Category: GBHackers
Proofpoint Threat Research has identified a sophisticated multi-pronged cyberespionage campaign targeting Taiwan’s semiconductor industry between March and June 2025. Three…
Palo Alto, California, July 17th, 2025, CyberNewsWire SquareX announced the official launch of The Browser Security Field Manual at Black…
FortiGuard Labs researchers have uncovered a sophisticated cryptomining campaign where the H2Miner botnet, active since late 2019, has expanded its…
A sophisticated cyberattack campaign has emerged targeting organizations through Microsoft Teams impersonation, delivering the updated Matanbuchus 3.0 malware loader that…
A Ukrainian woman who survived a catastrophic cluster munition attack in 2014 continues to navigate the complex aftermath of severe…
Cybersecurity researchers at Lookout Threat Lab have uncovered a sophisticated mobile forensics application called Massistant, deployed by Chinese law enforcement…
Security researchers have discovered over 4 million vulnerable Internet hosts that can be weaponized for devastating new denial-of-service attacks, marking…
Cybersecurity researchers at Graphika have unveiled comprehensive findings on the operational dynamics of hacktivist organizations, revealing sophisticated attention-seeking behaviors and…
The UK’s Co-op retailer has disclosed that all 6.5 million of its members had their personal data stolen during a…
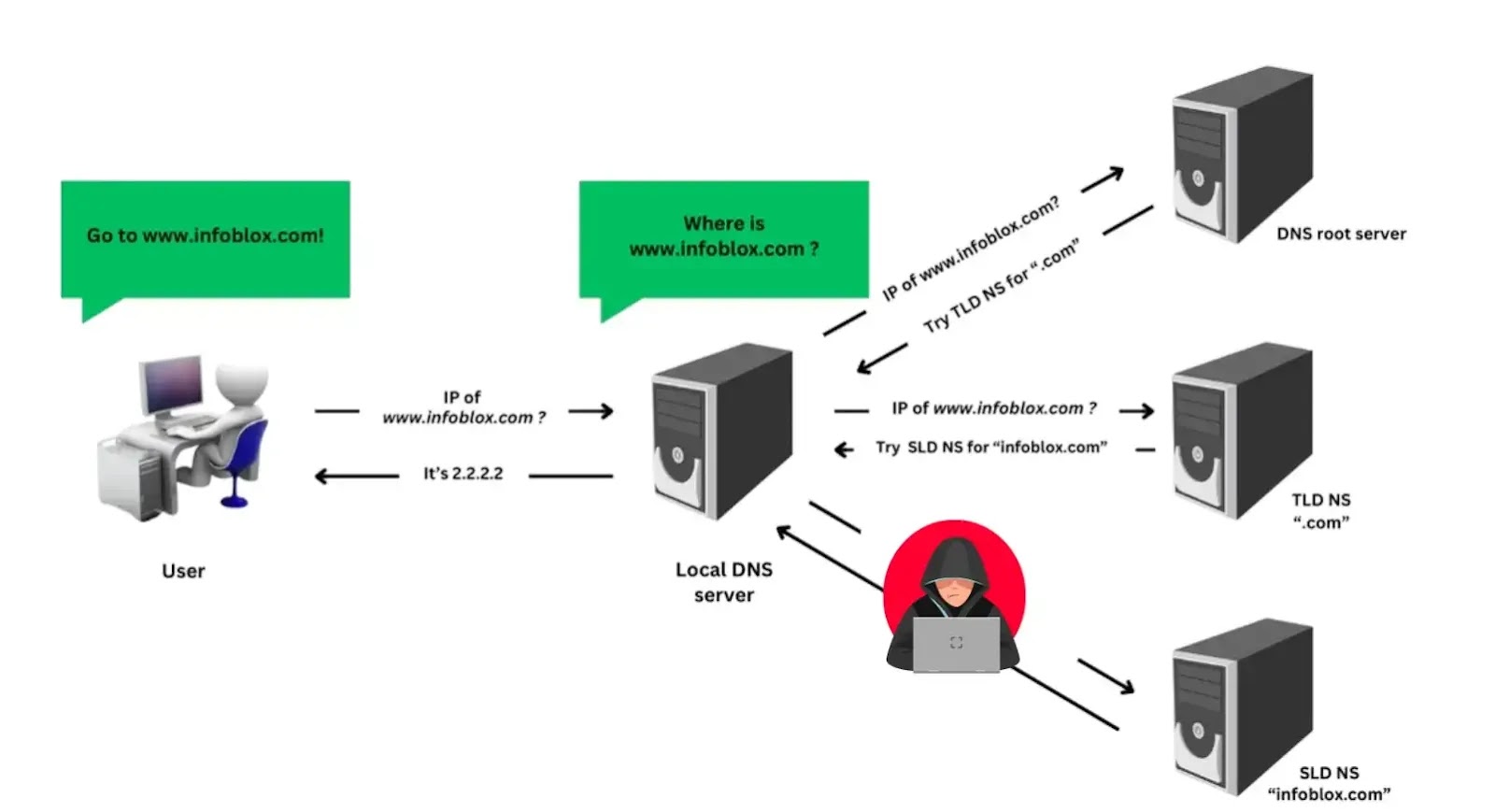
Cybercriminals are increasingly exploiting the Domain Name System (DNS) to bypass corporate security measures and steal sensitive data, according to…
Iranian state-backed Advanced Persistent Threat (APT) groups and their hacktivist allies have stepped up operations that could spark worldwide cyber…
Socket’s Threat Research Team has discovered a network of at least 28 malicious packages including protestware scripts, totaling approximately 2,000…