Category: GBHackers
Jeremiah Fowler, an ethical researcher, discovered an unsecured database with 245,949 entries totaling 286.9 GB in a huge cybersecurity issue….
The Cybersecurity and Infrastructure Security Agency (CISA) has issued a critical alert regarding active exploitation of a newly discovered vulnerability…
Security researchers have discovered two critical vulnerabilities in RapidFire Tools Network Detective, a widely-used network assessment and reporting tool developed…
A prominent Russian basketball player has been arrested in France on charges related to one of the most extensive ransomware…
Security researchers at Huntress have confirmed active exploitation of a critical remote code execution vulnerability in Wing FTP Server, designated…
Ingram Micro Holding Corporation (NYSE: INGM), a global leader in IT distribution and technology solutions, has announced that it has…
A critical vulnerability has been identified in the GSMA TS.48 Generic Test Profile versions 6.0 and earlier, which are widely…
AMD has issued a security bulletin, AMD-SB-7029, highlighting several transient scheduler attacks that exploit speculative execution timing in its processors,…
A critical arbitrary file deletion vulnerability has been discovered in the SureForms WordPress plugin, affecting over 200,000 active installations and…
A critical vulnerability in Juniper Networks’ Junos OS and Junos OS Evolved has been disclosed that permits unauthenticated adjacent attackers…
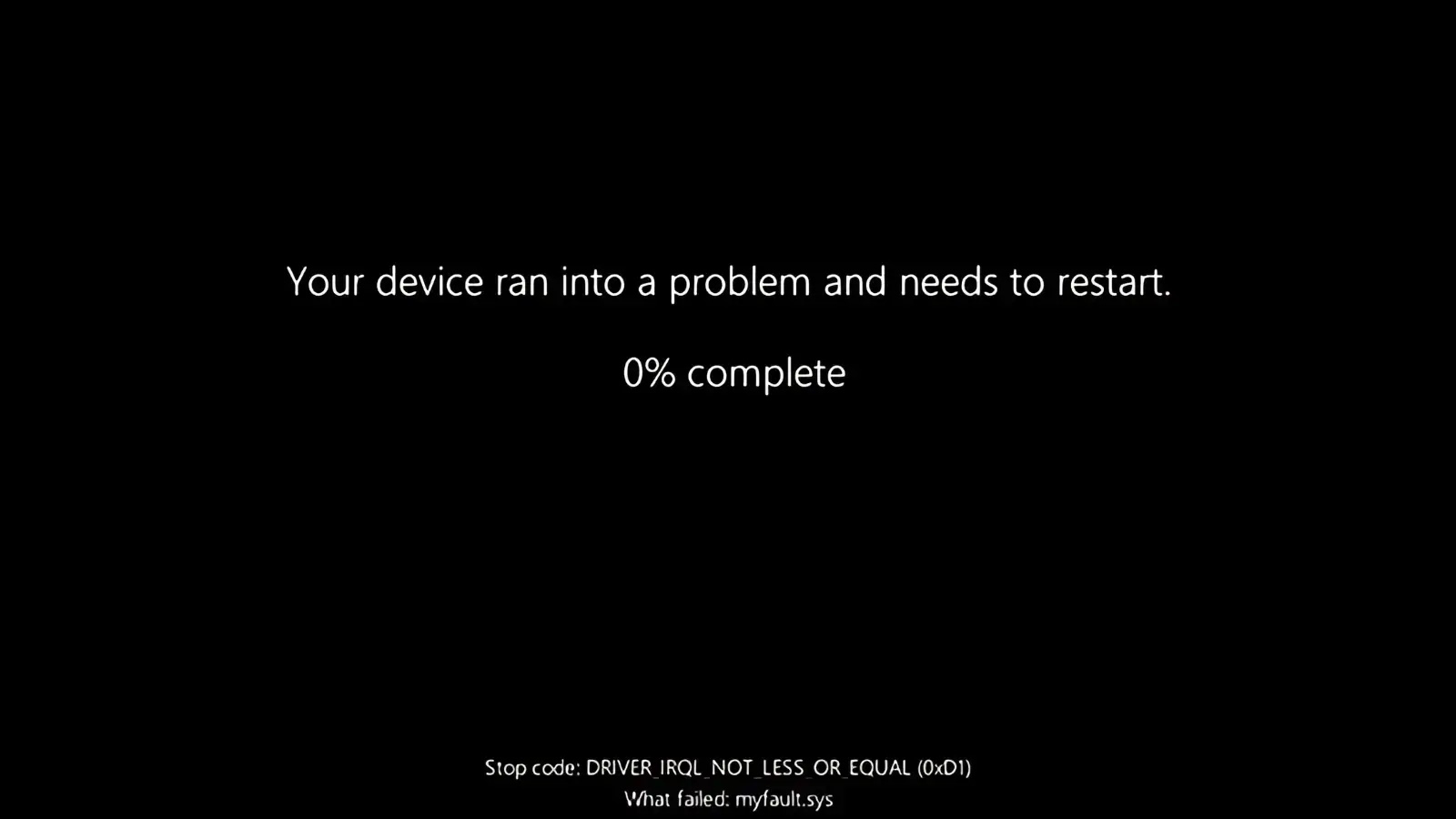
Microsoft has released Windows 11 Build 26100.4762 (KB5062660) to Insiders in the Release Preview Channel, introducing a redesigned restart interface…
Palo Alto Networks has disclosed a significant security vulnerability in its Autonomous Digital Experience Manager software that could allow attackers…