Category: GBHackers
GreyNoise has discovered an undiscovered version of a scraper botnet with more than 3,600 distinct IP addresses worldwide, which is…
Security researchers revealed the dangers of GitHub Device Code Phishing—a technique that leverages the OAuth 2.0 Device Authorization Grant flow….
A shocking security vulnerability in McDonald’s AI-powered hiring system has exposed the personal information of millions of job applicants, after…
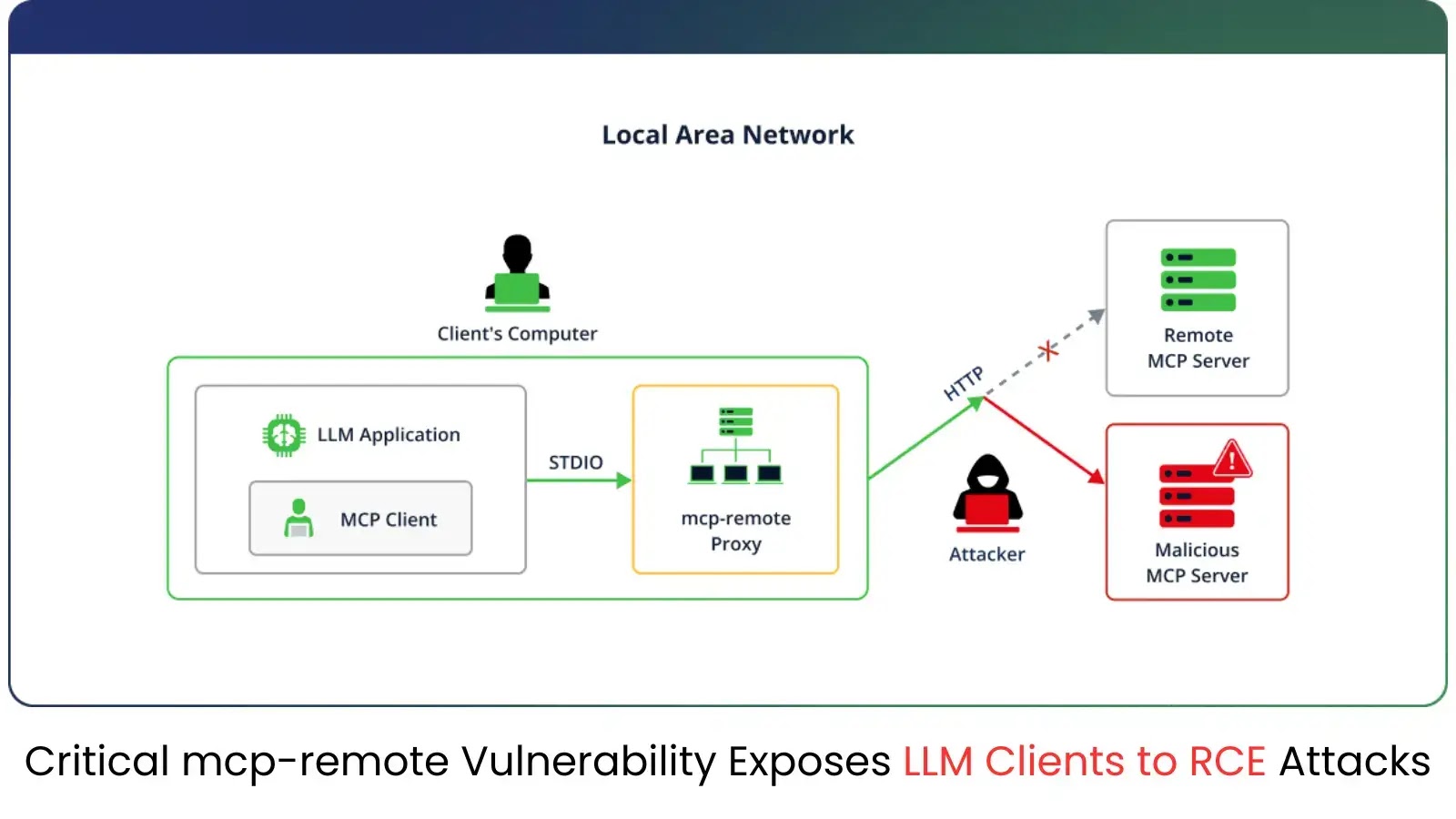
The JFrog Security Research team has discovered a critical security vulnerability in mcp-remote, a widely used tool that enables Large…
A critical security vulnerability in Microsoft 365’s PDF export functionality has been discovered and subsequently patched, highlighting significant risks to…
A sophisticated threat network called “Triad Nexus,” which operates through the FUNNULL content delivery network (CDN) to hide malicious infrastructure…
Microsoft has released critical security updates addressing a severe remote code execution vulnerability that could allow attackers to execute malicious…
Reflectiz, a leading cybersecurity company specializing in web exposure management, today announced a new integration with Datadog, Inc. (NASDAQ: DDOG),…
A sophisticated supply chain attack targeting cryptocurrency developers through the compromise of ETHcode, a legitimate Visual Studio Code extension with…
A sophisticated Trojan malware campaign has been targeting mobile device users across iOS and Android platforms since February 2024, with…
A new Android vulnerability called TapTrap that allows malicious apps to bypass the operating system’s permission system without requiring any…
A sophisticated campaign by an initial access broker (IAB) group exploiting leaked Machine Keys from ASP.NET websites to gain unauthorized…