Category: GBHackers
The Parrot Security team has released Parrot Security OS 6.4, a robust update featuring community-driven enhancements and contributions. As the…
Cybercriminals continue to use kernel-level malware as a preferred weapon against Windows systems amid a terrifying increase in cyberthreats. Operating…
Cybercriminals continue to use kernel-level malware as a preferred weapon against Windows systems amid a terrifying increase in cyberthreats. Operating…
Dr.Web Security Space for mobile devices reported that malware activity on Android devices increased significantly in the second quarter of…
“Slopsquatting” is a new supply-chain danger that has surfaced in the quickly changing field of AI-driven software development, presenting serious…
ESET researchers have uncovered a series of malicious tools deployed by BladedFeline, an Iran-aligned advanced persistent threat (APT) group, targeting…
Batavia, an unidentified spyware, has been using a sophisticated phishing operation to target Russian industrial organizations since July 2024. Kaspersky…
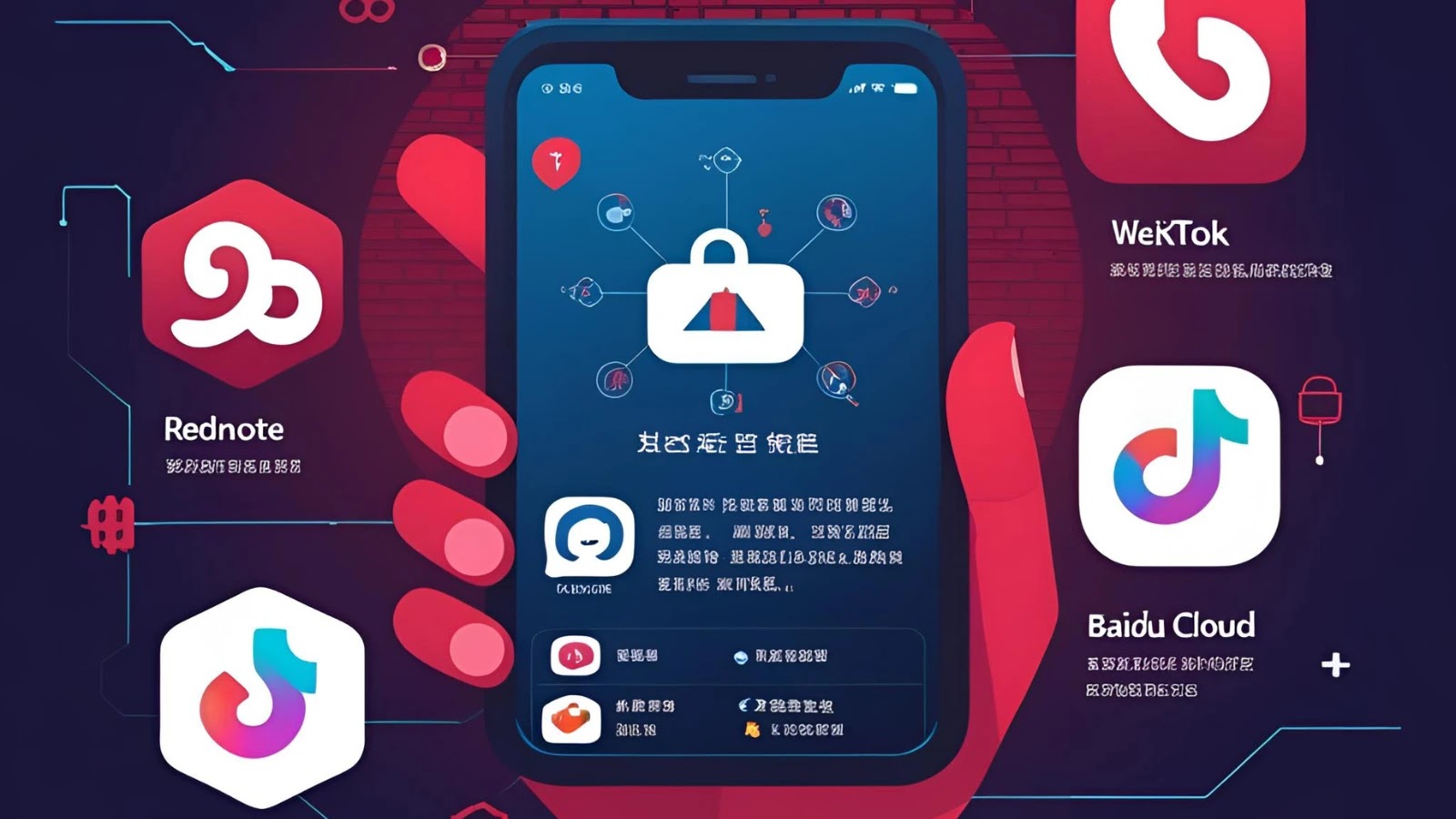
Taiwan’s National Security Bureau (NSB) has issued a stark warning about cybersecurity risks associated with several widely used China-developed mobile…
The AiLock ransomware organization, which Zscaler first discovered in March 2025, has become a powerful force in the ransomware-as-a-service (RaaS)…
The dark web forum DarkForums, which has been a site for data breaches and leaks since BreachForums was shut down…
The advanced attack campaigns of a top Advanced Persistent Threat (APT) group known as “NightEagle,” internally coded as APT-Q-95, were…
Ingram Micro Holding Corporation (NYSE: INGM), a global leader in technology distribution and supply chain solutions, has confirmed that it…