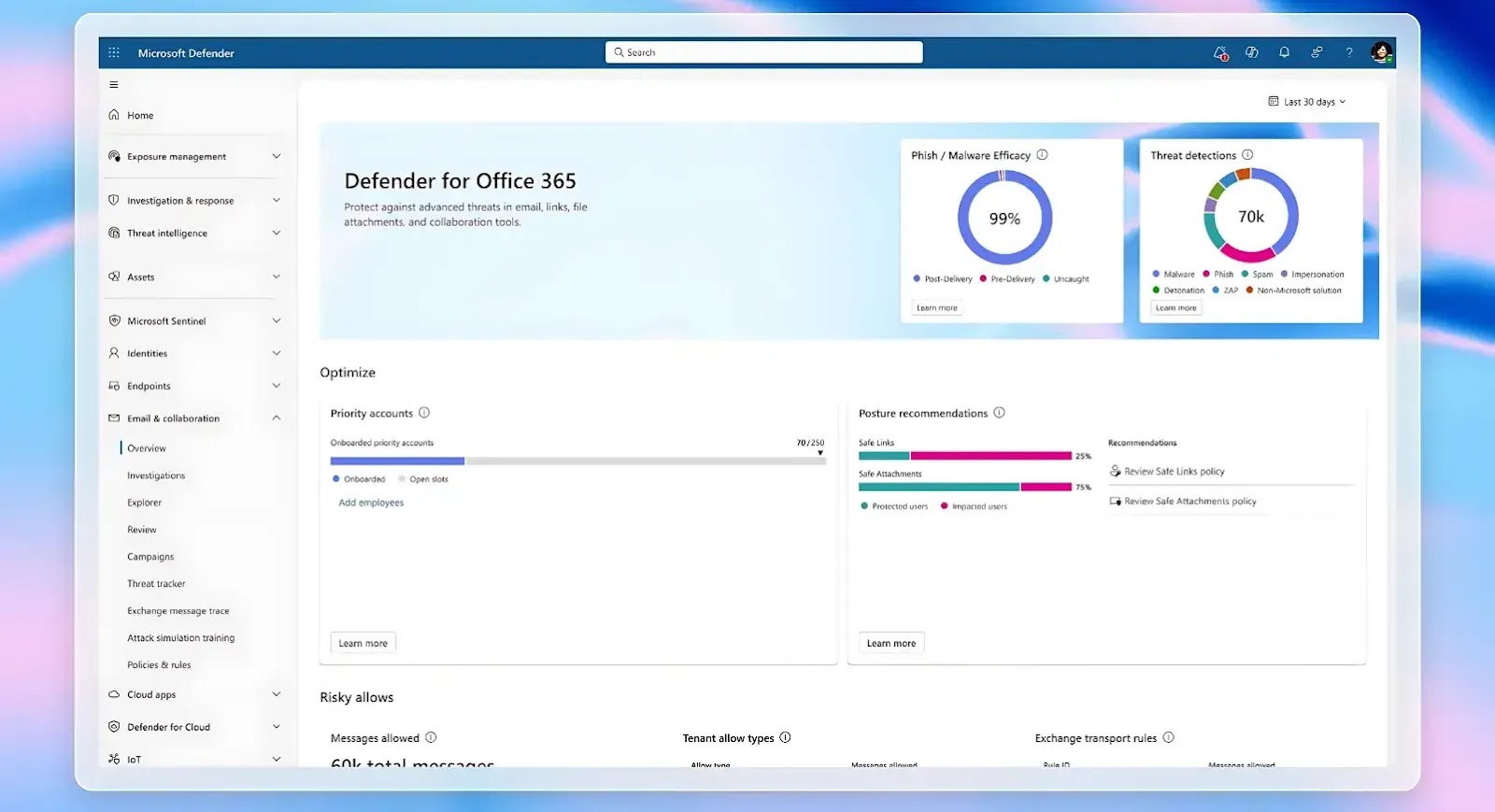
Microsoft has announced significant transparency improvements for its email security platform, introducing a new customer-facing dashboard that provides detailed visibility…
Grafana Labs has released critical security patches addressing two significant vulnerabilities that could enable attackers to redirect users to malicious…
Google has initiated legal proceedings against the operators of BadBox 2.0, identified as the largest botnet comprising internet-connected televisions and…
Sophos has disclosed three critical security vulnerabilities in its Intercept X for Windows endpoint security solution that could allow attackers…
Researchers at Cyble Research and Intelligence Labs (CRIL) have uncovered an ongoing quishing campaign dubbed “Scanception,” which exploits QR code-based…
A critical security vulnerability has been discovered in Ubiquiti’s UniFi Access devices that could allow malicious actors to inject and…
The Internet Systems Consortium (ISC) has disclosed two critical security vulnerabilities in BIND 9, one of the most widely used…
A critical vulnerability in TeleMessageTM SGNL, an enterprise messaging platform modeled after Signal, is being actively exploited by threat actors…
Cybersecurity researchers have uncovered a sophisticated technique where threat actors are exploiting DNS infrastructure to covertly store and distribute malware,…
Cybersecurity researchers at Seqrite Labs have identified a sophisticated espionage group designated as UNG0002 (Unknown Group 0002) that has been…